
Reading Time: 4 minutesArtificial Intelligence has crossed a threshold in cybersecurity. It’s no longer just a defensive accelerator — it’s now a fully weaponized capability in the hands of adversaries.
Meeting of Brilliant Syche – IT Pro's Corner

Reading Time: 2 minutesAI-driven tools can craft highly targeted, multilingual phishing emails by scraping OSINT, leaked credentials, and social media profiles. Deepfake voice generators mimic executives’ tone and emotional cues, making human detection far more difficult. Services like PhishGPT+ enable automated spear-phishing campaigns tailored by geolocation, language, and psychological triggers.

Reading Time: 8 minutesThis blueprint outlines a comprehensive Security Orchestration, Automation, and Response (SOAR) playbook to combat cryptojacking—the unauthorized use of computing resources for cryptocurrency mining. Cryptojacking poses significant financial, operational, and reputational risks by silently consuming CPU cycles, increasing power costs, degrading system performance, and introducing hidden vulnerabilities.

Reading Time: 5 minutesThe escalating volume and sophistication of cyber threats, coupled with a shortage of security professionals, necessitate a shift from manual incident response (IR) to automated solutions. Security Orchestration, Automation, and Response (SOAR) platforms offer a transformative approach by consolidating security operations, automating repetitive tasks, and streamlining incident handling.

Reading Time: 6 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: March 29, 2025 Location: Dhaka, Bangladesh Version: 1.0 1. Executive Summary Ransomware has evolved into a sophisticated, multi-stage cyber threat causing significant financial, operational, Read More …

Reading Time: 5 minutesBlueprint Details 1. Executive Summary: The Imperative for Smarter Threat Prioritization The cybersecurity landscape is overwhelmed by an ever-increasing volume of vulnerabilities, with over 25,000 new CVEs reported in 2022 alone. Traditional vulnerability management, often relying solely on CVSS scores, Read More …

Reading Time: 6 minutesData Loss Prevention (DLP) is a crucial cybersecurity strategy designed to detect and prevent data breaches by blocking unauthorized extraction or exposure of sensitive data. It combines people, processes, and technology to identify, classify, and apply usage policies to sensitive information across endpoints, networks, and cloud platforms (data at rest, in motion, and in use).

Reading Time: 6 minutesExtended Detection and Response (XDR) is a pivotal evolution in enterprise cybersecurity. It unifies, intelligently, and automates threat detection, investigation, and response by aggregating telemetry from endpoints, networks, cloud, identity, and email into a single platform. This holistic visibility, powered by AI/ML, detects complex attacks, reduces alert fatigue, and accelerates incident containment.

Reading Time: 6 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: March 17, 2025 Location: Dhaka, Bangladesh Version: 1.0 Executive Summary The “Implementation Plan – NIST AI RMF” provides a comprehensive roadmap for large enterprises Read More …

Reading Time: 4 minutesInformation Technology (IT) governance has evolved from a technical control function into a strategic enterprise imperative, driven by digital transformation, complex regulations, and escalating cybersecurity threats. The modern mandate for IT governance is to ensure technology aligns with business strategy, delivers measurable value, optimizes resources, and manages risk effectively.

Reading Time: 4 minutesIn an era of unprecedented volatility, IT Resilience is a fundamental requirement for survival, moving beyond reactive Disaster Recovery (DR) and Business Continuity (BC) to a proactive discipline of survivability. This blueprint provides a framework to embed resilience into the core of the digital enterprise, ensuring critical services remain available despite adverse conditions.

Reading Time: 3 minutesPart I: The Strategic Imperative The adoption of enterprise blockchain, or Distributed Ledger Technology (DLT), is driven by the need for enhanced trust, transparency, and efficiency in multi-party business processes. Unlike public blockchains (e.g., Bitcoin), enterprise systems are permissioned, meaning Read More …

Reading Time: 3 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: March 1, 2025 Version: 1.0 Part 1: The Strategic Imperative The shift from traditional, script-based automation to AI-driven quality engineering is a transformative evolution Read More …

Reading Time: 3 minutesThe traditional “castle-and-moat” security model is obsolete, broken by the rise of cloud computing, a hybrid workforce, and the explosion of unmanaged devices. The network perimeter has dissolved, creating a new reality where attackers with compromised credentials can move freely within a supposedly “trusted” internal network.

Reading Time: 4 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: January 21, 2025 Location: Dhaka, Bangladesh Version: 1.0 Part I: The Strategic Mandate of the Modern CTO The role of the Chief Technology Officer Read More …

Reading Time: 3 minutesThe selection of a Security Information and Event Management (SIEM) platform is a foundational decision for any modern Security Operations Center (SOC). The modern SIEM has evolved from a simple log repository into an intelligent, AI-driven platform essential for digital resilience.

Reading Time: 4 minutesThe Tensor Processing Unit (TPU) is a custom-built Application-Specific Integrated Circuit (ASIC) developed by Google to accelerate AI and machine learning workloads. Its creation was driven by the unsustainable computational and energy demands of running deep neural networks on general-purpose hardware like CPUs and GPUs.

