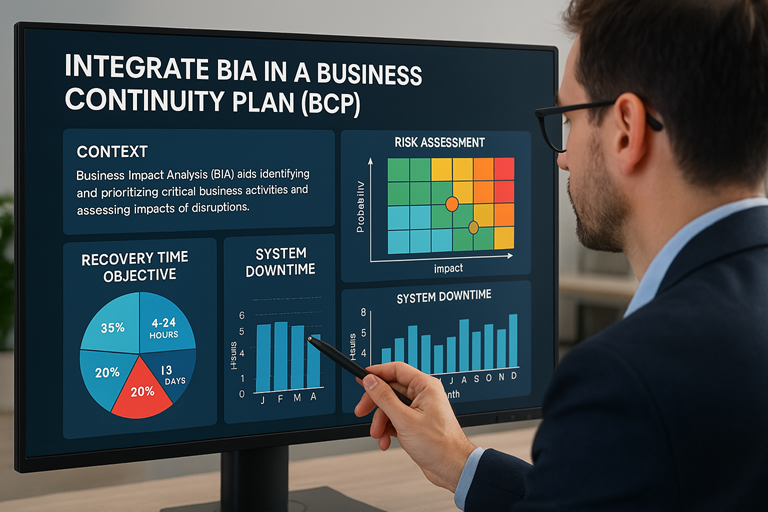
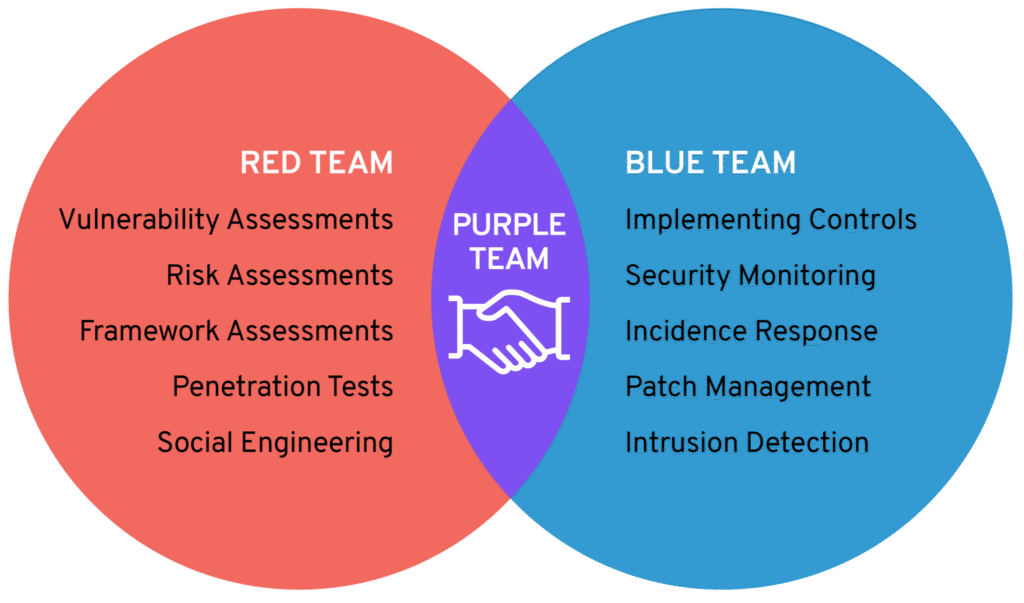
Reading Time: 3 minutesThe 2025 IT risk landscape is defined by the industrialization of cyber threats and the obsolescence of traditional, reactive security postures. Adversaries now leverage AI-driven attack platforms, operate sophisticated Ransomware-as-a-Service (RaaS) ecosystems, and systematically exploit global supply chains.