
Reading Time: 4 minutesModern data protection has evolved beyond simple recovery from hardware failure into a strategic imperative for business resilience.
Meeting of Brilliant Syche – IT Pro's Corner

Reading Time: 4 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: February 3, 2022 Location: Dhaka, Bangladesh Version: 1.0 Part I: The Strategic Imperative of Data Integrity 1.0 Defining the Data Integrity Landscape Data integrity Read More …

Reading Time: 4 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: September 4, 2023 Location: Dhaka, Bangladesh Version: 1.0 Executive Summary: The Data Imperative In the modern economy, data is the central force behind competitive Read More …
Reading Time: 3 minutesStatus: Final BlueprintAuthor: Shahab Al Yamin ChawdhuryOrganization: Principal Architect & Consultant GroupResearch Date: April 9, 2024Location: Dhaka, BangladeshVersion: 1.0 The New Imperative: Securing the AI-Driven Enterprise The integration of Artificial Intelligence (AI) is a present-day reality, creating a new, dynamic, Read More …

Reading Time: 4 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: July 26, 2024 Version: 1.0 1. The Strategic Imperative for Modernization Application modernization is a critical business initiative to update legacy software, aligning it Read More …

Reading Time: 6 minutesStatus: Final Blueprint (Summary) Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: June 1, 2024 Location: Dhaka, Bangladesh Version: 1.0 1. The Core Dilemma: Assessor vs. Builder Mindset We are observing worldwide adoption on CISSP Read More …
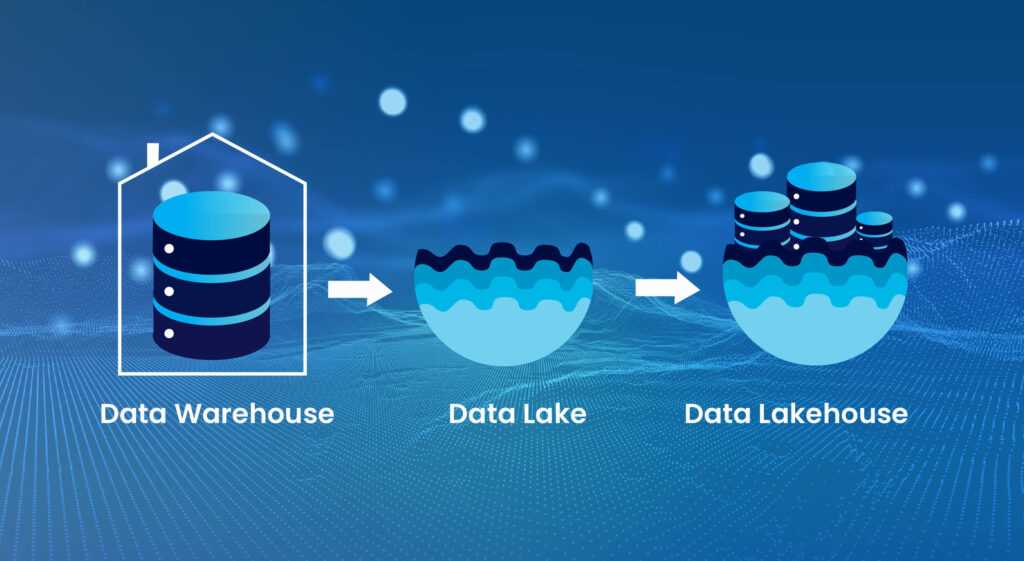
Reading Time: 4 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: October 26, 2023 Location: Dhaka, Bangladesh Version: 1.0 Executive Summary The Data Lakehouse paradigm marks a critical evolution in enterprise data architecture, merging the Read More …

Reading Time: 3 minutesStatus: Summary Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: July 24, 2025 Location: Dhaka, Bangladesh Version: 1.0 1. Executive Summary The modern enterprise faces a critical paradox: the need to defend against costly Read More …

Reading Time: 4 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: July 21, 2024 Location: Dhaka, Bangladesh Version: 1.0 1.0 Executive Summary 2.0 The Evolving Threat Landscape 3.0 Amplified Risk Factors in Hybrid Environments 4.0 Read More …

Reading Time: 6 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: July 22, 2024 Location: Dhaka, Bangladesh Version: 1.0 Executive Summary The enterprise Business Intelligence (BI) landscape is undergoing a seismic shift, driven by the Read More …

