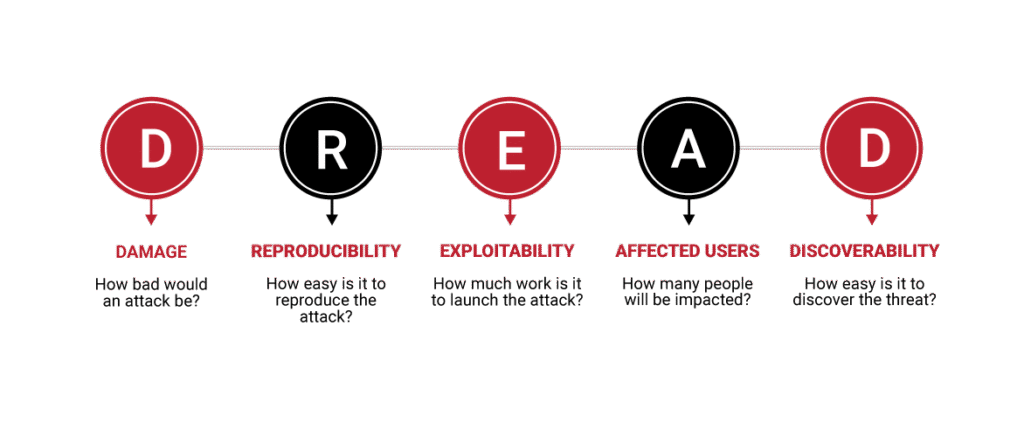
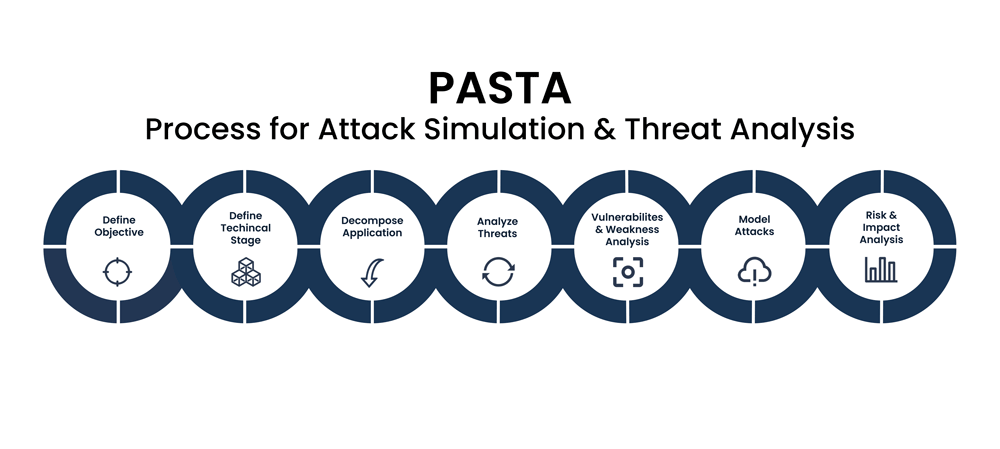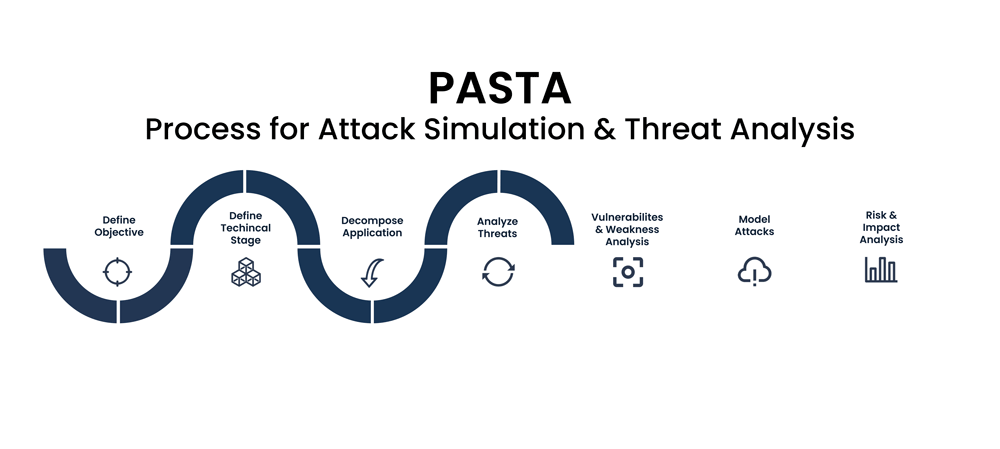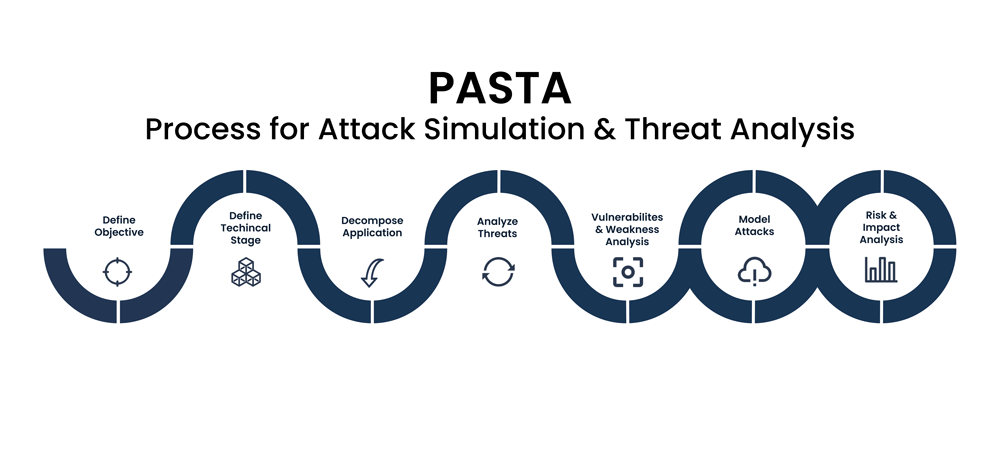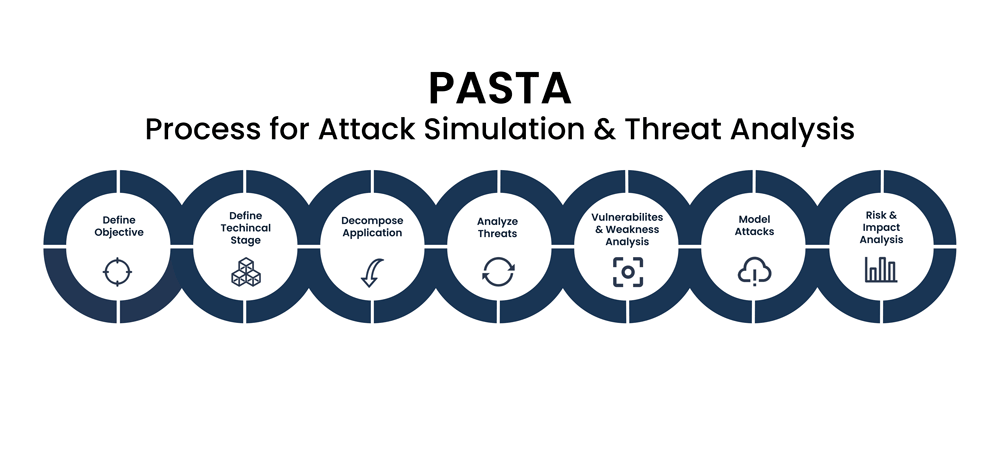
Reading Time: 6 minutesData Loss Prevention (DLP) is a crucial cybersecurity strategy designed to detect and prevent data breaches by blocking unauthorized extraction or exposure of sensitive data. It combines people, processes, and technology to identify, classify, and apply usage policies to sensitive information across endpoints, networks, and cloud platforms (data at rest, in motion, and in use).