
Reading Time: 4 minutesThe modern enterprise faces a critical challenge: the increasing complexity of cloud-native technologies imposes a significant cognitive load on developers, hindering productivity and slowing innovation.
Meeting of Brilliant Syche – IT Pro's Corner

Reading Time: 4 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: July 26, 2024 Version: 1.0 1. The Strategic Imperative for Modernization Application modernization is a critical business initiative to update legacy software, aligning it Read More …

Reading Time: 4 minutesStatus: Final Blueprint (Summary) Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: October 10, 2022 Version: 1.0 1. Executive Summary The modern enterprise runs on open-source software (OSS), which creates a vast and unmanaged attack Read More …

Reading Time: 4 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: July 21, 2025 Location: Dhaka, Bangladesh Version: 1.0 1. Executive Summary 2. Deep Dive: Laravel-Specific Concerns for Enterprise Use 3. Deep Dive: MySQL-Specific Concerns Read More …

Reading Time: 3 minutesMachine Identity Security (MIS) or Machine Identity Management (MIM) is another critical aspect of cybersecurity that focuses on securing and managing the digital identities of machines, such as servers, applications, and IoT devices, which is currently overlooked due to lack Read More …
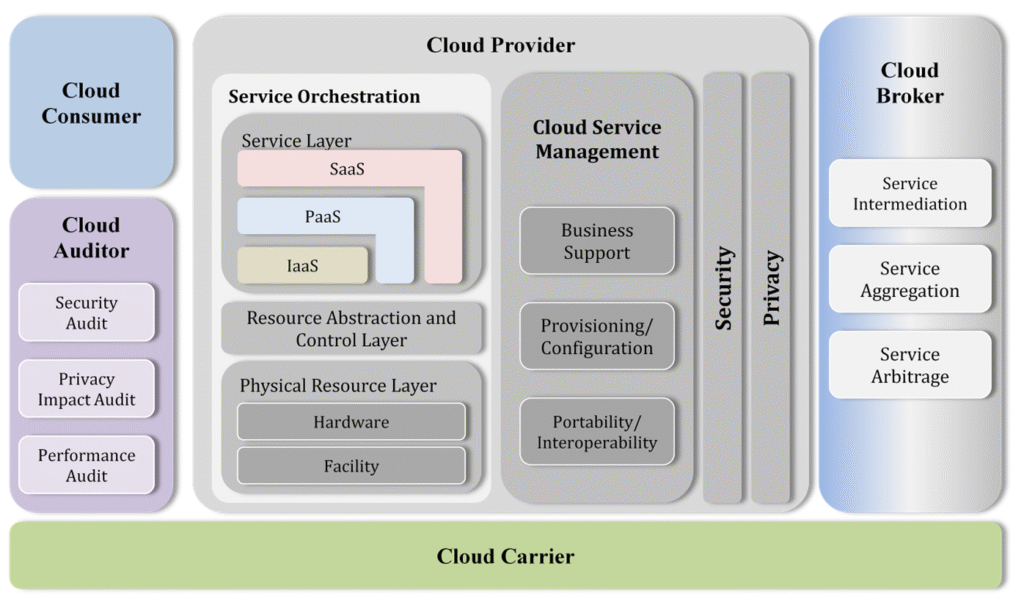
Reading Time: 9 minutesImage Source: https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication500-292.pdf Cloud computing has become an integral part of modern IT infrastructure, enabling enterprises to achieve scalability, efficiency, and agility. This paper discusses the Cloud Computing Reference Architecture (CCRA), including its key adoption requirements, standard bodies of knowledge Read More …
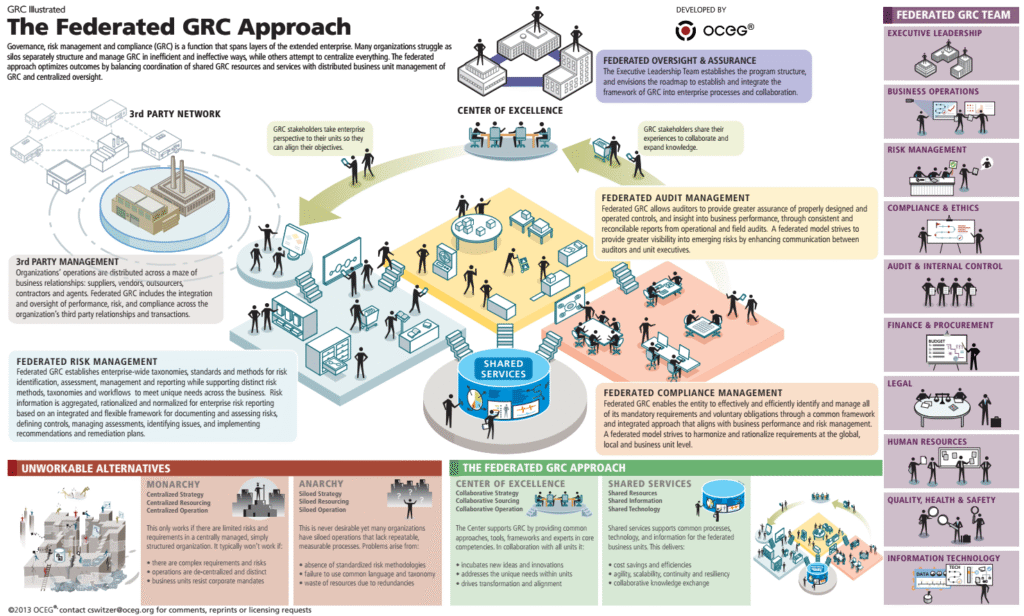
Reading Time: 3 minutesImage source: OCEG Organizations face unprecedented challenges in governance, risk management, and compliance (GRC). The increasing complexity of risks, regulations, and operational demands necessitates a modern, integrated approach to GRC. To connect the dots between risks, compliance, and other GRC elements that Read More …
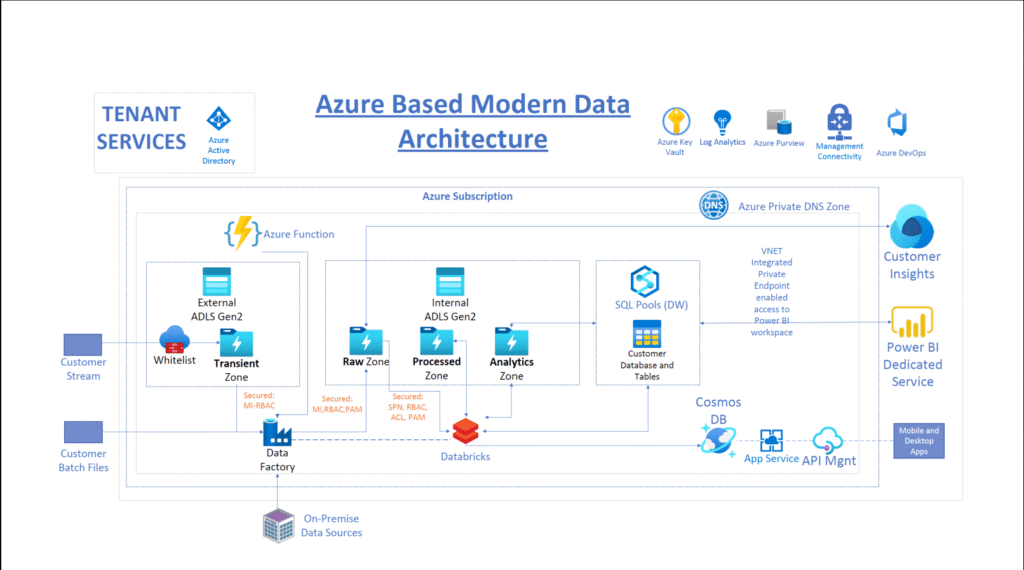
Reading Time: 6 minutesAzure Data Lake Architecture Overview Data Sources: Ingestion Layer: Storage Layer: Processing Layer: Analytics & Serving Layer: Governance & Security: Monitoring: +——————-+ +——————-+ +——————-+ | Data Sources | —> | Ingestion Layer | —> | Storage Layer | | (Structured, Read More …

