
Reading Time: 3 minutesThe Domain Name System (DNS), a Tier-0 critical infrastructure component, was designed for scalability, not security.
Meeting of Brilliant Syche – IT Pro's Corner

Reading Time: 4 minutesStatus: Final Blueprint Summary Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: 25 July 2025 Location: Dhaka, Bangladesh Version: 1.0 1. Executive Summary This document addresses the critical gap identified when organizations mistakenly assume their Read More …

Reading Time: 3 minutesStatus: Summary Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: May 23, 2025 Version: 1.0 1. Executive Summary This document summarizes the architectural blueprint for the CMMI Cybermaturity Platform, an enterprise solution designed to Read More …

Reading Time: 3 minutesStatus: Final Blueprint (Condensed) Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: January 6, 2022 Location: Dhaka, Bangladesh Version: 1.0 (Summary) Executive Summary In a landscape of relentless cyber threats, traditional, point-in-time security assessments are Read More …
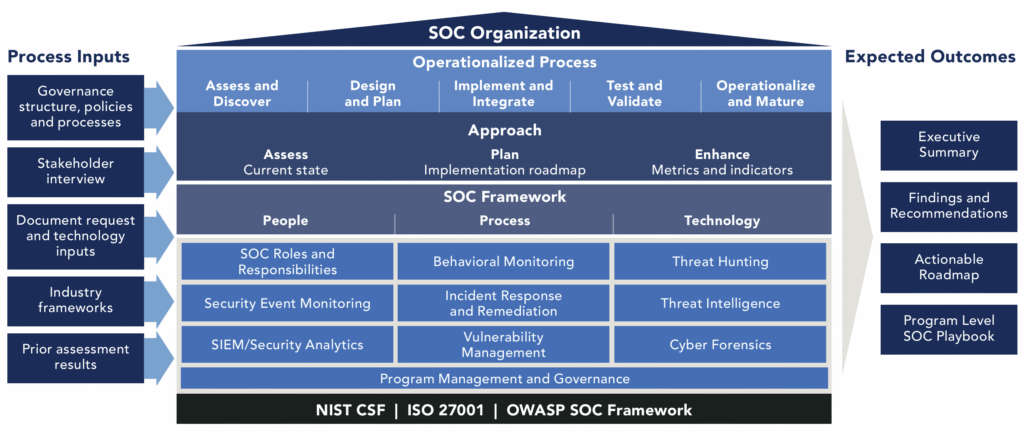
Reading Time: 3 minutesStatus: Final Blueprint Summary Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: April 4, 2024 The SOC as a Strategic Business Enabler The modern Security Operations Center (SOC) has evolved from a technical cost center Read More …

Reading Time: 3 minutesStatus: Summary Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: July 24, 2025 Location: Dhaka, Bangladesh Version: 1.0 1. Executive Summary The modern enterprise faces a critical paradox: the need to defend against costly Read More …

Reading Time: 4 minutesStatus: Final Blueprint (Summary) Author: Shahab Al Yamin Chawdhury Version: 1.0 1. Executive Summary: The Illusion of a Single Defense In the modern digital landscape, relying solely on a Distributed Denial-of-Service (DDoS) appliance creates a dangerous false sense of security. Read More …
Reading Time: 4 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: May 4, 2024 Location: Dhaka, Bangladesh Version: 1.0 1. Executive Summary Modern enterprises face a paradox: a landscape of abundant cybersecurity frameworks has led Read More …

Reading Time: 3 minutes1.0 Purpose and Mandate This Security Program Aggregate (SPA) document establishes the formal, high-level governance framework for the organization’s security operations. It serves as the central charter, summarizing the policies and principles that are implemented through the comprehensive suite of Read More …

Reading Time: 5 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: August 28, 2024 Location: Dhaka, Bangladesh Version: 1.0 Executive Summary This blueprint provides a strategic framework for developing Security Operations Center (SOC) playbooks to Read More …
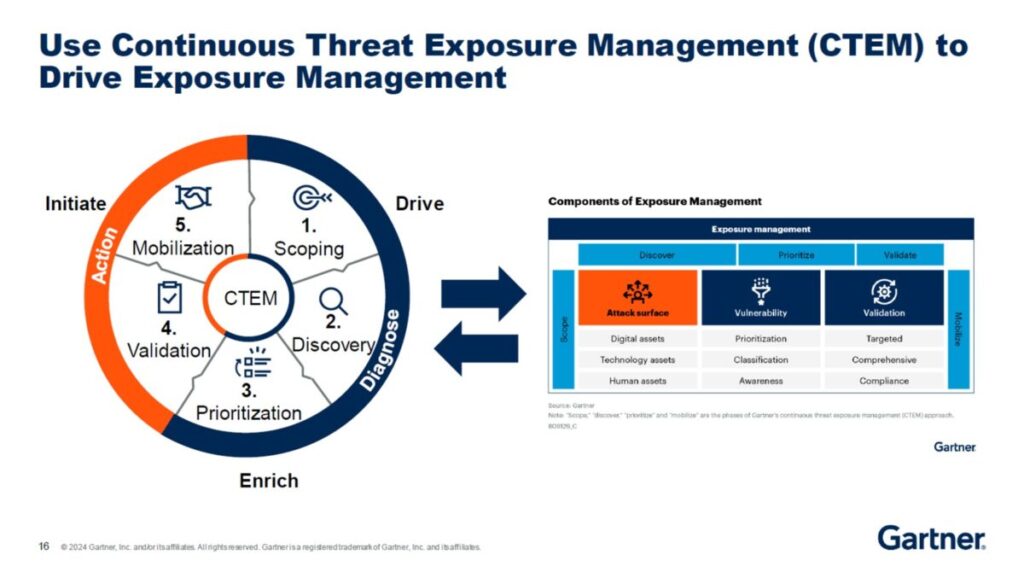
Reading Time: 4 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: July 23, 2025 Location: Dhaka, Bangladesh Version: 1.0 Executive Summary Continuous Threat Exposure Management (CTEM) marks a strategic evolution from reactive, incident-driven security to Read More …