Reading Time: 8 minutesExecutive Summary The advent of publicly available generative Artificial Intelligence (AI) represents a paradigm shift in the cybersecurity landscape. While offering immense productivity benefits, these tools have also been weaponized, providing adversaries with the means to automate, scale, and enhance Read More …

Reading Time: 5 minutes1.0 Executive Summary This document provides a comprehensive architectural blueprint for the strategic implementation of honeypots within an enterprise network. Honeypots serve as a proactive defense mechanism, acting as decoy systems designed to attract, deceive, and analyze the activities of Read More …

Reading Time: 6 minutes1.0 Executive Summary & 2025-2026 Focus Areas This document provides a comprehensive, multi-domain blueprint of the modern cybersecurity landscape, designed for Chief Information Security Officers (CISOs) and security leadership. It maps critical functions, responsibilities, technologies, and metrics across all major Read More …

Reading Time: 2 minutesIT risk taxonomy is a structured framework that categorizes and classifies various types of IT-related risks, enabling organizations to manage and mitigate these risks effectively. Image Source: https://www.pwc.com/us/en/services/consulting/cybersecurity-risk-regulatory/library/technology-risk.html What is IT Risk Taxonomy? IT risk taxonomy is a systematic approach Read More …

Reading Time: 4 minutesTable of Contents 1. Executive Summary Enterprises embracing two or more public clouds face unique security challenges: inconsistent controls, blind spots, and operational complexity. This report outlines a holistic architecture—spanning network fabric, resilient application platforms, identity-centric access, client-specific handling, and Read More …