Reading Time: 2 minutesEmphasizing on the technology requirements, implementation challenges, and platform security management: Image Source: Transportation | ITS Intelligent Transportation Solutions Overview The Automatic Car Toll System (ACTS) is an innovative solution aimed at streamlining toll collection processes for highways and bridges. Read More …
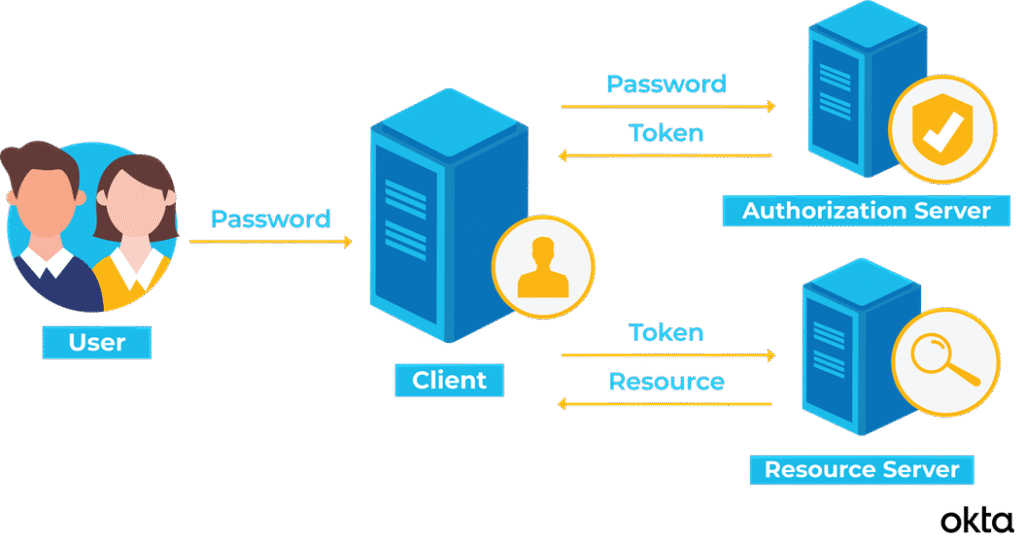
Reading Time: 4 minutesImage Source: TokenBasedAuthentication2.png (3121×1648) Developing an authentication server is a crucial part of building secure applications. Here’s a structured approach to creating one: 1. Define Your Authentication Method: Decide whether you’ll use: 2. Choose a Tech Stack: Pick a language Read More …

Reading Time: 5 minutesImage Source: What is OAuth? (An Introduction to OAuth and OpenID) – The Genius Blog OAuth 2.0 is a widely used authorization framework that enables secure access to resources without exposing user credentials. Here’s a breakdown of its architecture, possibilities Read More …
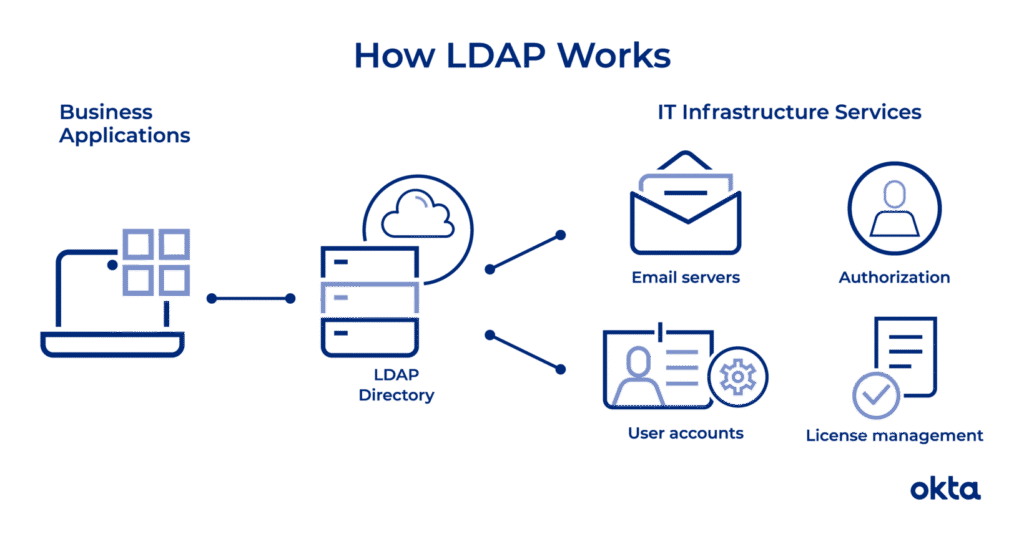
Reading Time: 2 minutesImage Source: https://www.okta.com/identity-101/what-is-ldap/ The Lightweight Directory Access Protocol (LDAP) is an open, vendor-neutral, industry-standard application protocol for accessing and maintaining distributed directory information services over an Internet Protocol (IP) network. LDAP is based on a simpler subset of the standards Read More …
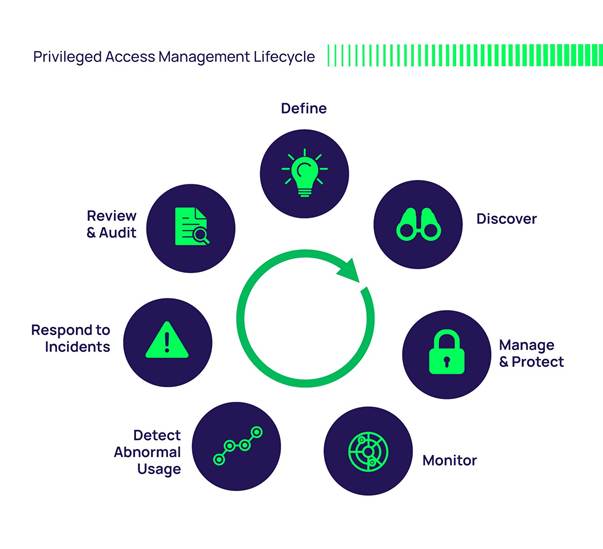
Reading Time: 2 minutesPAM organizes the key aspects of securing high-privilege accounts and activities. It typically includes core functionalities like discovery, control, password management, session monitoring, and compliance, along with components like account discovery, access management, and password vault. The mindmap helps understand Read More …

