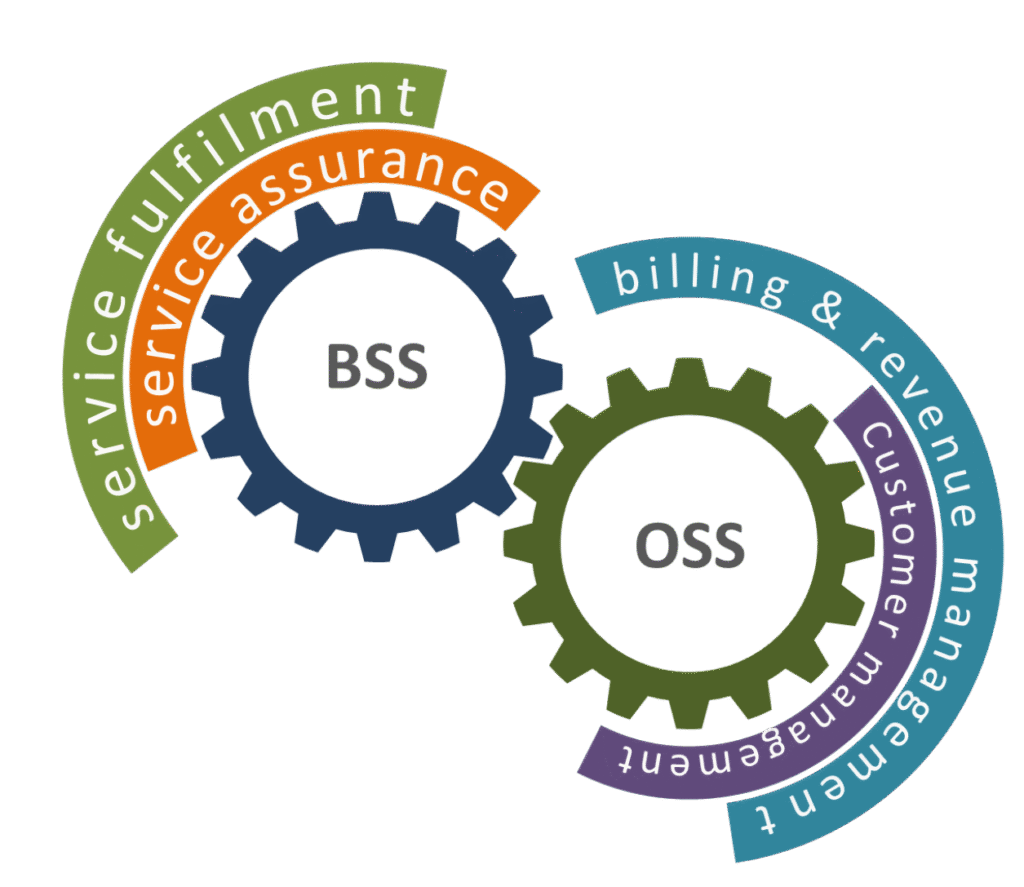
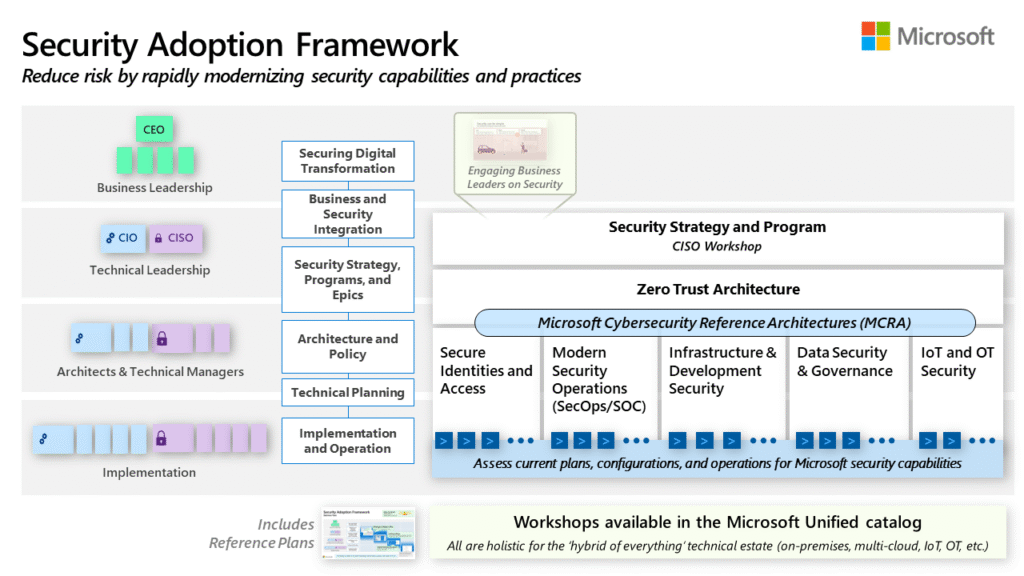
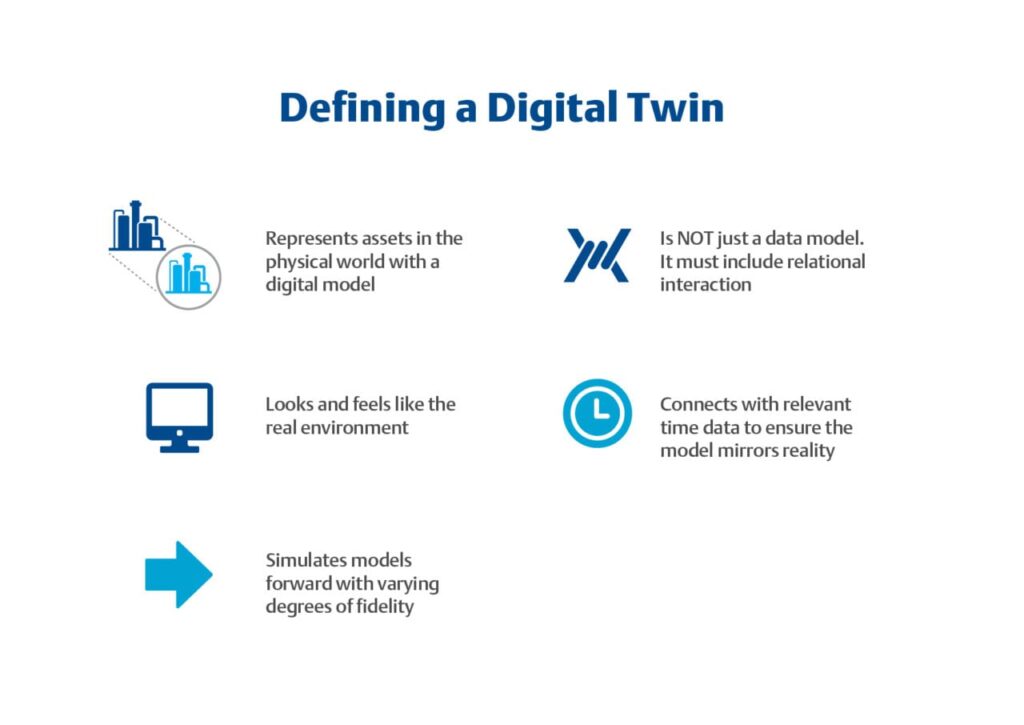
Reading Time: 7 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: July 28, 2024 Location: Dhaka, Bangladesh Version: 1.0 1. Executive Summary The Sherwood Applied Business Security Architecture (SABSA) is a foundational, open-standard methodology for Read More …