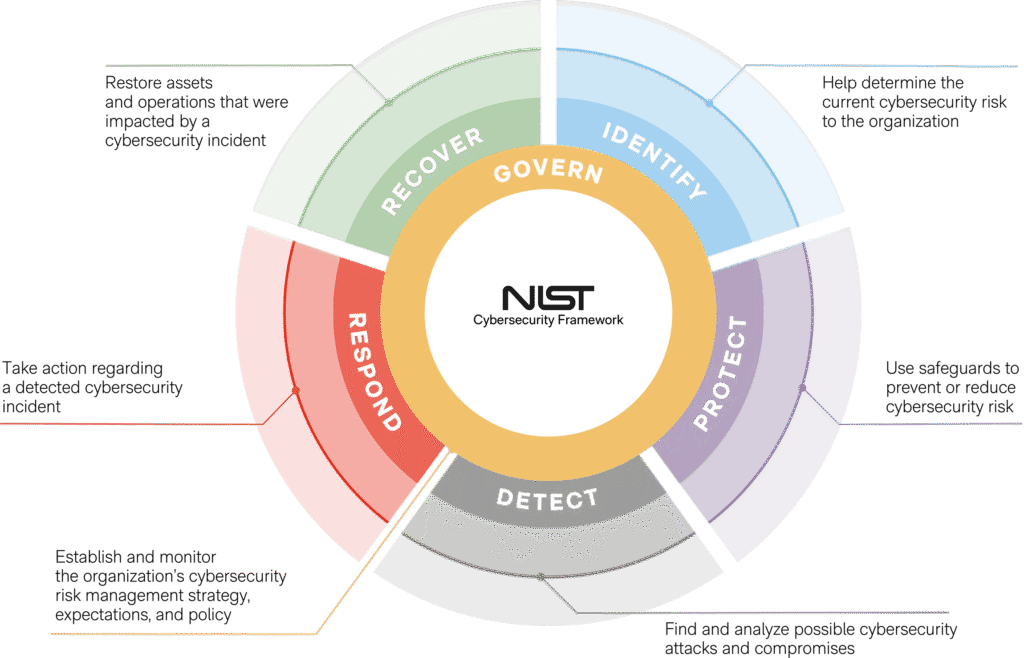
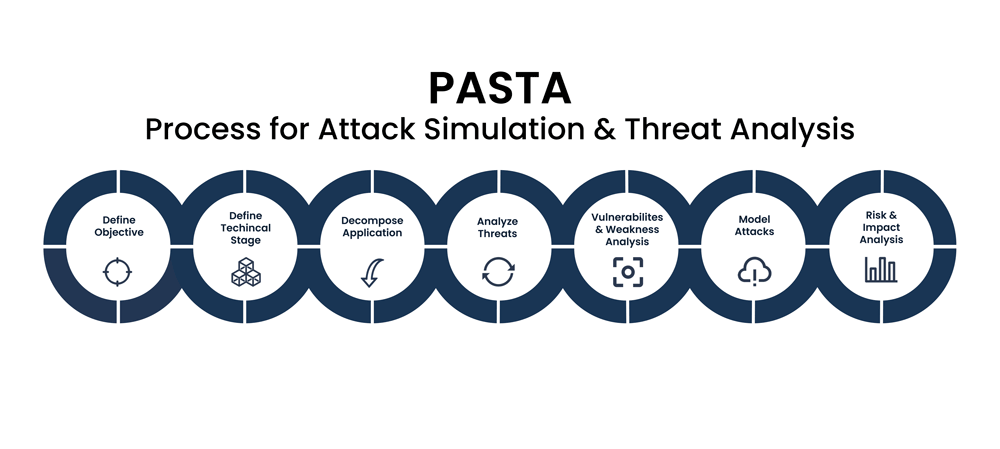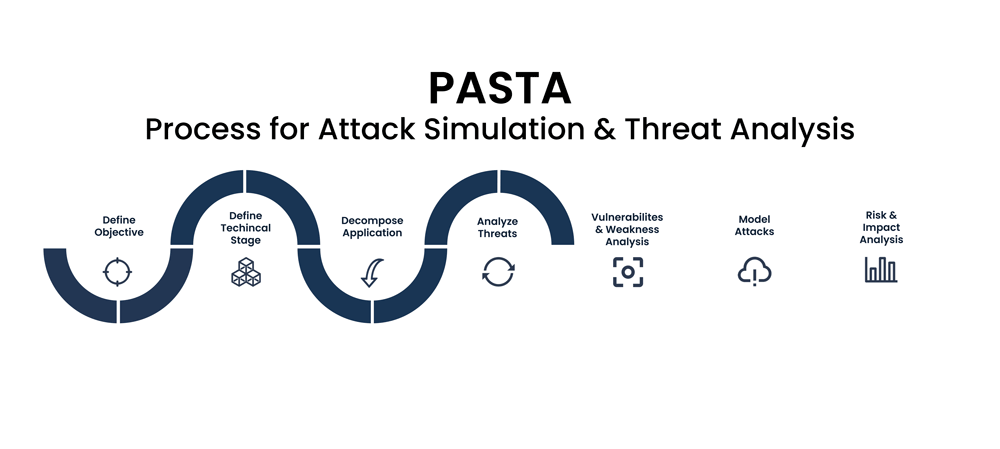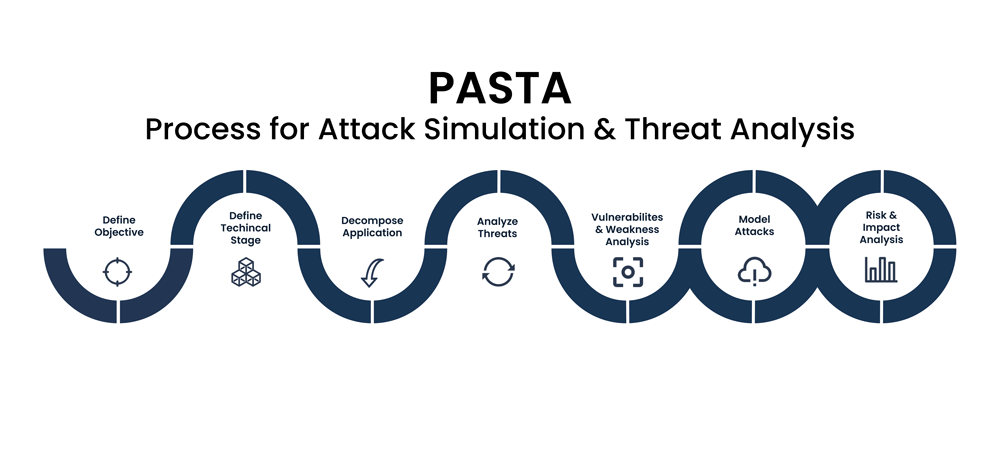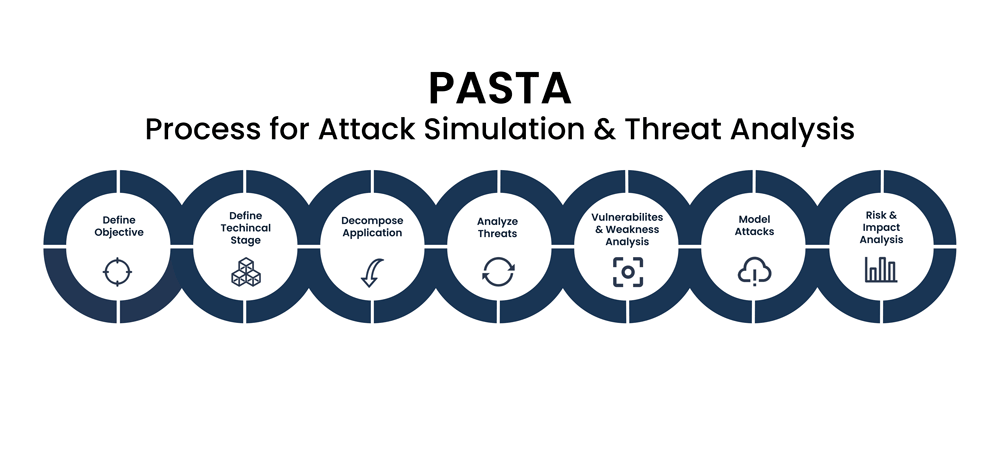
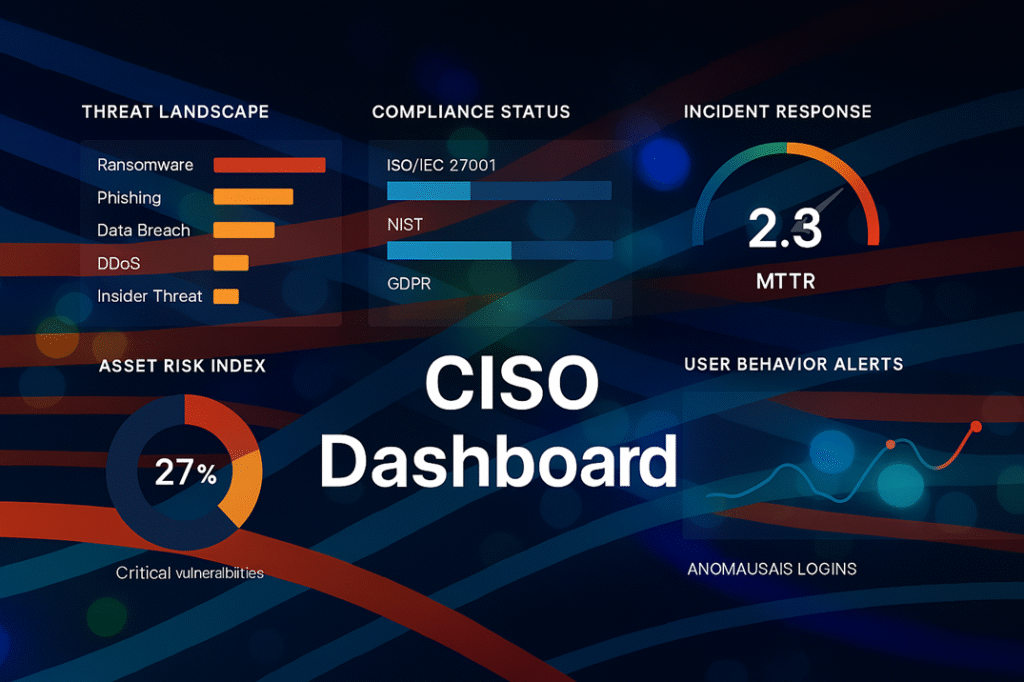