Reading Time: 4 minutesStatus: Condensed Summary Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: February 9, 2024 Location: Dhaka, Bangladesh Version: 1.0 (Summary) Executive Summary The Information Systems (IS) auditing profession faces a seismic transformation driven by relentless Read More …
Reading Time: 3 minutesStatus: Final Blueprint (Summary) Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: September 11, 2023 Location: Dhaka, Bangladesh Version: 1.0 (Summary) Page 1: Strategic Overview & Core Differences 1. The Core Dichotomy: Automated Hygiene vs. Read More …

Reading Time: 4 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: July 21, 2024 Location: Dhaka, Bangladesh Version: 1.0 1.0 Executive Summary 2.0 The Evolving Threat Landscape 3.0 Amplified Risk Factors in Hybrid Environments 4.0 Read More …

Reading Time: 4 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: July 21, 2025 Location: Dhaka, Bangladesh Version: 1.0 1. Executive Summary 2. Deep Dive: Laravel-Specific Concerns for Enterprise Use 3. Deep Dive: MySQL-Specific Concerns Read More …

Reading Time: 8 minutesExecutive Summary The advent of publicly available generative Artificial Intelligence (AI) represents a paradigm shift in the cybersecurity landscape. While offering immense productivity benefits, these tools have also been weaponized, providing adversaries with the means to automate, scale, and enhance Read More …

Reading Time: 4 minutes1. Executive Summary This document presents a strategic blueprint for leveraging the Cyber Attack Kill Chain model as a proactive framework for cybersecurity. The primary objective is to shift organizational defense from a reactive posture to a predictive and preventative Read More …

Reading Time: 5 minutes1.0 Executive Summary This document provides a comprehensive architectural blueprint for the strategic implementation of honeypots within an enterprise network. Honeypots serve as a proactive defense mechanism, acting as decoy systems designed to attract, deceive, and analyze the activities of Read More …

Reading Time: 6 minutes1.0 Executive Summary & 2025-2026 Focus Areas This document provides a comprehensive, multi-domain blueprint of the modern cybersecurity landscape, designed for Chief Information Security Officers (CISOs) and security leadership. It maps critical functions, responsibilities, technologies, and metrics across all major Read More …

Reading Time: 2 minutesIT risk taxonomy is a structured framework that categorizes and classifies various types of IT-related risks, enabling organizations to manage and mitigate these risks effectively. Image Source: https://www.pwc.com/us/en/services/consulting/cybersecurity-risk-regulatory/library/technology-risk.html What is IT Risk Taxonomy? IT risk taxonomy is a systematic approach Read More …

