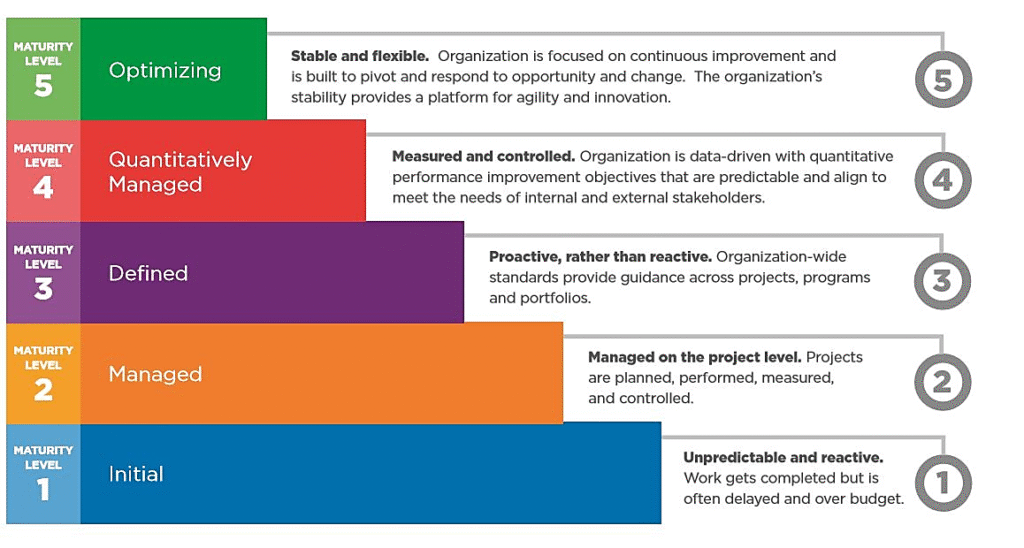
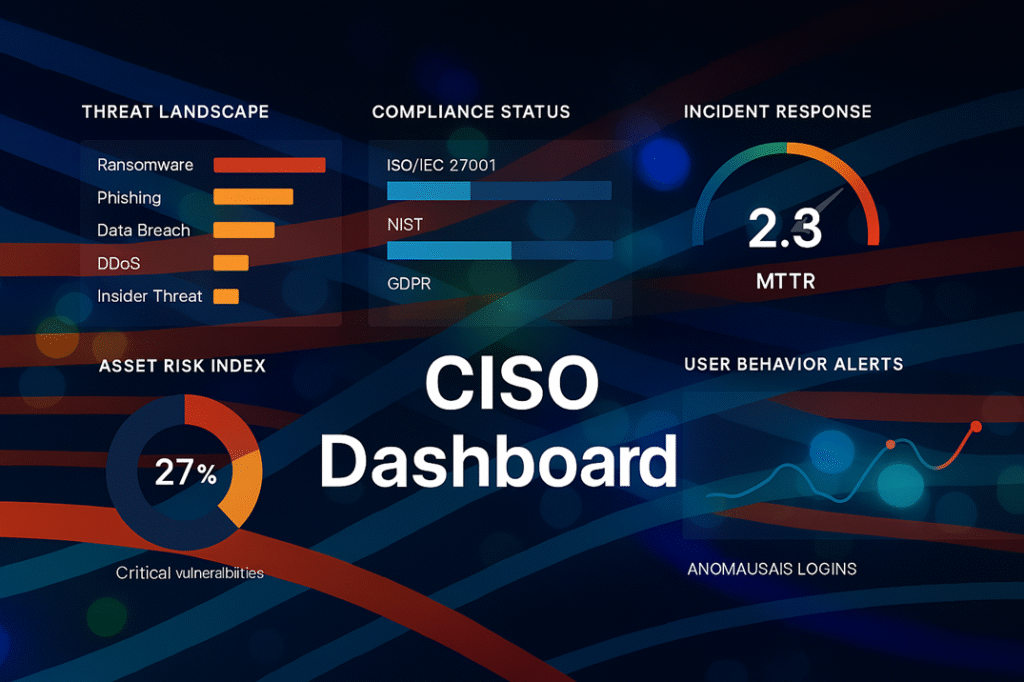
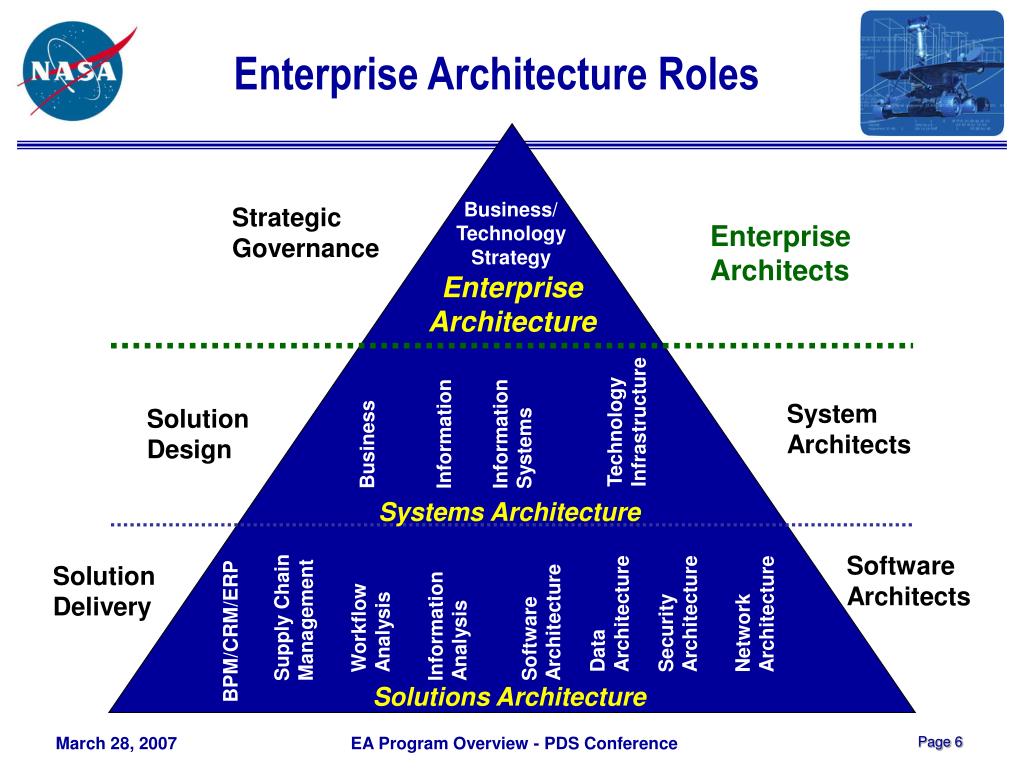
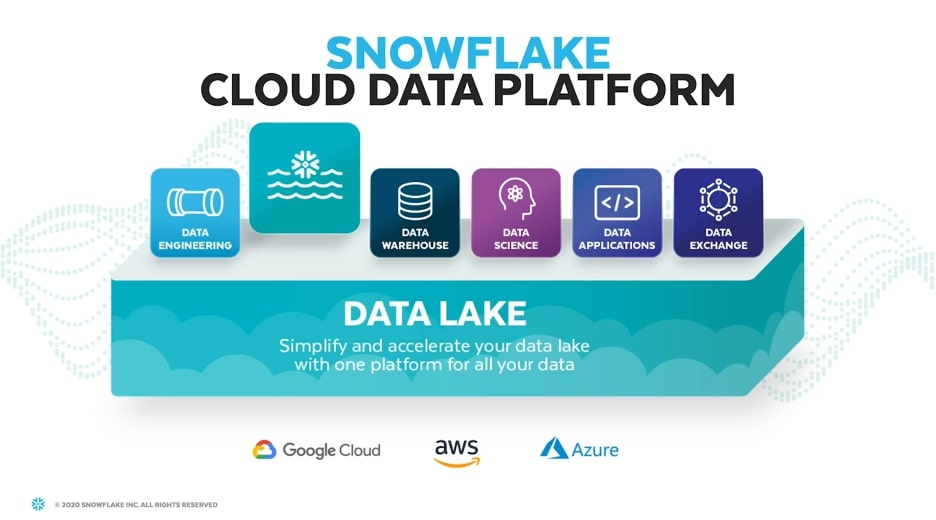