Reading Time: 3 minutesMachine Identity Security (MIS) or Machine Identity Management (MIM) is another critical aspect of cybersecurity that focuses on securing and managing the digital identities of machines, such as servers, applications, and IoT devices, which is currently overlooked due to lack Read More …
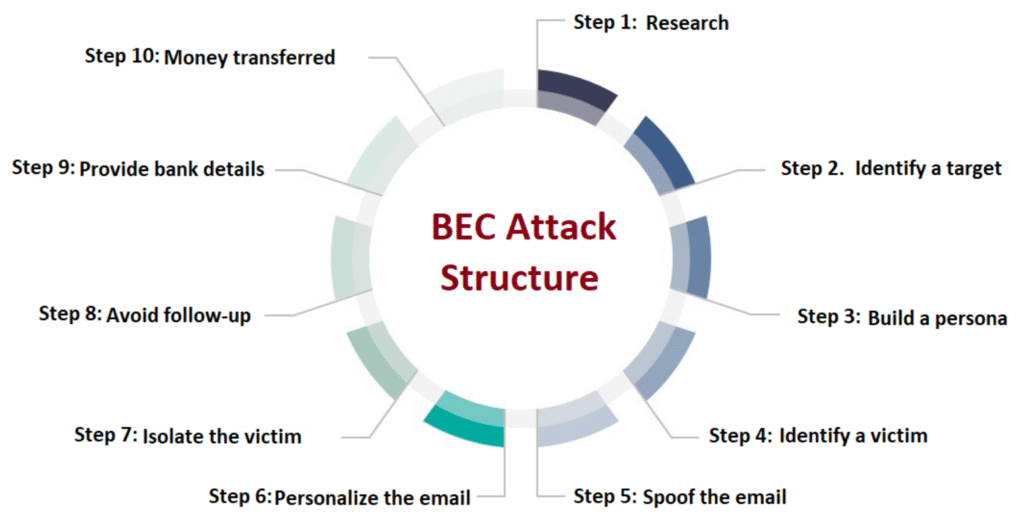
Reading Time: 3 minutesIn a typical Business Email Compromise (BEC) attack, attackers impersonate trusted individuals or organizations to deceive employees into taking harmful actions like transferring funds or sharing sensitive information. This involves research, email manipulation, and often social engineering tactics to exploit Read More …
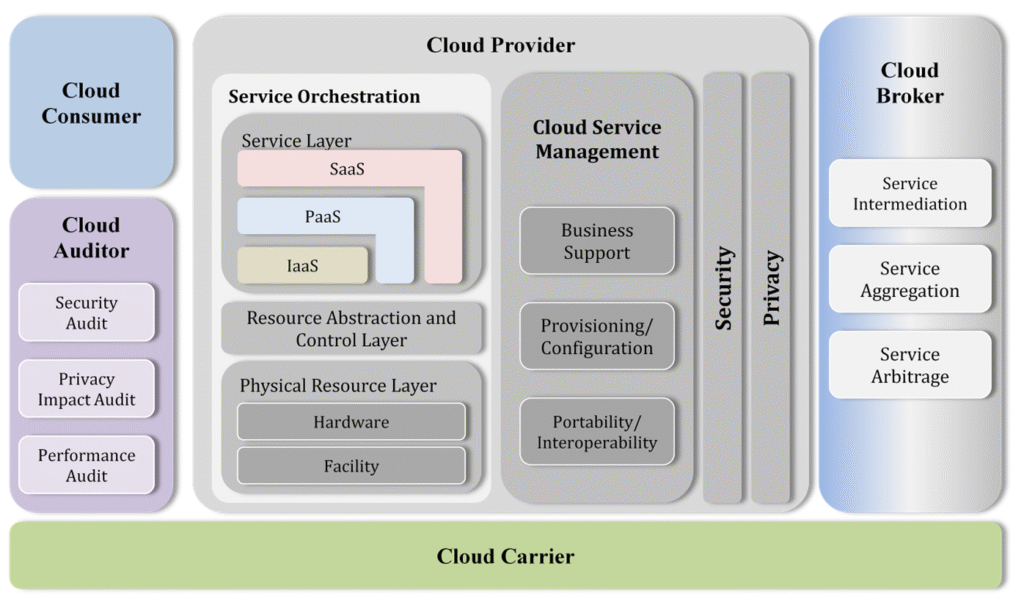
Reading Time: 9 minutesImage Source: https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication500-292.pdf Cloud computing has become an integral part of modern IT infrastructure, enabling enterprises to achieve scalability, efficiency, and agility. This paper discusses the Cloud Computing Reference Architecture (CCRA), including its key adoption requirements, standard bodies of knowledge Read More …
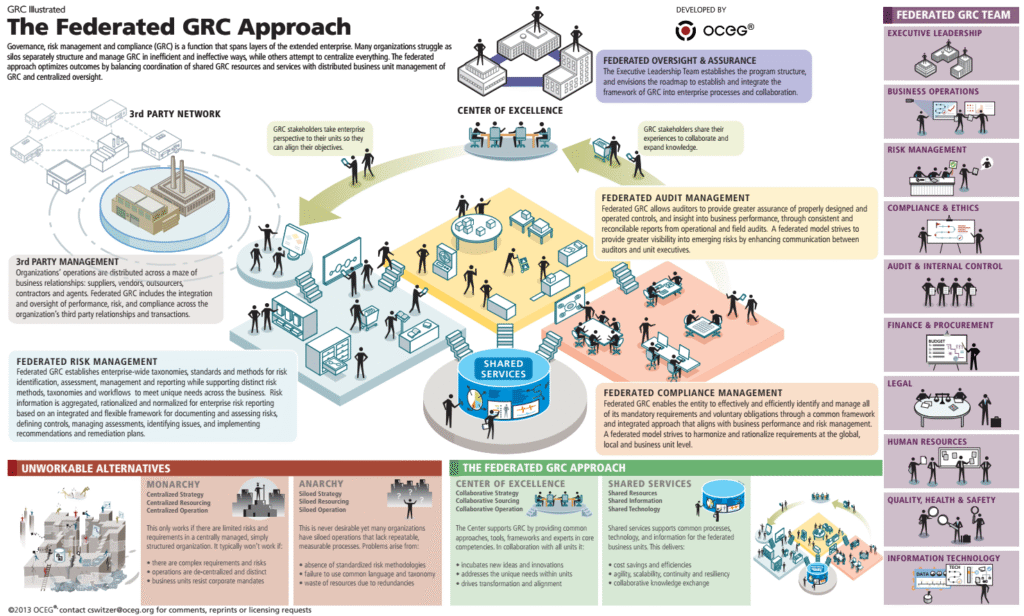