Reading Time: 4 minutesTable of Contents 1. Executive Summary Enterprises embracing two or more public clouds face unique security challenges: inconsistent controls, blind spots, and operational complexity. This report outlines a holistic architecture—spanning network fabric, resilient application platforms, identity-centric access, client-specific handling, and Read More …
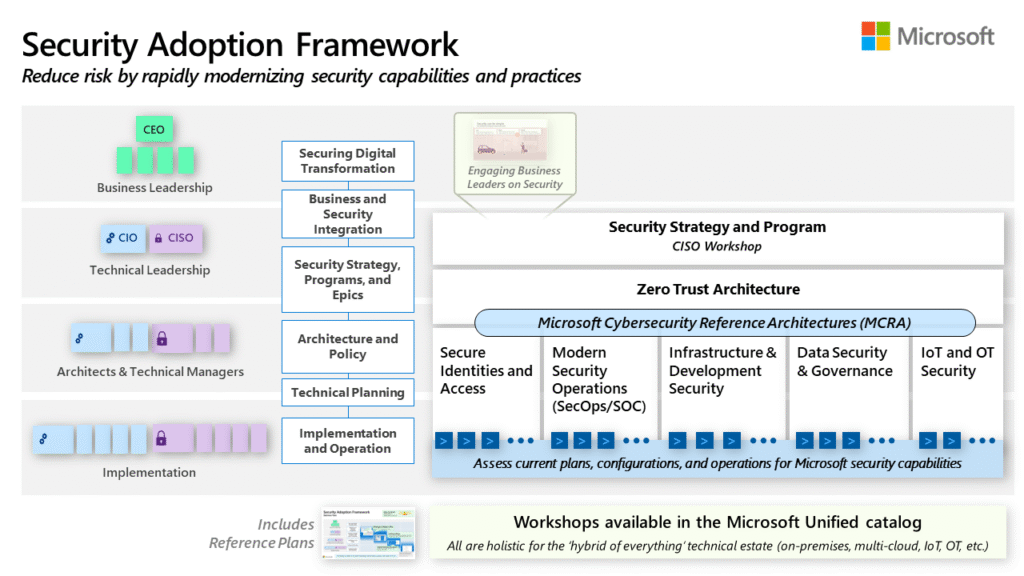
Reading Time: 2 minutesImage source: Security Adoption Resources | Microsoft Learn Traditional security models that rely on a fortified perimeter are no longer enough. With the rise of remote work, cloud applications, and increasingly sophisticated cyber threats, organizations need a more dynamic and Read More …
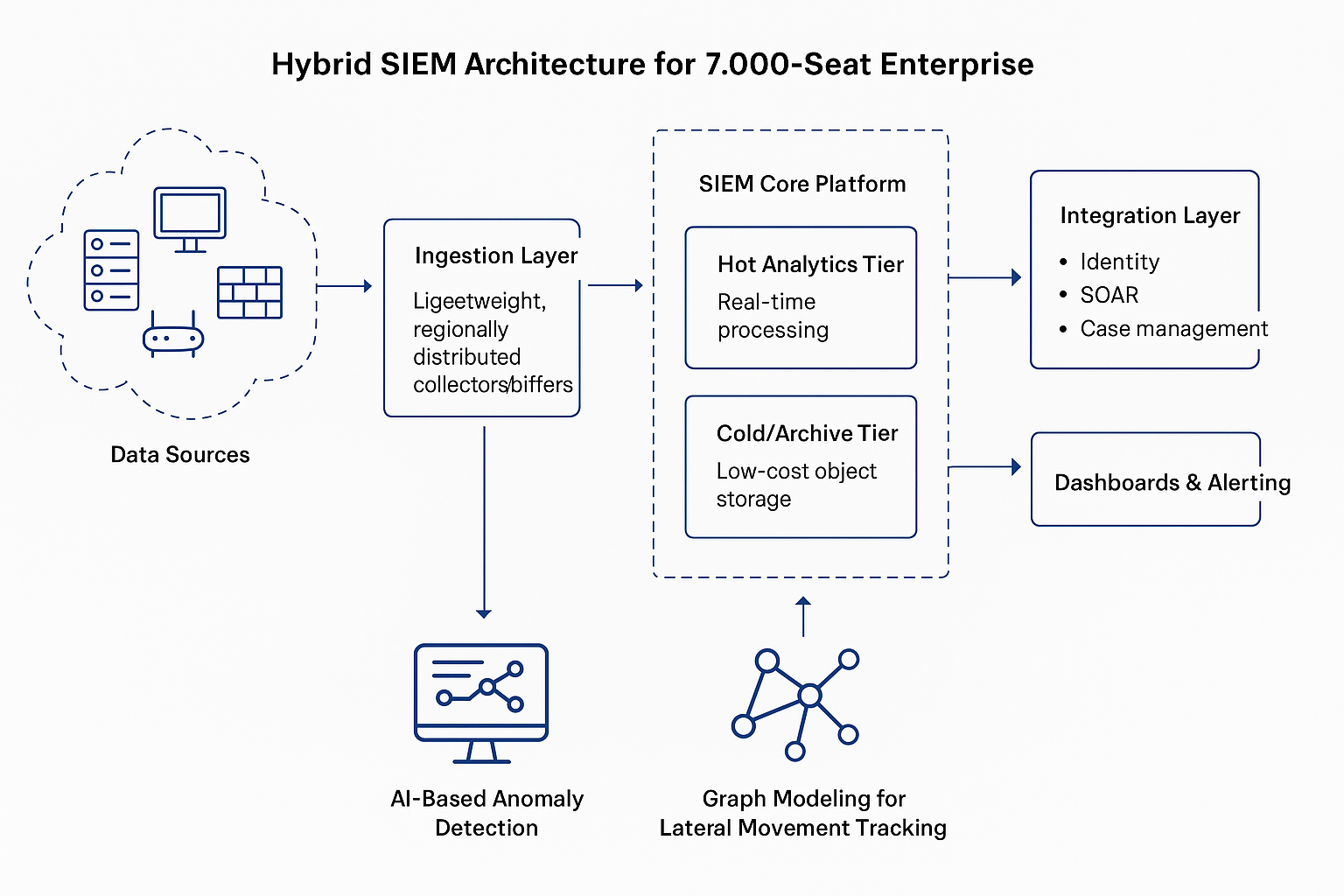
Reading Time: 8 minutesSIEM sizing is all about estimating the resources your Security Information and Event Management (SIEM) system that needs to handle log data efficiently—without overprovisioning or underestimating. The two key metrics used are: To calculate SIEM sizing, you typically keep the Read More …

