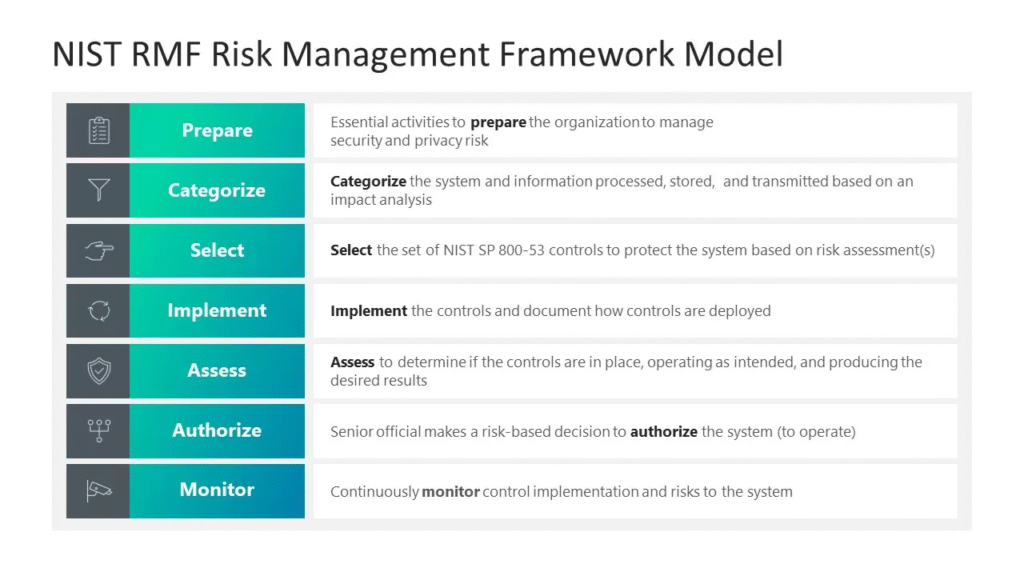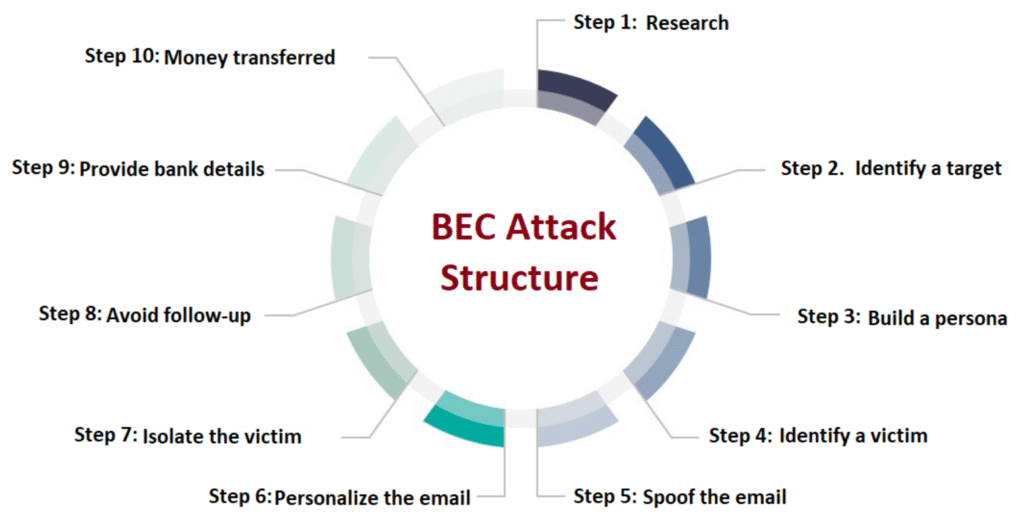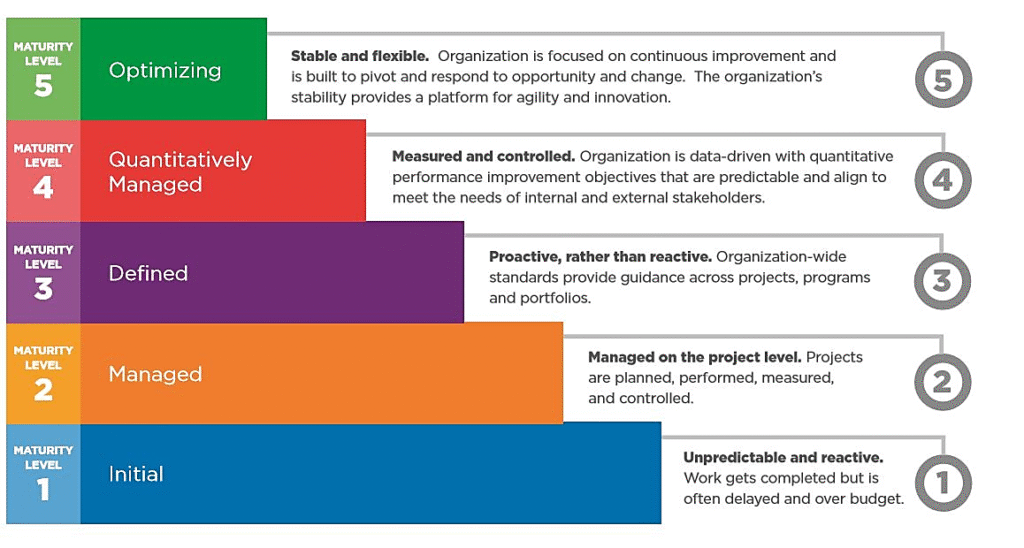
Reading Time: 4 minutesThis document provides a concise overview of the “Implementation Plan – SOC-CMM” research blueprint, synthesizing key insights for establishing, maturing, and optimizing Security Operations Center (SOC) capabilities. It highlights the core framework, implementation lifecycle, and critical areas for optimization across people, processes, technology, performance, and compliance.