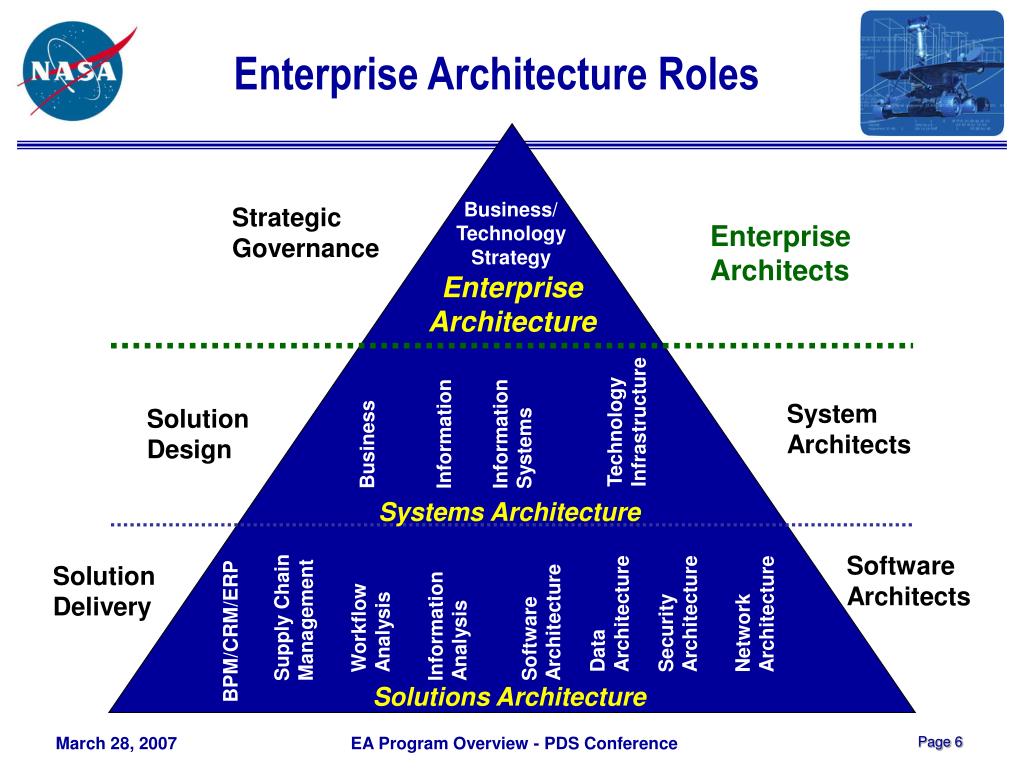
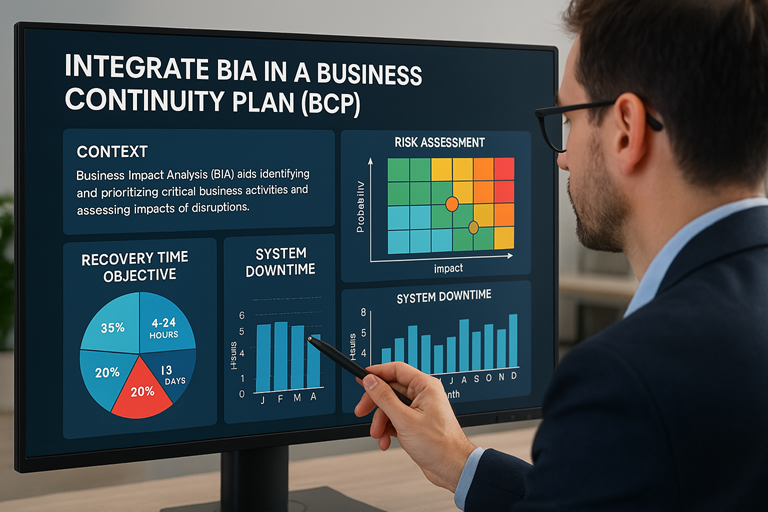
Reading Time: 5 minutesThe escalating volume and sophistication of cyber threats, coupled with a shortage of security professionals, necessitate a shift from manual incident response (IR) to automated solutions. Security Orchestration, Automation, and Response (SOAR) platforms offer a transformative approach by consolidating security operations, automating repetitive tasks, and streamlining incident handling.