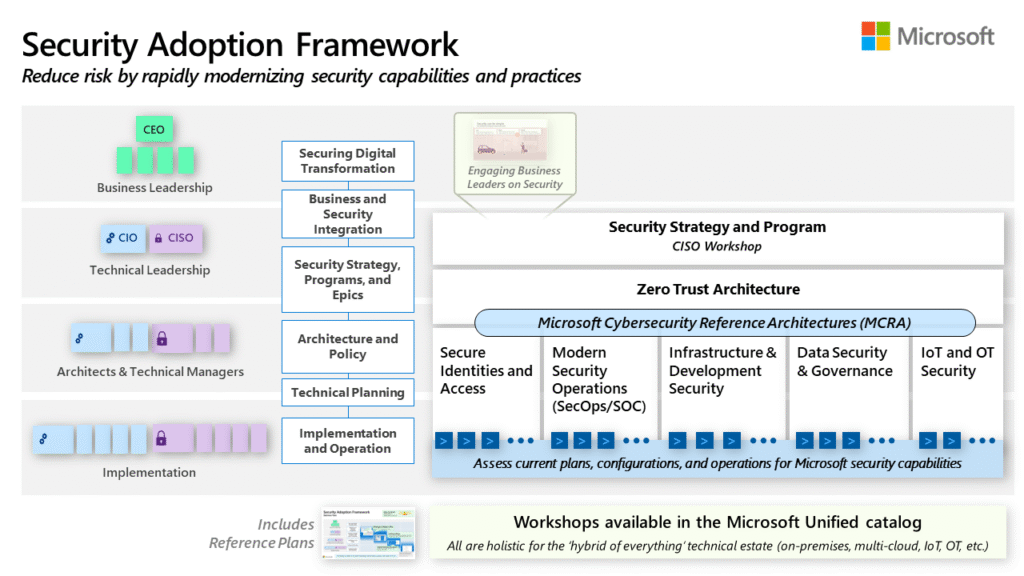
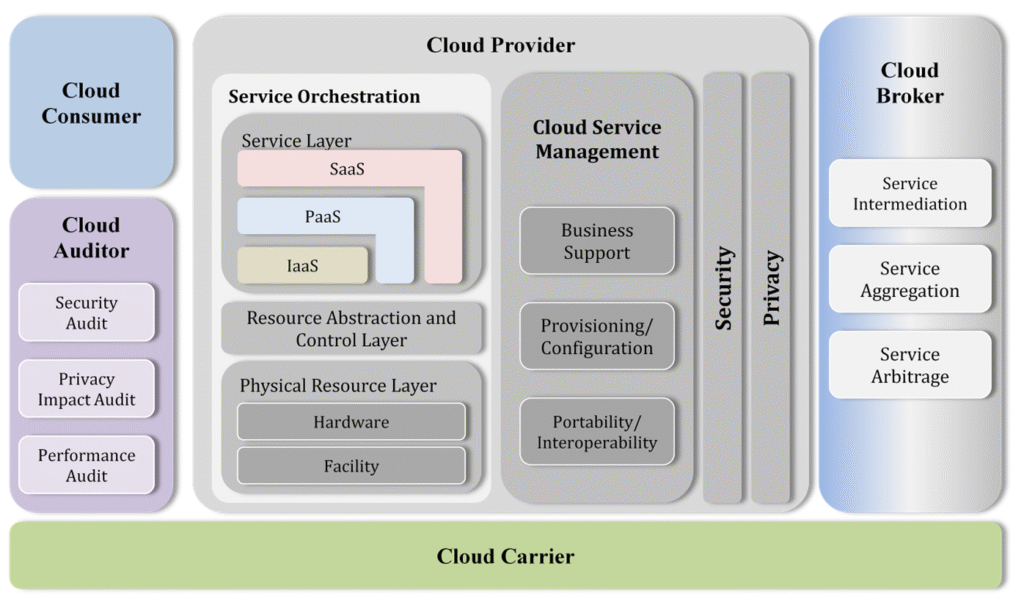
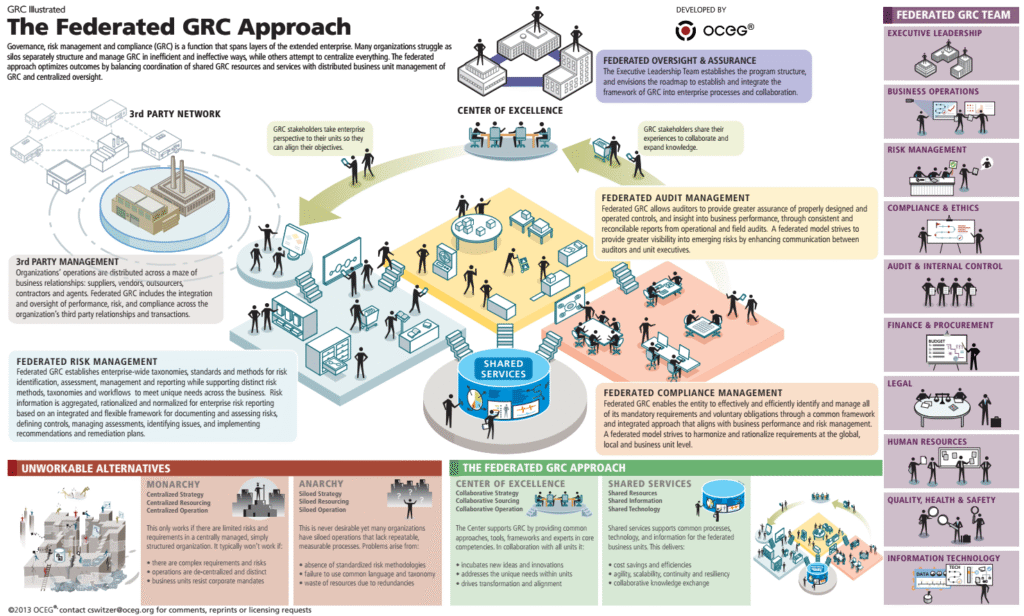
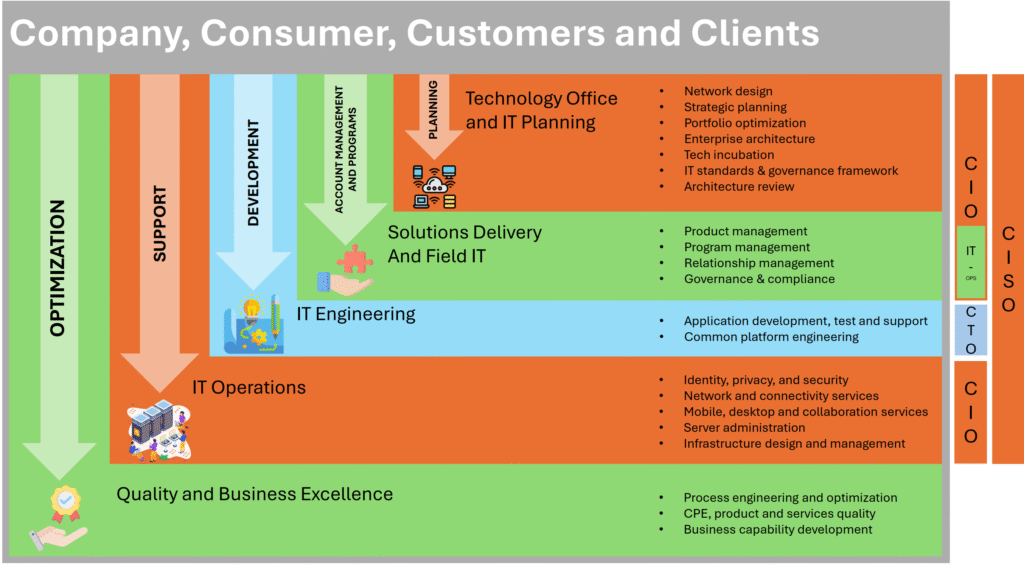
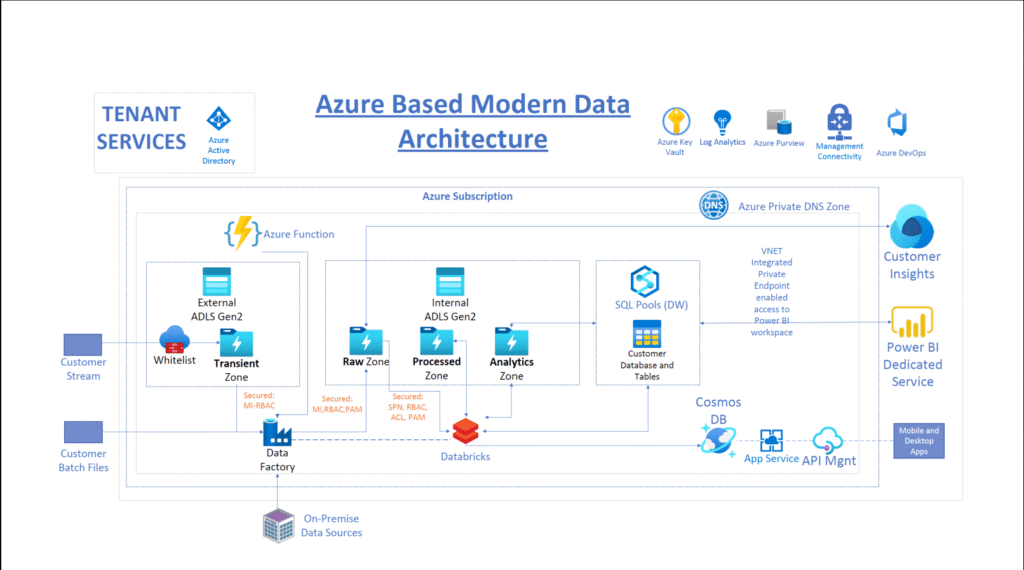
Reading Time: 4 minutesTable of Contents 1. Executive Summary Enterprises embracing two or more public clouds face unique security challenges: inconsistent controls, blind spots, and operational complexity. This report outlines a holistic architecture—spanning network fabric, resilient application platforms, identity-centric access, client-specific handling, and Read More …