Reading Time: 3 minutesMachine Identity Security (MIS) or Machine Identity Management (MIM) is another critical aspect of cybersecurity that focuses on securing and managing the digital identities of machines, such as servers, applications, and IoT devices, which is currently overlooked due to lack Read More …
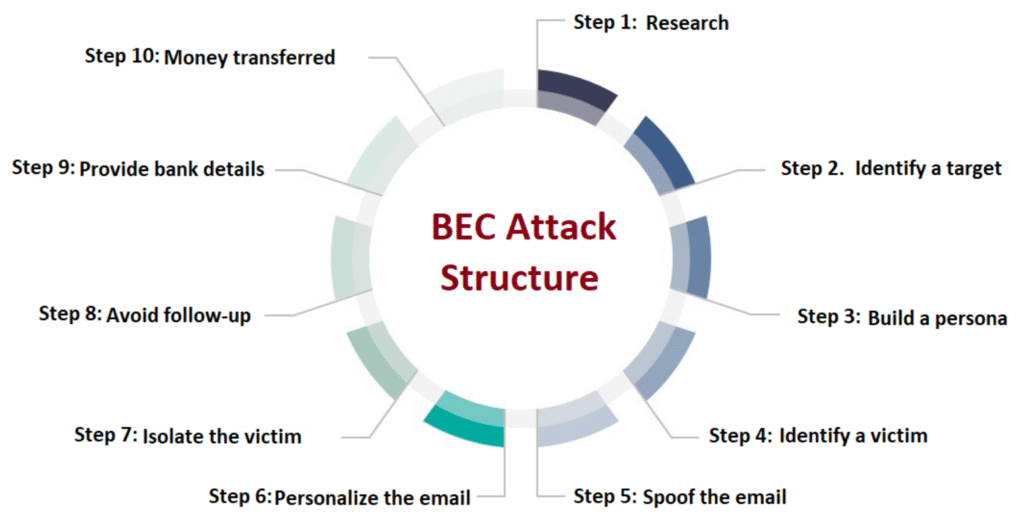
Reading Time: 3 minutesIn a typical Business Email Compromise (BEC) attack, attackers impersonate trusted individuals or organizations to deceive employees into taking harmful actions like transferring funds or sharing sensitive information. This involves research, email manipulation, and often social engineering tactics to exploit Read More …

