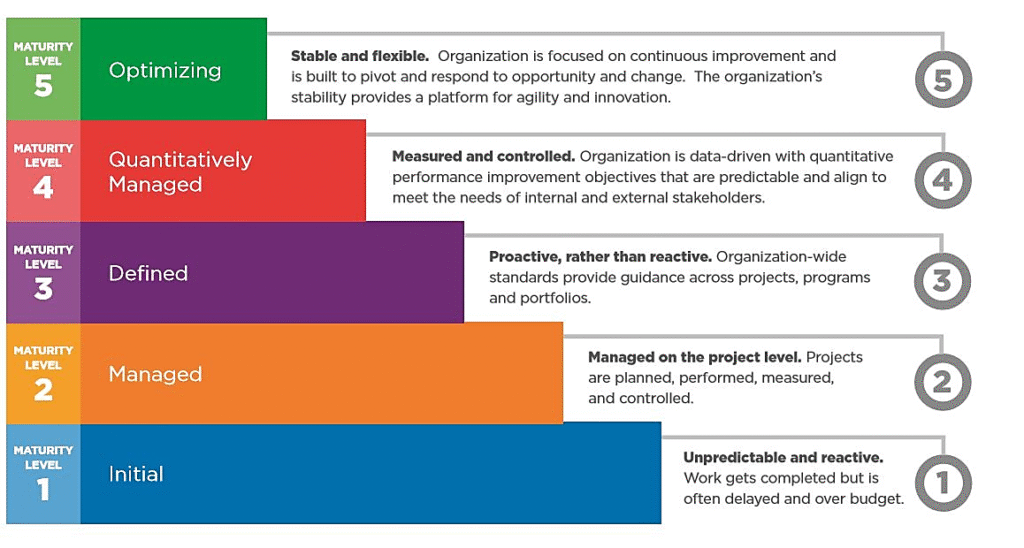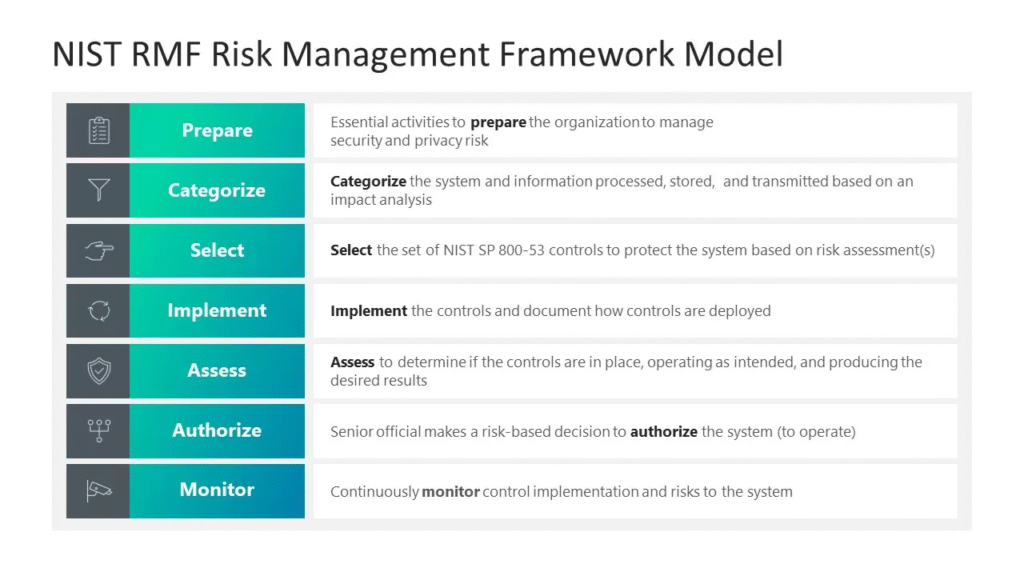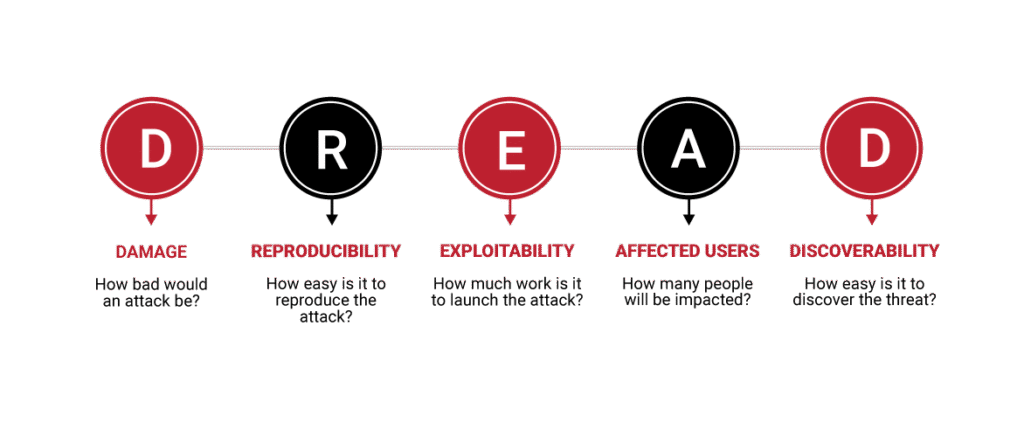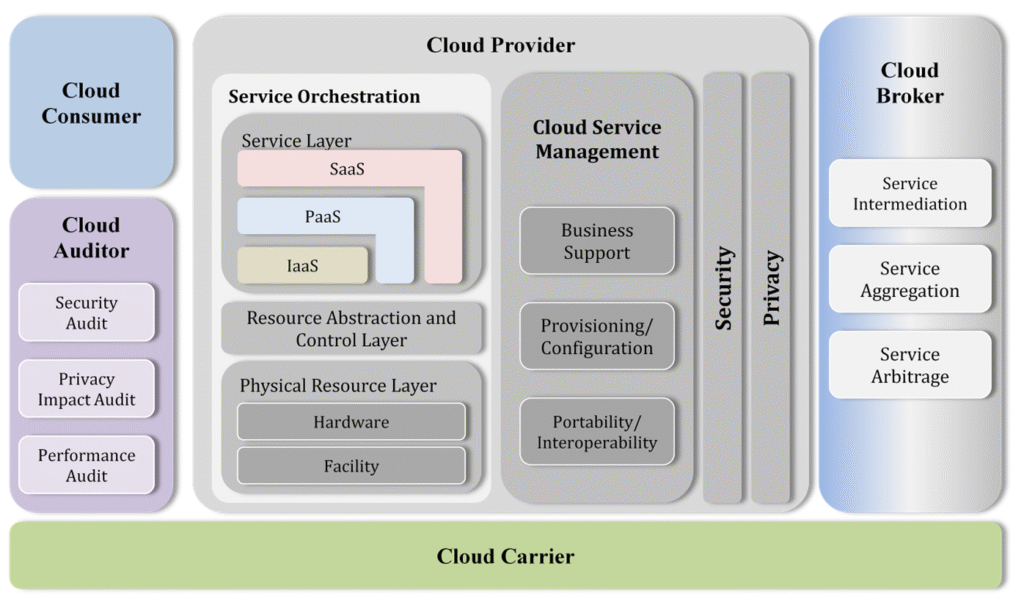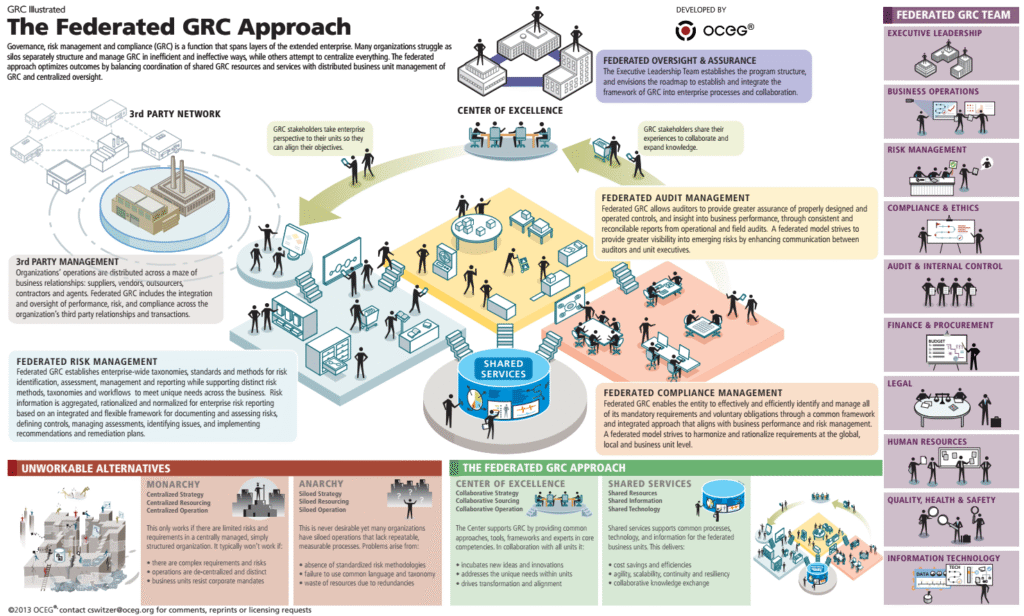