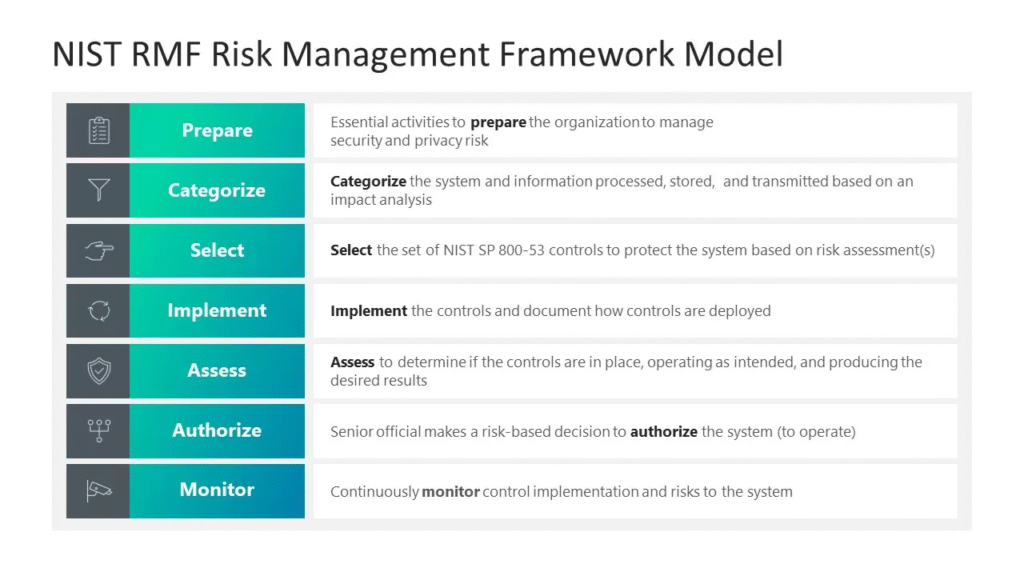
Reading Time: 6 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: March 29, 2025 Location: Dhaka, Bangladesh Version: 1.0 1. Executive Summary Ransomware has evolved into a sophisticated, multi-stage cyber threat causing significant financial, operational, Read More …