Reading Time: 3 minutesProtecting an organization from DDoS attacks requires a multi-layered approach, including prevention, mitigation, and continuous monitoring. Here’s a breakdown of key strategies: Image Source: How Cloudflare auto-mitigated world record 3.8 Tbps DDoS attack Strategy 1. Preventing DDoS Attacks 2. Securing Read More …
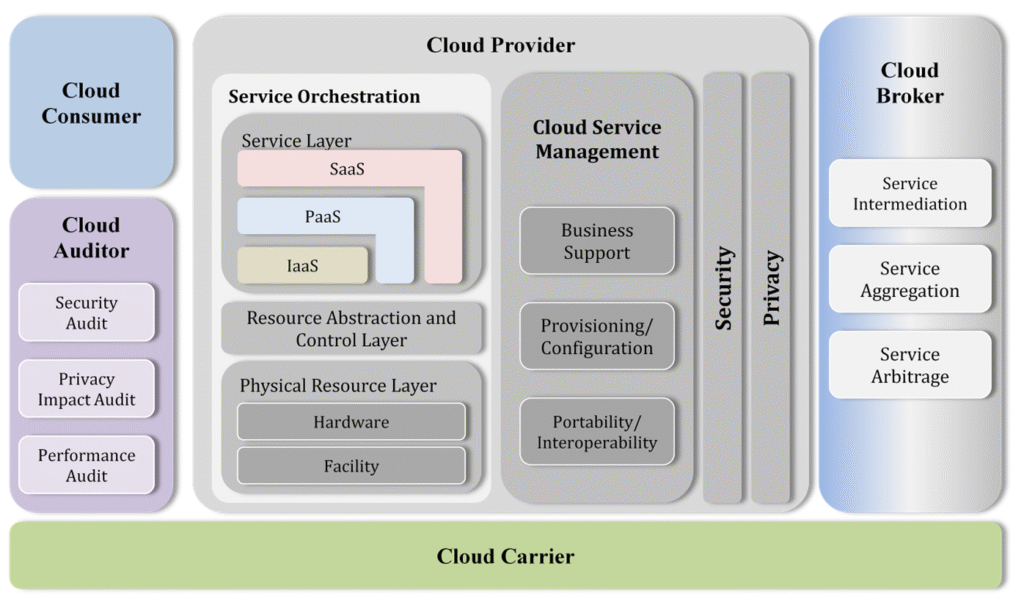
Reading Time: 9 minutesImage Source: https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication500-292.pdf Cloud computing has become an integral part of modern IT infrastructure, enabling enterprises to achieve scalability, efficiency, and agility. This paper discusses the Cloud Computing Reference Architecture (CCRA), including its key adoption requirements, standard bodies of knowledge Read More …
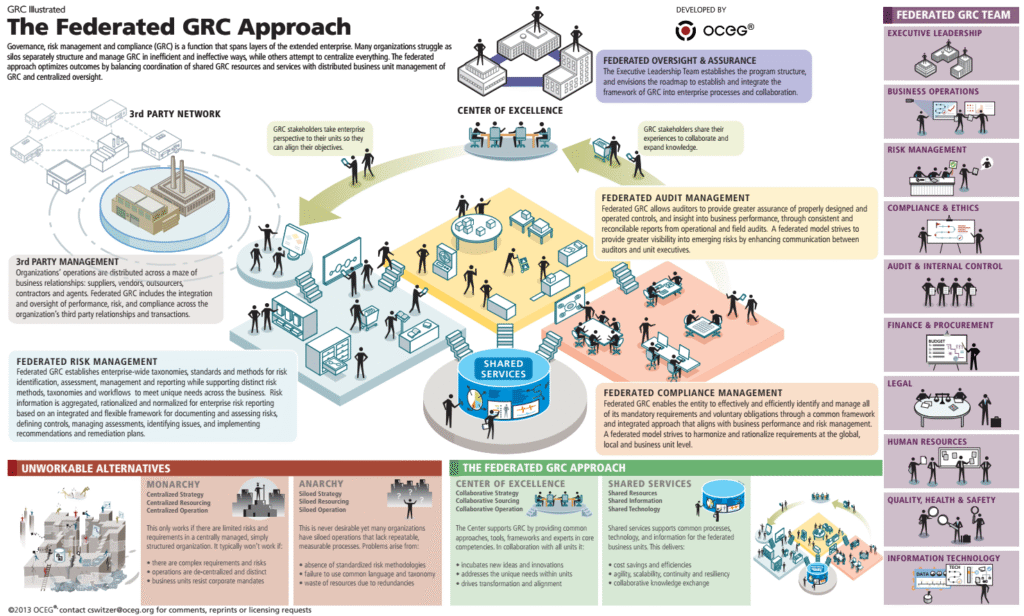
Reading Time: 3 minutesImage source: OCEG Organizations face unprecedented challenges in governance, risk management, and compliance (GRC). The increasing complexity of risks, regulations, and operational demands necessitates a modern, integrated approach to GRC. To connect the dots between risks, compliance, and other GRC elements that Read More …
Reading Time: 2 minutesCISO due diligence refers to the process a CISO (Chief Information Security Officer) and their team conduct to assess the cybersecurity posture and practices of an organization or third party, particularly during mergers and acquisitions, or before entering into a Read More …
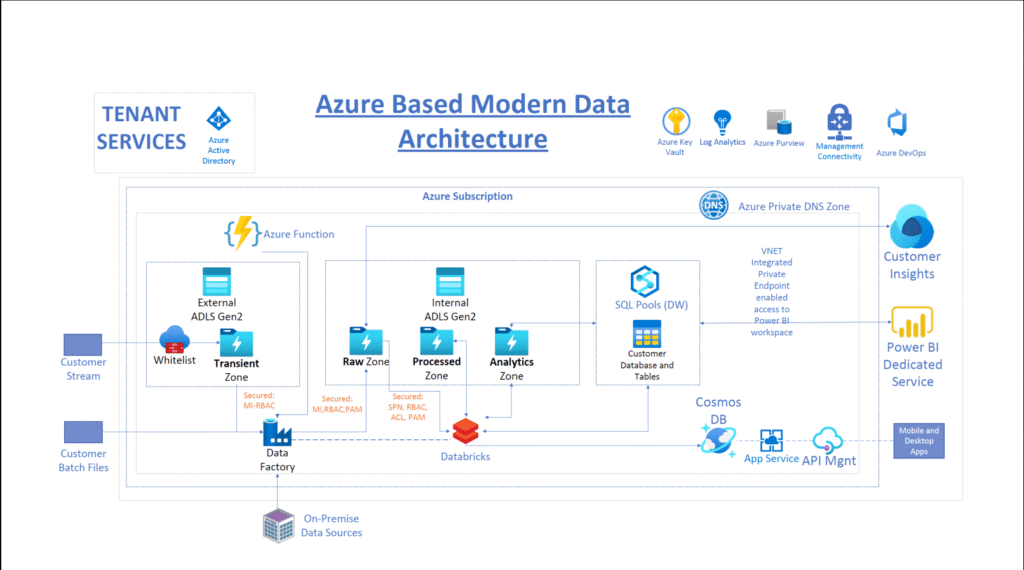
Reading Time: 6 minutesAzure Data Lake Architecture Overview Data Sources: Ingestion Layer: Storage Layer: Processing Layer: Analytics & Serving Layer: Governance & Security: Monitoring: +——————-+ +——————-+ +——————-+ | Data Sources | —> | Ingestion Layer | —> | Storage Layer | | (Structured, Read More …
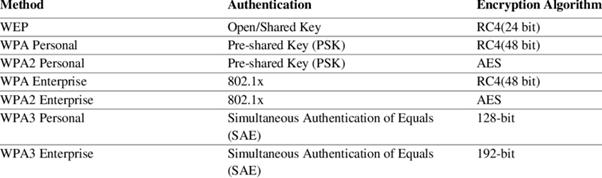
Reading Time: 7 minutesWireless Pre-Shared Key (PSK) A Pre-Shared Key (PSK) is a security mechanism used in Wi-Fi Protected Access (WPA) networks. It works by requiring both the wireless access point (AP) and the client device to have the same secret key before Read More …