Reading Time: 3 minutesImage source: OCEG Organizations face unprecedented challenges in governance, risk management, and compliance (GRC). The increasing complexity of risks, regulations, and operational demands necessitates a modern, integrated approach to GRC. To connect the dots between risks, compliance, and other GRC elements that Read More …
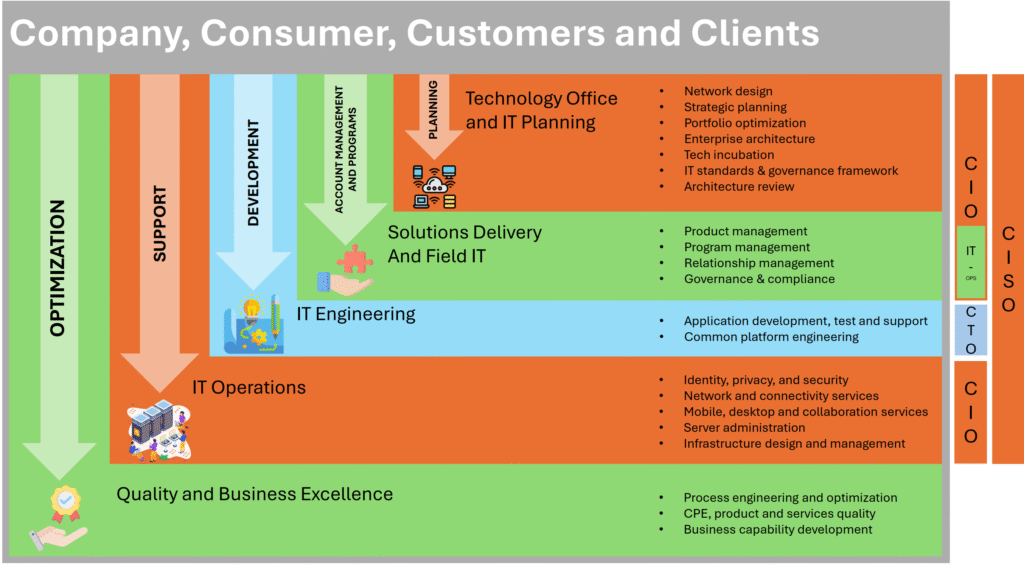
Reading Time: 2 minutesCISO due diligence refers to the process a CISO (Chief Information Security Officer) and their team conduct to assess the cybersecurity posture and practices of an organization or third party, particularly during mergers and acquisitions, or before entering into a Read More …
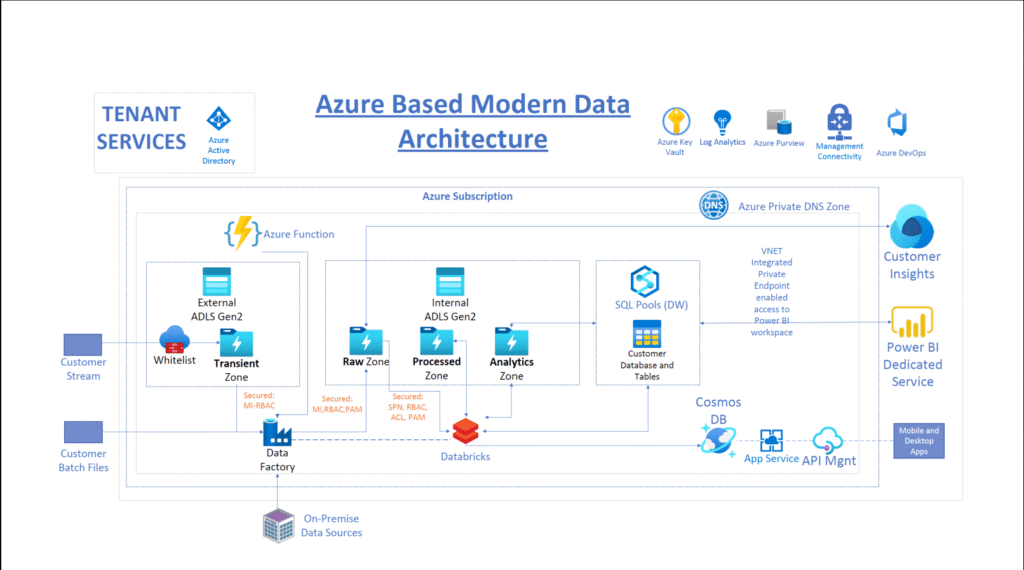
Reading Time: 6 minutesAzure Data Lake Architecture Overview Data Sources: Ingestion Layer: Storage Layer: Processing Layer: Analytics & Serving Layer: Governance & Security: Monitoring: +——————-+ +——————-+ +——————-+ | Data Sources | —> | Ingestion Layer | —> | Storage Layer | | (Structured, Read More …

Reading Time: 2 minutesEmphasizing on the technology requirements, implementation challenges, and platform security management: Image Source: Transportation | ITS Intelligent Transportation Solutions Overview The Automatic Car Toll System (ACTS) is an innovative solution aimed at streamlining toll collection processes for highways and bridges. Read More …