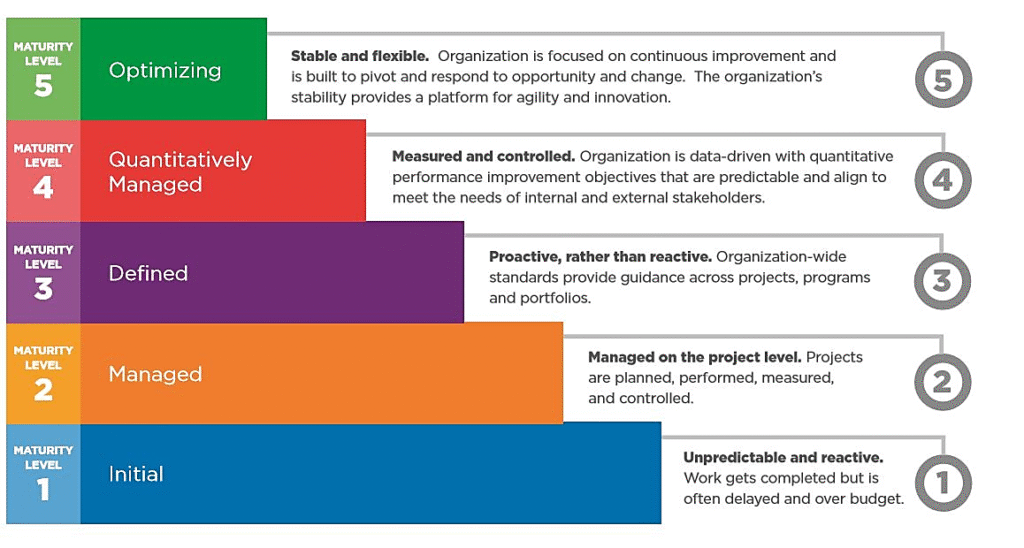
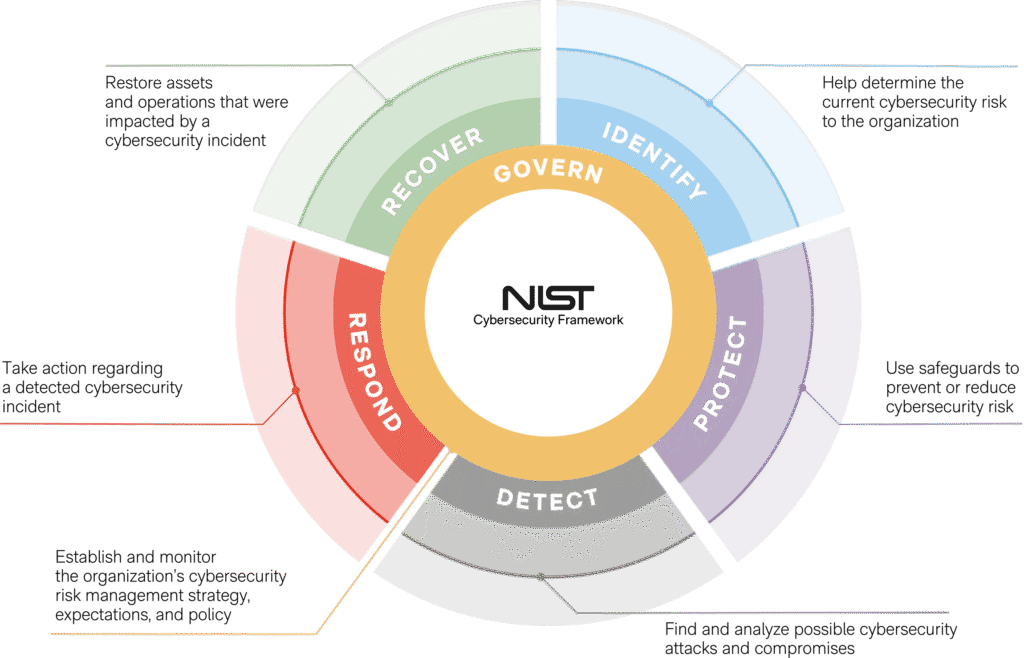
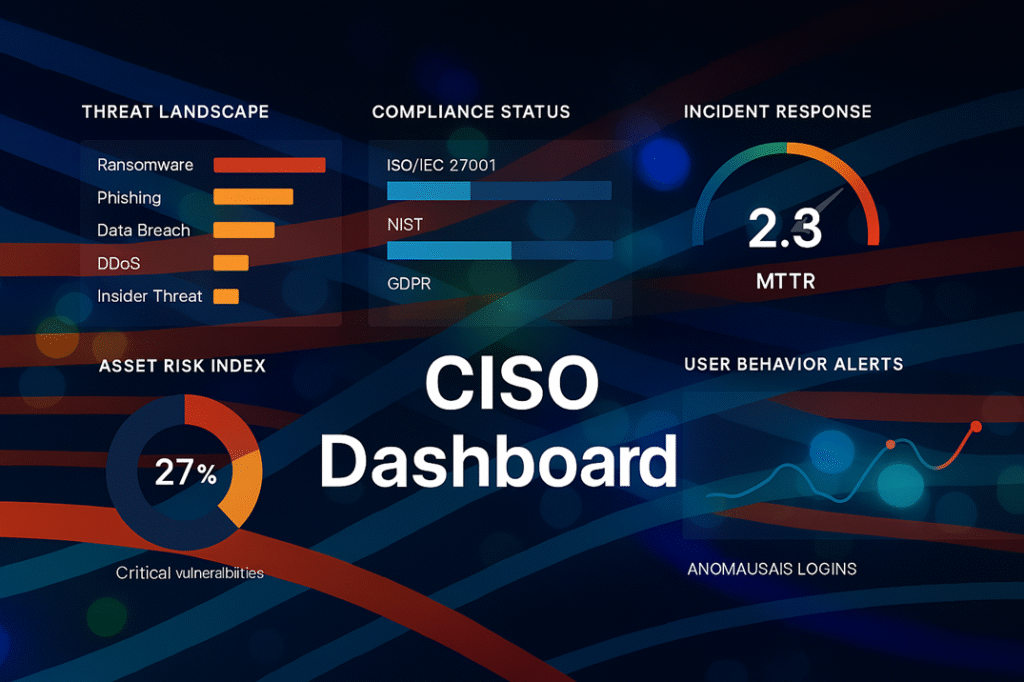
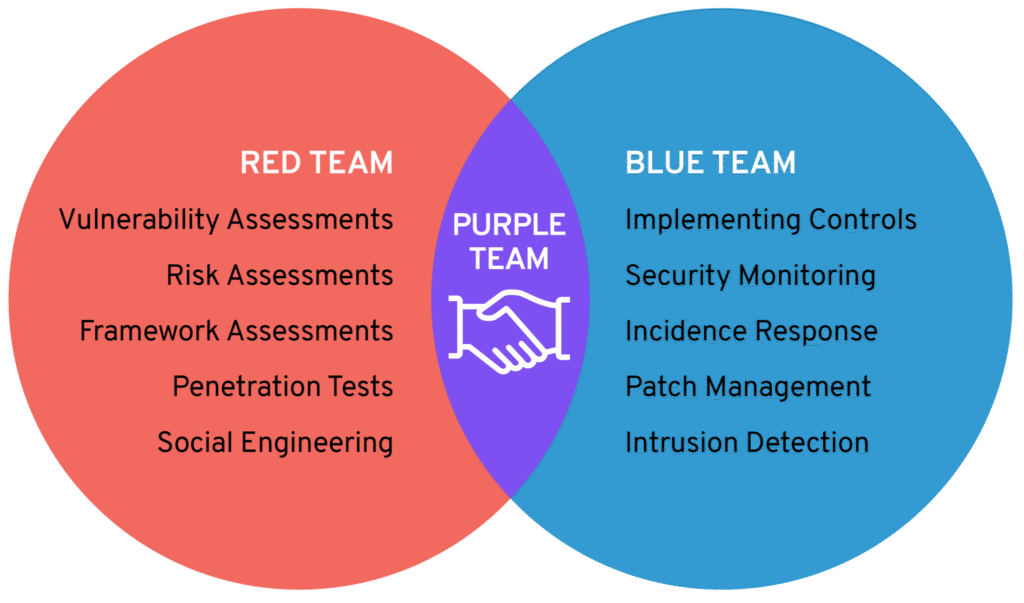
Reading Time: 2 minutesA company’s cybersecurity framework needs rebuilding when it shows repeated gaps, outdated practices, or fails to adapt to evolving threats. Key warning signs include frequent incidents, audit failures, and static controls that don’t match the current attack surface.