Reading Time: 3 minutes1. Introduction With the increasing threats to online security, securing personal blogs is not just about maintaining content integrity but also ensuring protection against cyberattacks and compliance with global data privacy laws. This paper explores essential security mechanisms and compliance Read More …

Reading Time: 3 minutesA Data & Analytics Capability Model is a framework that organizations use to assess and improve their ability to leverage data and analytics for better decision-making and business outcomes. It outlines the various skills, processes, and technologies needed to effectively manage, analyze, Read More …

Reading Time: 3 minutesBackground: with an increasing demand for reliable internet services in Bangladesh, a twenty years ofd ISP aimed to differentiate itself by providing high-quality, affordable services while ensuring efficient operations and scalability. To achieve these goals, Enterprise Architecture (EA) was implemented Read More …

Reading Time: 2 minutesA structured outline of a software development team with their titles and job requirements: Software Development Team Requirements Responsibilities: Define product vision, strategy, and roadmap. Gather and prioritize product and customer requirements. Ensure alignment with business goals. Responsibilities: Plan, initiate, Read More …

Reading Time: 3 minutesIf you are an application developer, you know how important security is for your products. You want to protect your users’ data, your reputation, and your bottom line from malicious attacks. But security is not a one-time thing. It is Read More …
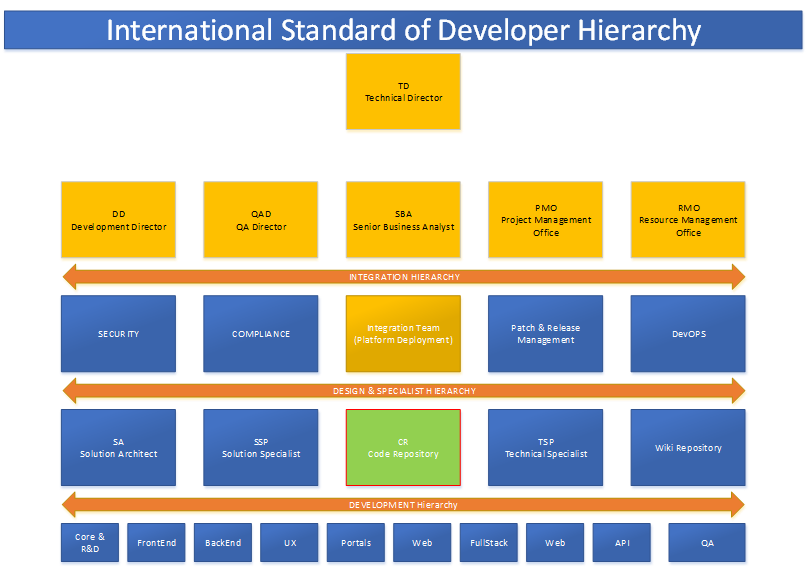
Reading Time: 3 minutesDevelopment Hierarchy Framework Introduction to Secure Development Lifecycle (SDLC) – Discover how integrating security practices into every phase of the software development process can mitigate security risks and protect sensitive data. Learn more in our latest blog post! Benefits of Read More …