Reading Time: 2 minutesEmphasizing on the technology requirements, implementation challenges, and platform security management: Image Source: Transportation | ITS Intelligent Transportation Solutions Overview The Automatic Car Toll System (ACTS) is an innovative solution aimed at streamlining toll collection processes for highways and bridges. Read More …
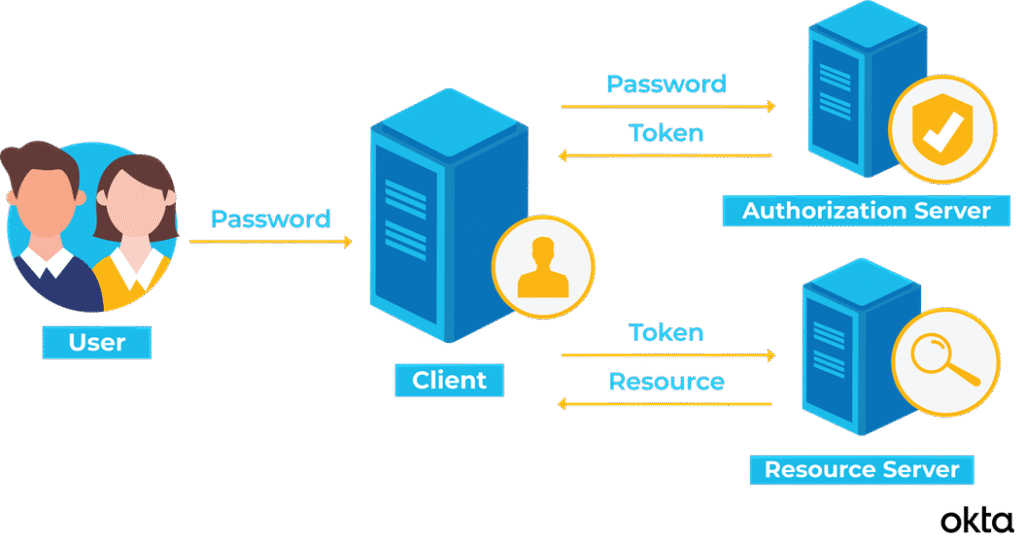
Reading Time: 4 minutesImage Source: TokenBasedAuthentication2.png (3121×1648) Developing an authentication server is a crucial part of building secure applications. Here’s a structured approach to creating one: 1. Define Your Authentication Method: Decide whether you’ll use: 2. Choose a Tech Stack: Pick a language Read More …

Reading Time: 5 minutesImage Source: What is OAuth? (An Introduction to OAuth and OpenID) – The Genius Blog OAuth 2.0 is a widely used authorization framework that enables secure access to resources without exposing user credentials. Here’s a breakdown of its architecture, possibilities Read More …
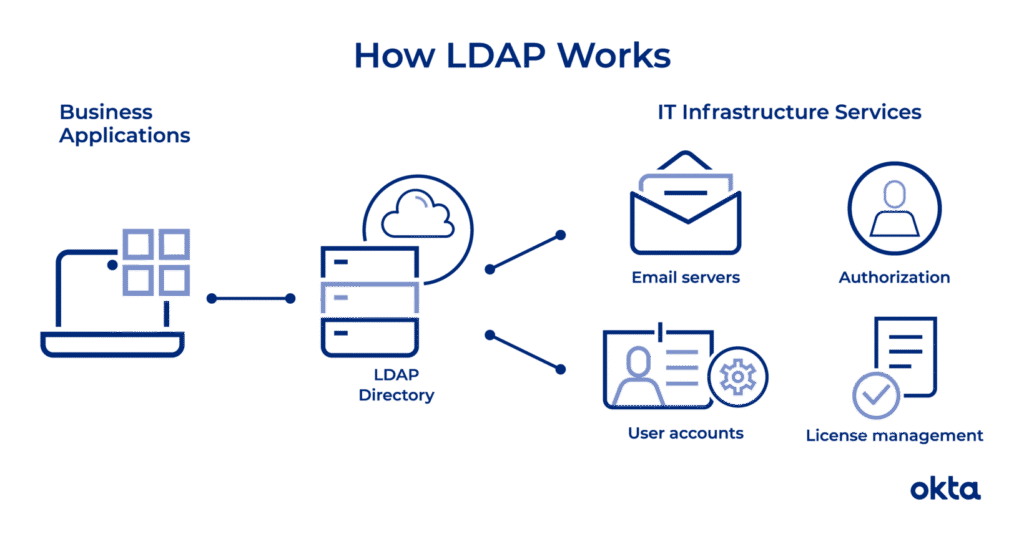
Reading Time: 2 minutesImage Source: https://www.okta.com/identity-101/what-is-ldap/ The Lightweight Directory Access Protocol (LDAP) is an open, vendor-neutral, industry-standard application protocol for accessing and maintaining distributed directory information services over an Internet Protocol (IP) network. LDAP is based on a simpler subset of the standards Read More …