Reading Time: 4 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: February 3, 2022 Location: Dhaka, Bangladesh Version: 1.0 Part I: The Strategic Imperative of Data Integrity 1.0 Defining the Data Integrity Landscape Data integrity Read More …

Reading Time: 4 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: September 4, 2023 Location: Dhaka, Bangladesh Version: 1.0 Executive Summary: The Data Imperative In the modern economy, data is the central force behind competitive Read More …

Reading Time: 3 minutesStatus: Summary of Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Date: August 23, 2023 Version: 1.0 1. Introduction & Executive Summary This document provides a condensed overview of the comprehensive AI-specific Incident Response Plan Read More …
Reading Time: 3 minutesStatus: Final BlueprintAuthor: Shahab Al Yamin ChawdhuryOrganization: Principal Architect & Consultant GroupResearch Date: April 9, 2024Location: Dhaka, BangladeshVersion: 1.0 The New Imperative: Securing the AI-Driven Enterprise The integration of Artificial Intelligence (AI) is a present-day reality, creating a new, dynamic, Read More …

Reading Time: 3 minutesThe 2025 IT risk landscape is defined by the industrialization of cyber threats and the obsolescence of traditional, reactive security postures. Adversaries now leverage AI-driven attack platforms, operate sophisticated Ransomware-as-a-Service (RaaS) ecosystems, and systematically exploit global supply chains.

Reading Time: 4 minutesStatus: Final Blueprint (Summary) Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: 24 May 2024 Location: Dhaka, Bangladesh Version: 1.0 Executive Summary Data Security Posture Management (DSPM) has emerged as a critical strategic response to Read More …

Reading Time: 4 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: 2 August 2025 Location: Dhaka, Bangladesh Version: 1.0 1. Executive Summary: The New Security Imperative for AI The rapid enterprise adoption of Large Language Read More …

Reading Time: 4 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: July 26, 2024 Version: 1.0 1. The Strategic Imperative for Modernization Application modernization is a critical business initiative to update legacy software, aligning it Read More …

Reading Time: 6 minutesStatus: Final Blueprint (Summary) Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: June 1, 2024 Location: Dhaka, Bangladesh Version: 1.0 1. The Core Dilemma: Assessor vs. Builder Mindset We are observing worldwide adoption on CISSP Read More …

Reading Time: 3 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: August 1, 2025 Location: Dhaka, Bangladesh Version: 1.0 1. The Strategic Imperative The operationalization of Cyber Threat Intelligence (CTI) is a strategic business necessity. Read More …

Reading Time: 4 minutesStatus: Final Blueprint Summary Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: March 1, 2022 Location: Dhaka, Bangladesh Version: 1.0 Part I: Foundational Blueprint Defining the Modern Architect: Beyond the Job Description The Cybersecurity Architect Read More …

Reading Time: 4 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: July 26, 2024 Location: Dhaka, Bangladesh Version: 1.0 Executive Summary Website defacement is a critical security breach that inflicts significant reputational and financial damage. Read More …
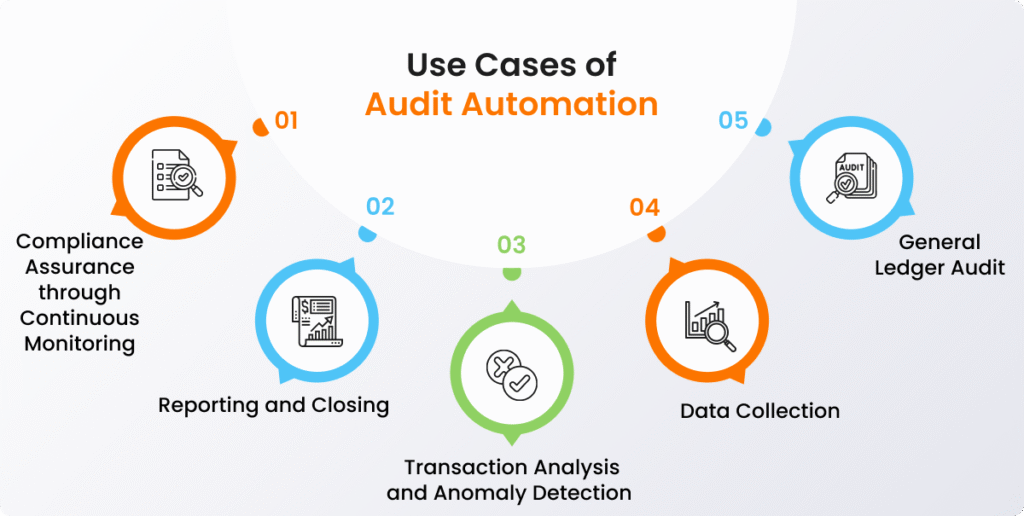
Reading Time: 5 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: December 9, 2024 Location: Dhaka, Bangladesh Version: 1.0 I. Executive Summary The internal audit function is undergoing a significant transformation, driven by complex business Read More …