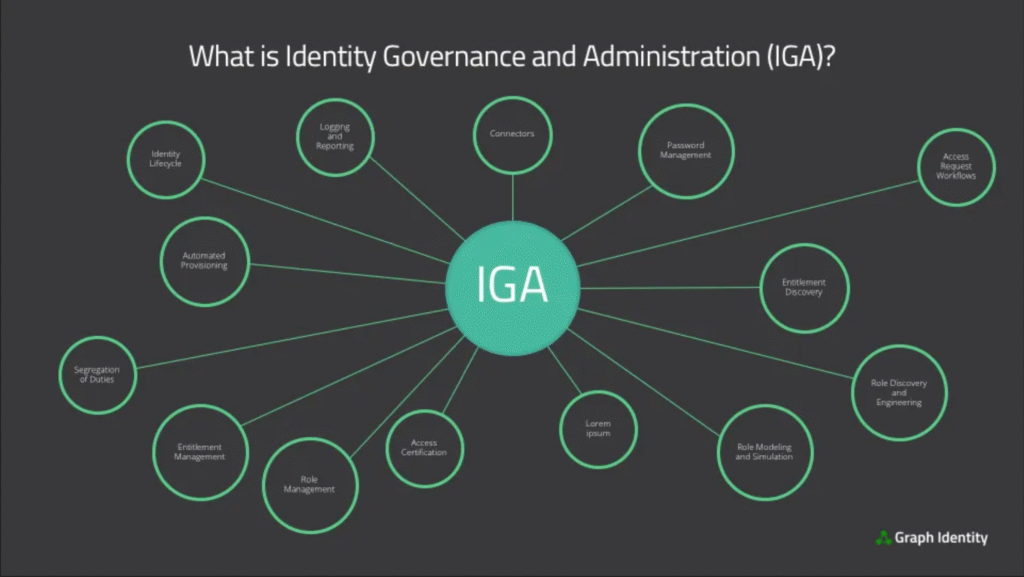
Reading Time: 5 minutesStatus: Final BlueprintAuthor: Shahab Al Yamin ChawdhuryOrganization: Principal Architect & Consultant GroupResearch Date: April 2, 2025Location: Dhaka, BangladeshVersion: 1.0 1. Executive Summary and Strategic Imperatives The “SOAR Playbook for Malware Containment” outlines Security Orchestration, Automation, and Response (SOAR) as a Read More …