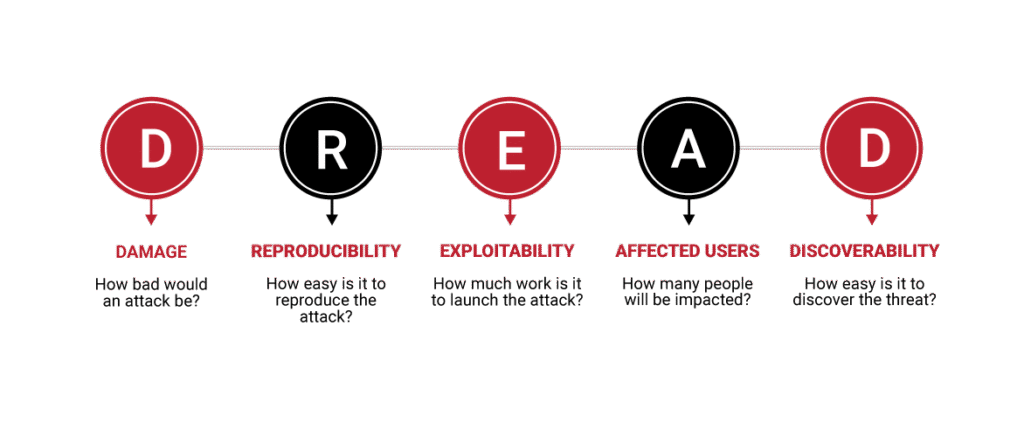
Reading Time: 5 minutesBlueprint Details 1. Executive Summary: The Imperative for Smarter Threat Prioritization The cybersecurity landscape is overwhelmed by an ever-increasing volume of vulnerabilities, with over 25,000 new CVEs reported in 2022 alone. Traditional vulnerability management, often relying solely on CVSS scores, Read More …