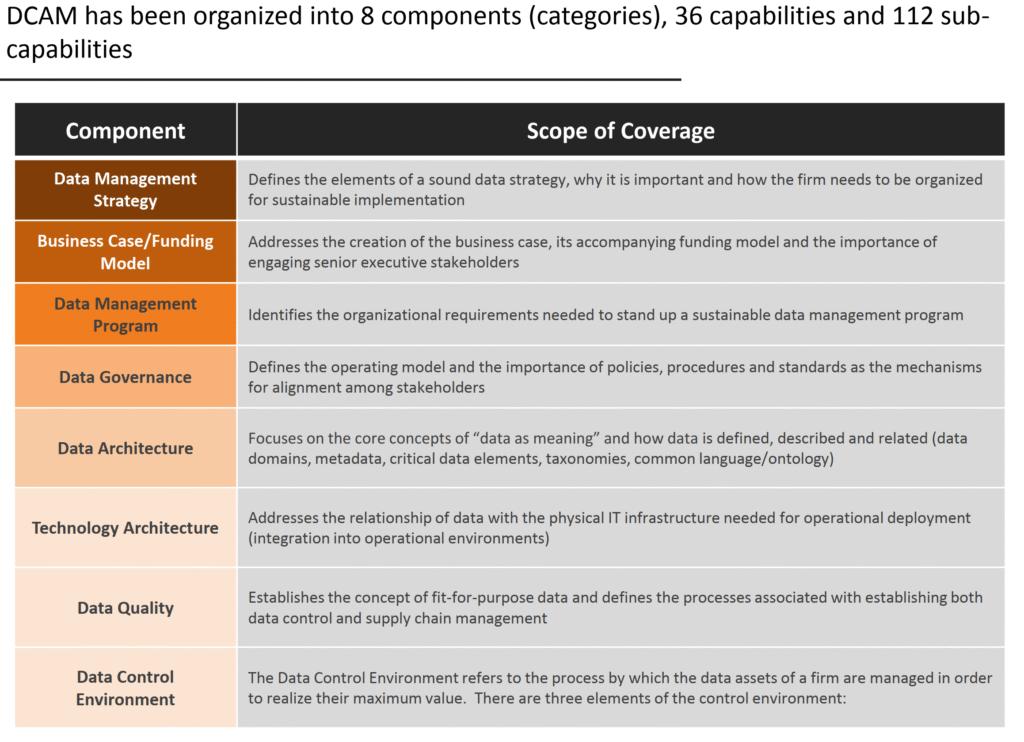
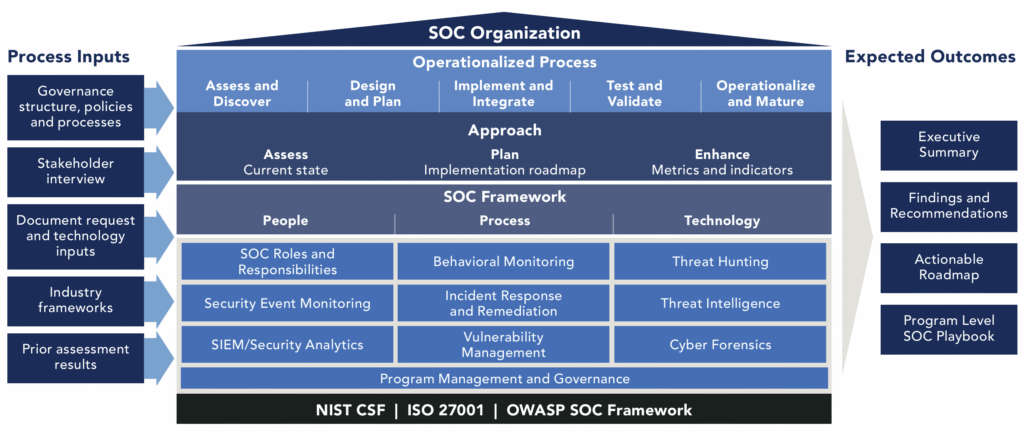
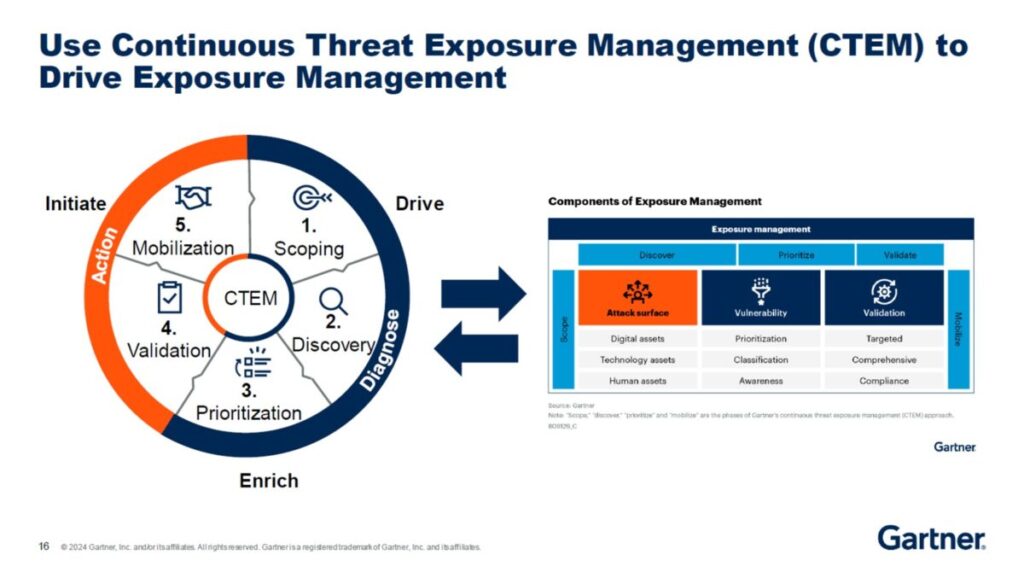
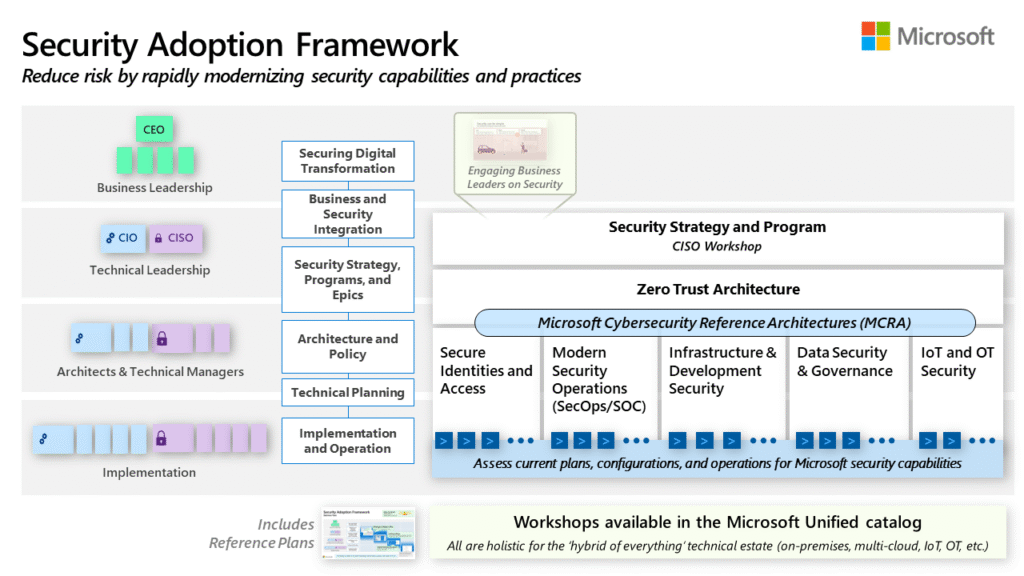
