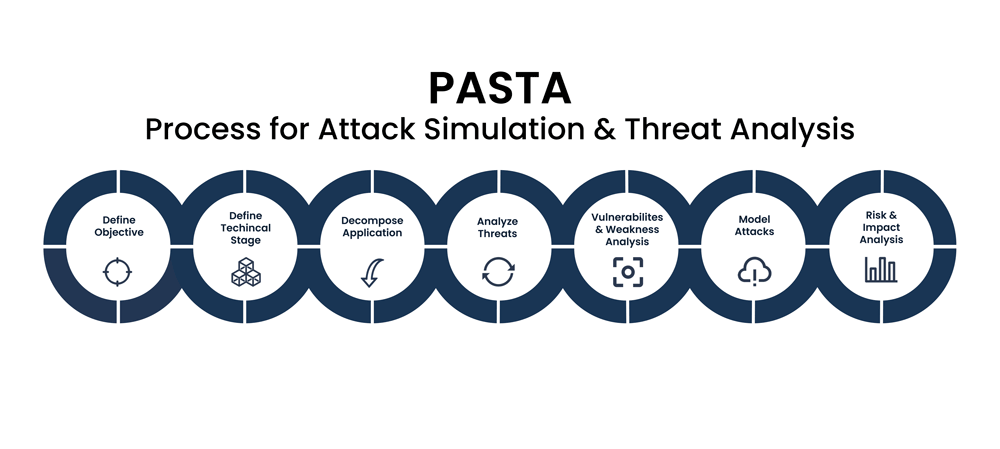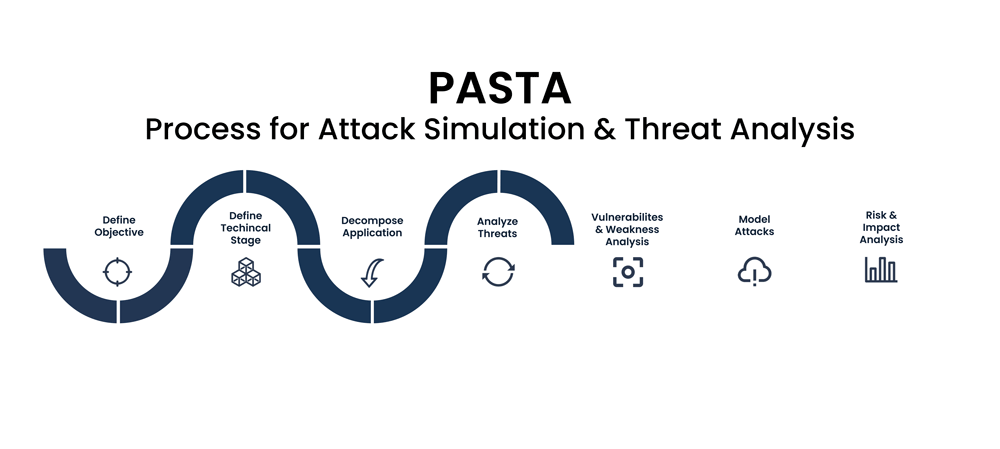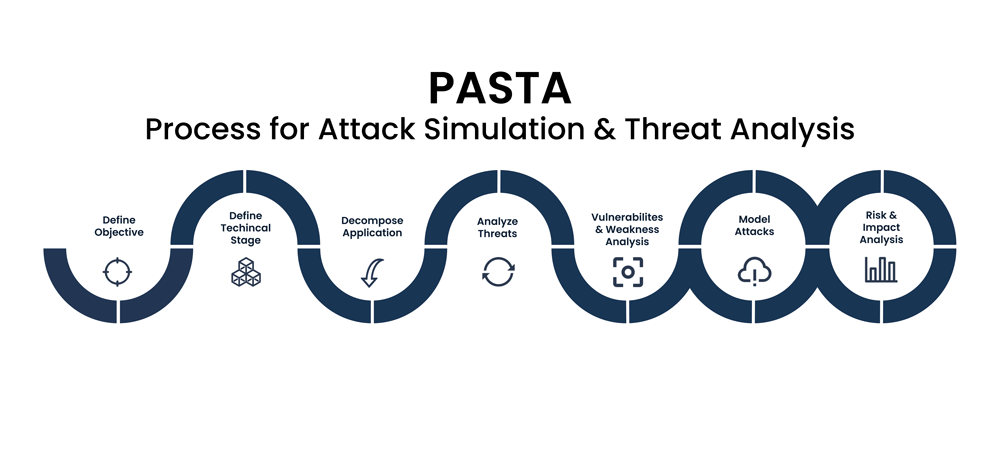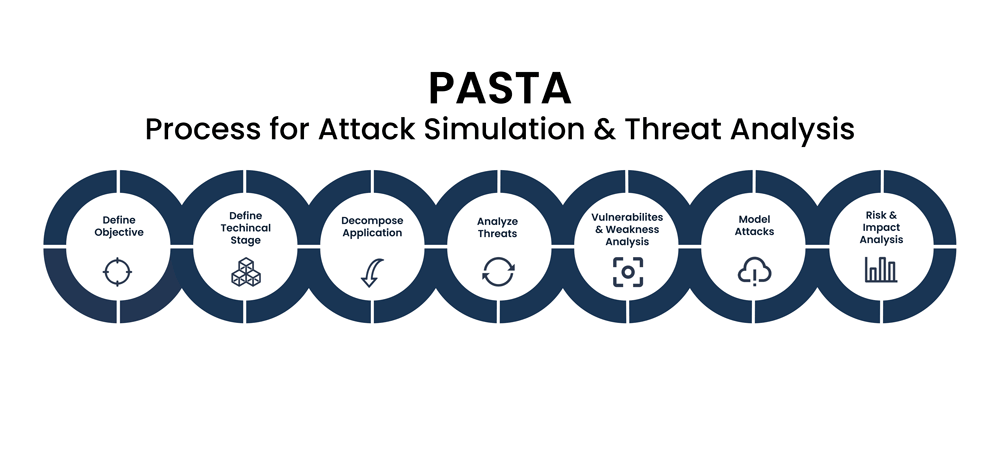
Reading Time: 4 minutesThis document outlines the PASTA-SOC framework, a structured methodology to evolve a Security Operations Center (SOC) from a reactive to a proactive, threat-informed defense model. It operationalizes the seven stages of the Process for Attack Simulation and Threat Analysis (PASTA) by integrating its business-centric principles with the tactical capabilities of modern security technologies, primarily Breach and Attack Simulation (BAS), Threat Intelligence Platforms (TIPs), and Security Orchestration, Automation, and Response (SOAR).