Reading Time: 4 minutesIntroduction In an era where cybersecurity threats are growing in complexity, organizations must continually adapt their security measures to protect sensitive information. Privileged Access Management (PAM) plays a critical role in safeguarding access to high-level accounts that control systems and Read More …
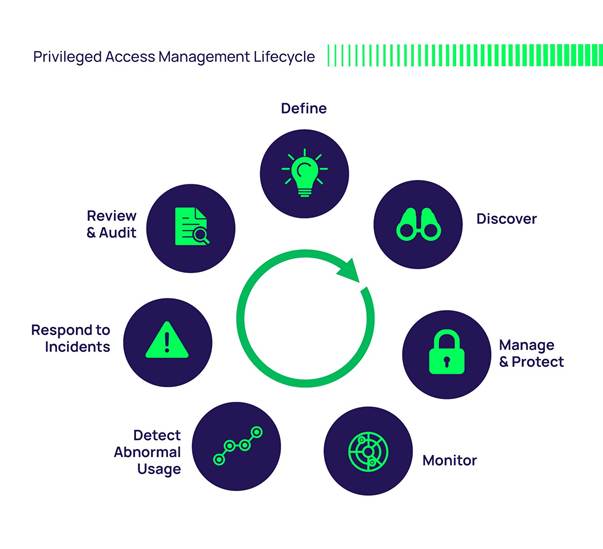
Reading Time: 2 minutesPAM organizes the key aspects of securing high-privilege accounts and activities. It typically includes core functionalities like discovery, control, password management, session monitoring, and compliance, along with components like account discovery, access management, and password vault. The mindmap helps understand Read More …

Reading Time: 2 minutesHID cards, produced by HID Global, are available in various types, primarily based on their technology and functionality. Common types include proximity cards, iCLASS smart cards, and more specialized cards like Seos and Clamshell cards. Here are some key points Read More …

Reading Time: 3 minutes1. Introduction With the increasing threats to online security, securing personal blogs is not just about maintaining content integrity but also ensuring protection against cyberattacks and compliance with global data privacy laws. This paper explores essential security mechanisms and compliance Read More …

Reading Time: 3 minutesA malware signature is a unique identifier used to detect malicious software. It can be a specific sequence of bytes, a file hash, or behavioral patterns that security tools recognize.Malware signatures are patterns or characteristics used to identify and detect Read More …

Reading Time: 2 minutesA mind map for Extended Detection and Response (XDR) can help visualize the components and concepts involved in XDR security solutions. This can be useful for understanding the scope, capabilities, and integration points of XDR, as well as for planning and implementing Read More …

Reading Time: 3 minutesOrganizations face significant challenges in securing sensitive information while navigating an evolving threat landscape. Effective data security practices require a strategic approach to identify, assess, and mitigate risks. This concept paper explores key aspects of data security risks, solutions, and Read More …
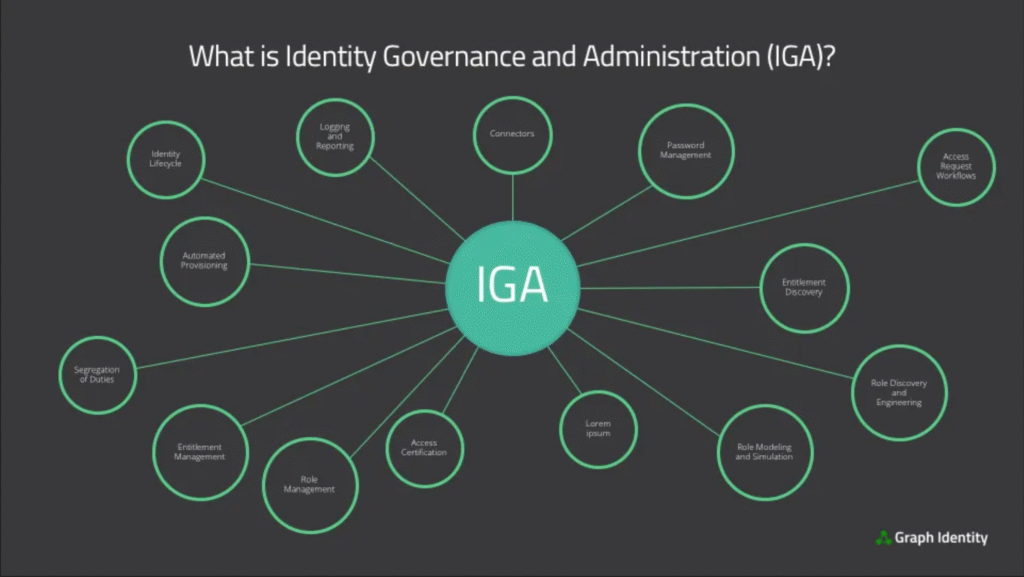
Reading Time: 2 minutesIdentity Governance and Administration (IGA) is a framework that manages and controls user identities and access rights within an organization. It combines identity lifecycle management and access governance to ensure that users have the right access to resources at the Read More …