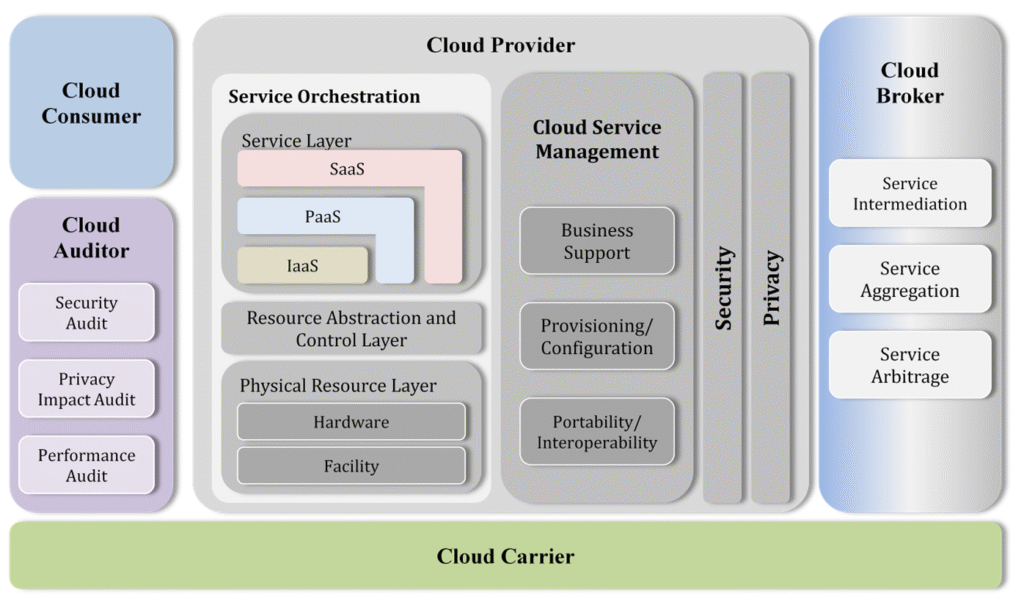
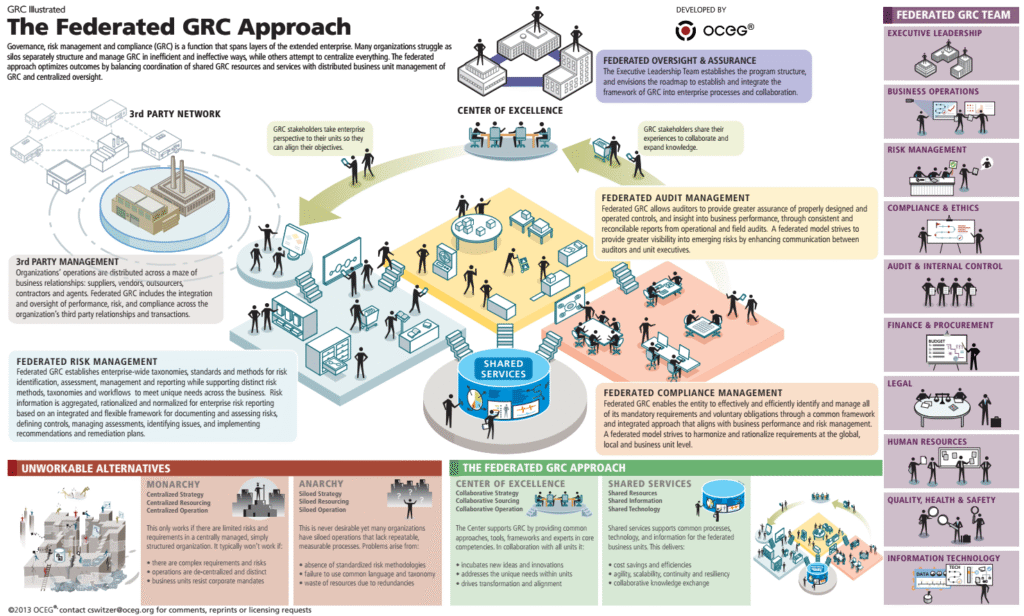
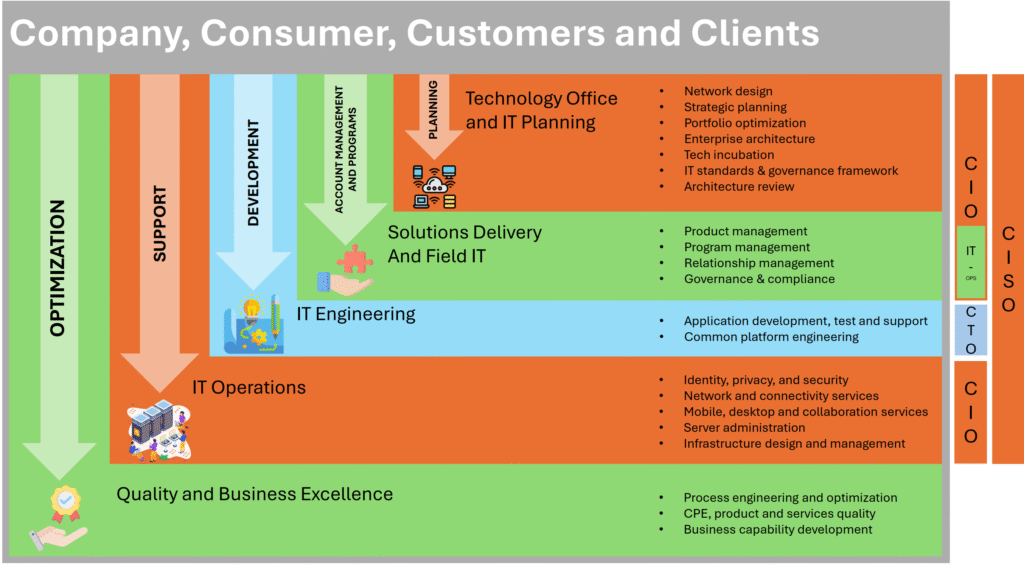
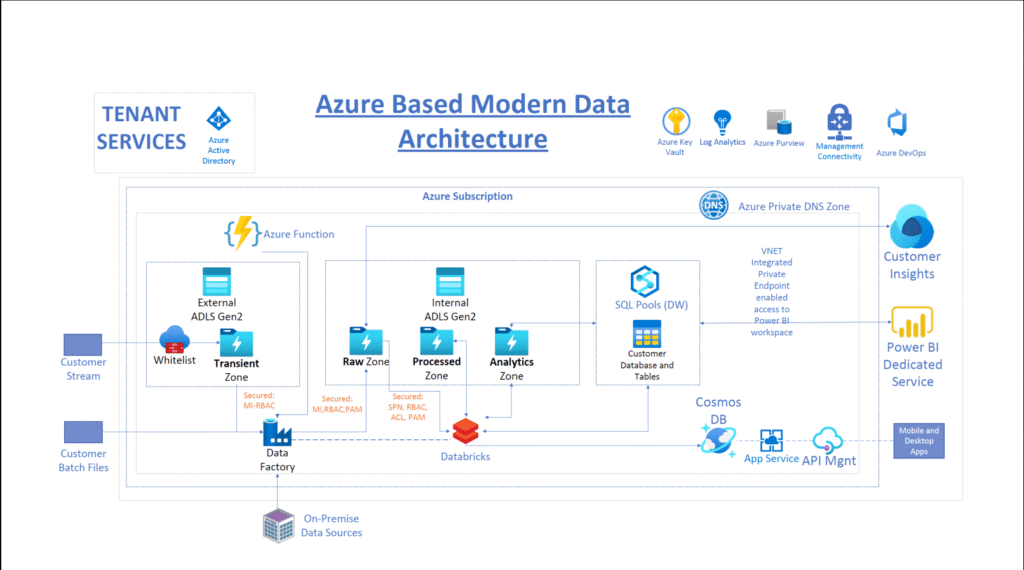