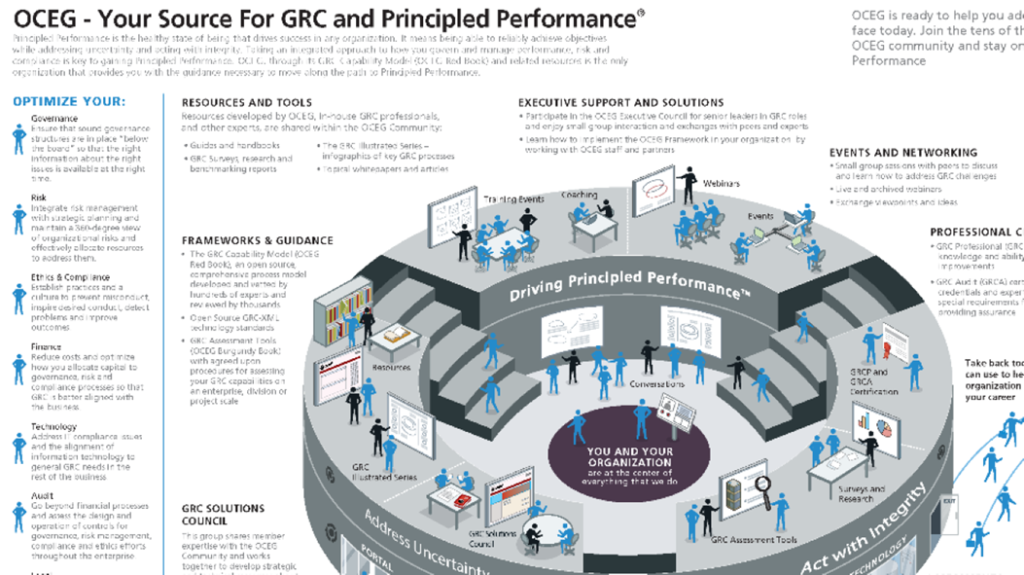
Reading Time: 3 minutesGovernance, Risk, and Compliance (GRC) is an integrated organizational strategy designed to manage corporate governance, identify and mitigate risks, and ensure ongoing compliance with industry standards and government regulations. It also refers to specialized software suites that help implement and Read More …