Reading Time: 3 minutesBackground: with an increasing demand for reliable internet services in Bangladesh, a twenty years ofd ISP aimed to differentiate itself by providing high-quality, affordable services while ensuring efficient operations and scalability. To achieve these goals, Enterprise Architecture (EA) was implemented Read More …
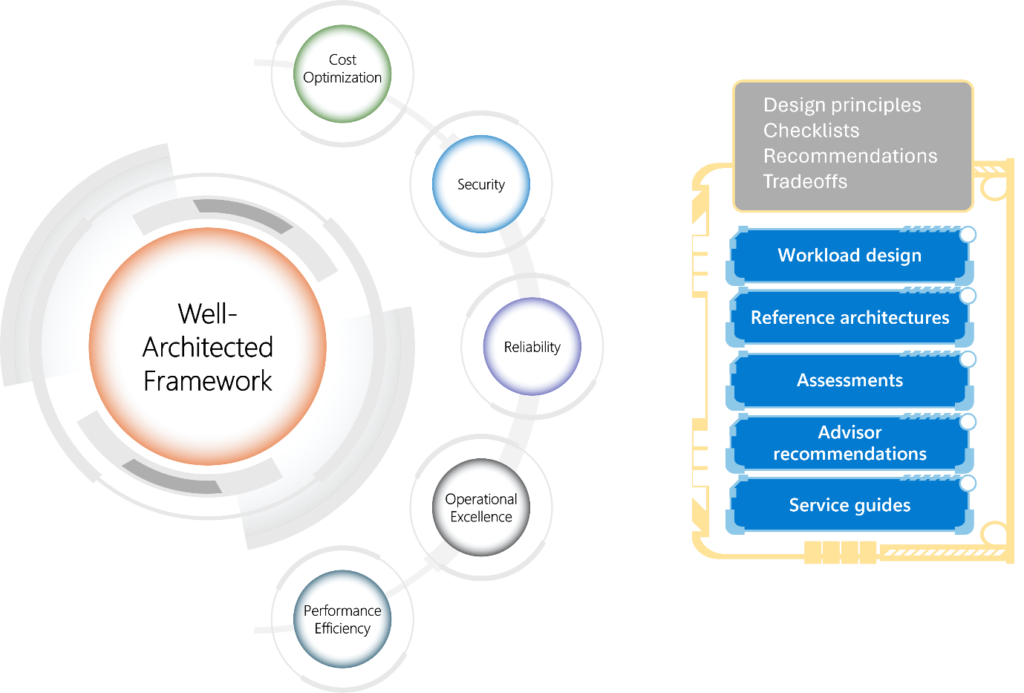
Reading Time: 5 minutesThe Azure Well-Architected Framework (WAF) encompasses five essential tenets that guide solution architects in building robust and efficient workloads on Microsoft Azure: These tenets collectively provide a strong foundation for designing and operating workloads on Azure, ensuring they deliver business value over time. Read More …

Reading Time: 2 minutesImproving threat detection in a Security Operations Center (SOC) involves several strategic and tweaking steps. Here are some defined ways to enhance your SOC’s threat detection capabilities: 1. Implement Advanced Threat Detection Tools 2. Leverage Machine Learning and AI 3. Read More …
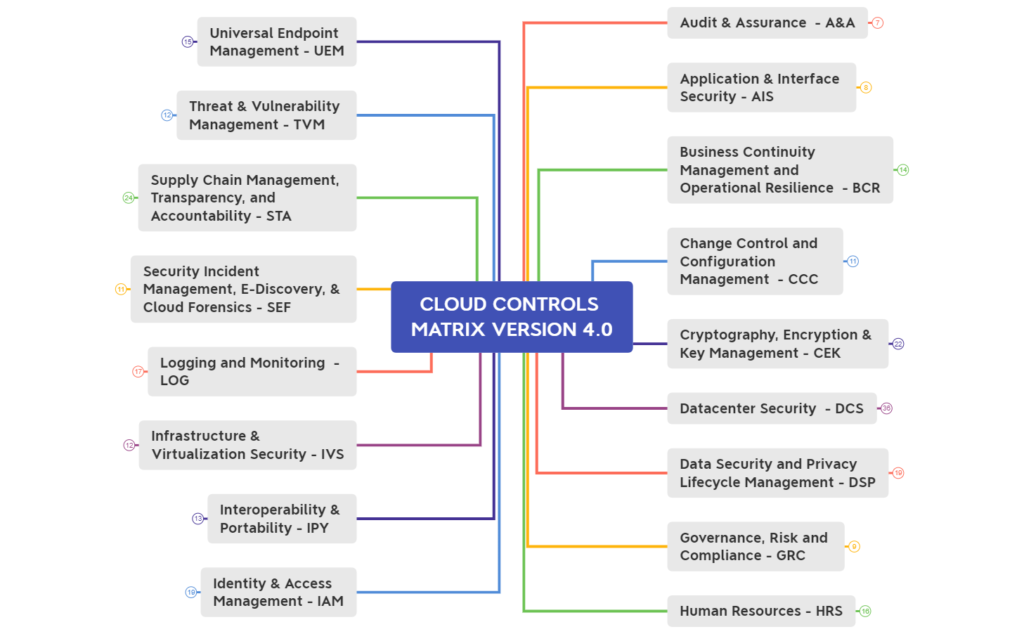
Reading Time: 2 minutesOne of the most effective ways to ensure robust security in the cloud is by implementing a Cloud Security Controls Framework. What is a Cloud Security Controls Framework? A Cloud Security Controls Framework is a structured set of guidelines that Read More …

Reading Time: 2 minutesIn the world of cybersecurity, integration between different tools and platforms is crucial for effective threat detection and response. In this blog post, we will guide you on integrating Wazuh, an open-source Security Information Event Management (SIEM) and XDR solution, with Read More …