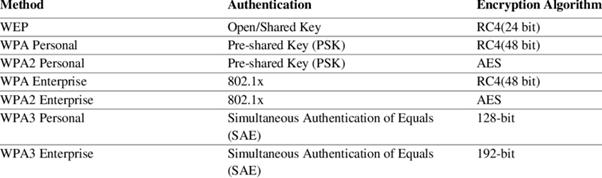
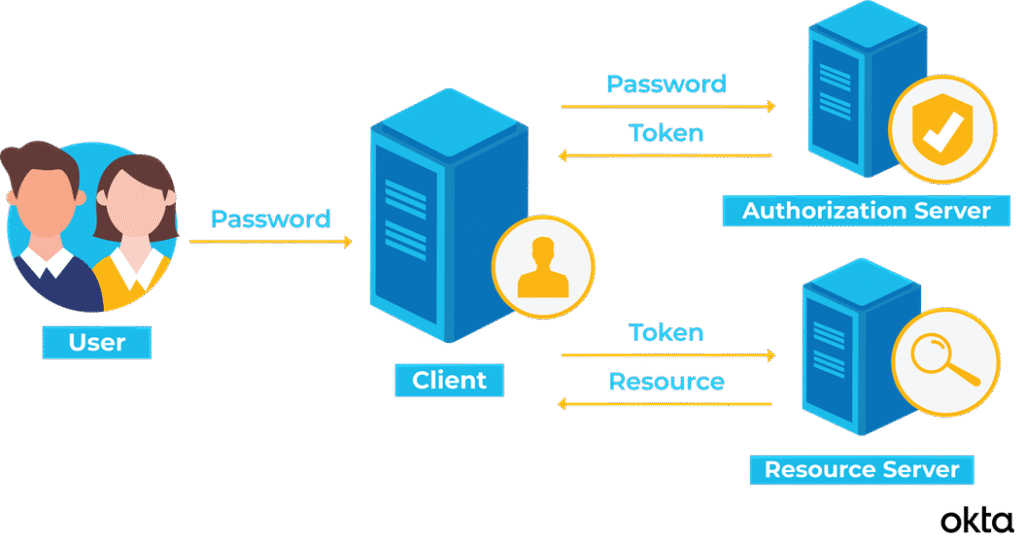
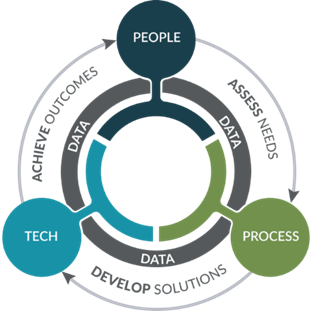
Reading Time: 7 minutesCybersecurity assessment frameworks are structured methodologies guiding organizations to establish and maintain robust cybersecurity postures. They provide a roadmap for identifying, assessing, and managing risks to digital assets, enhancing resilience, streamlining operations, and building trust. Cybersecurity is a core business enabler, requiring agile, adaptive security, strong governance, and leveraging a complementary ecosystem of frameworks to tailor security to unique needs.