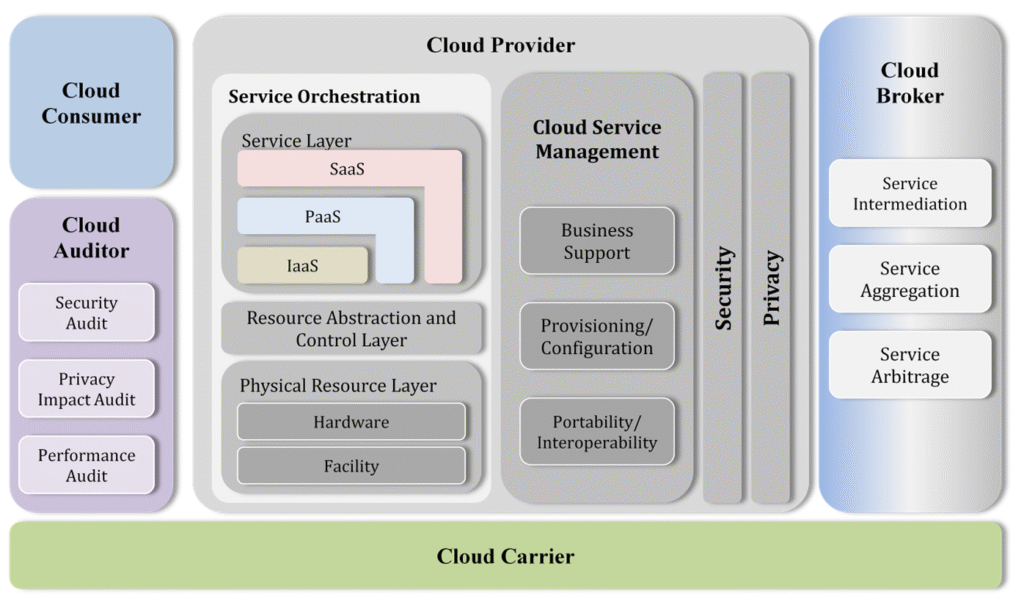
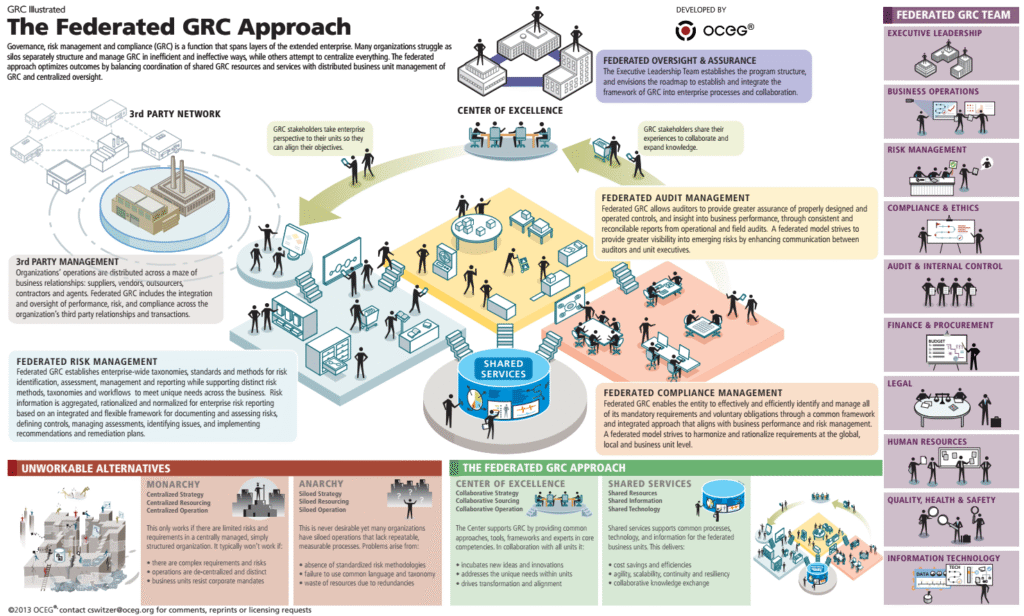
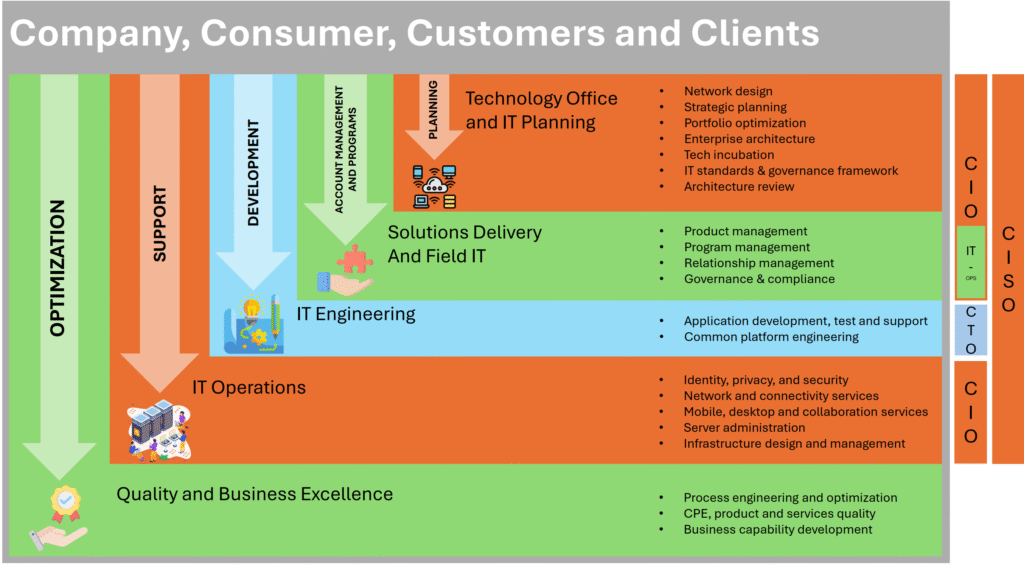
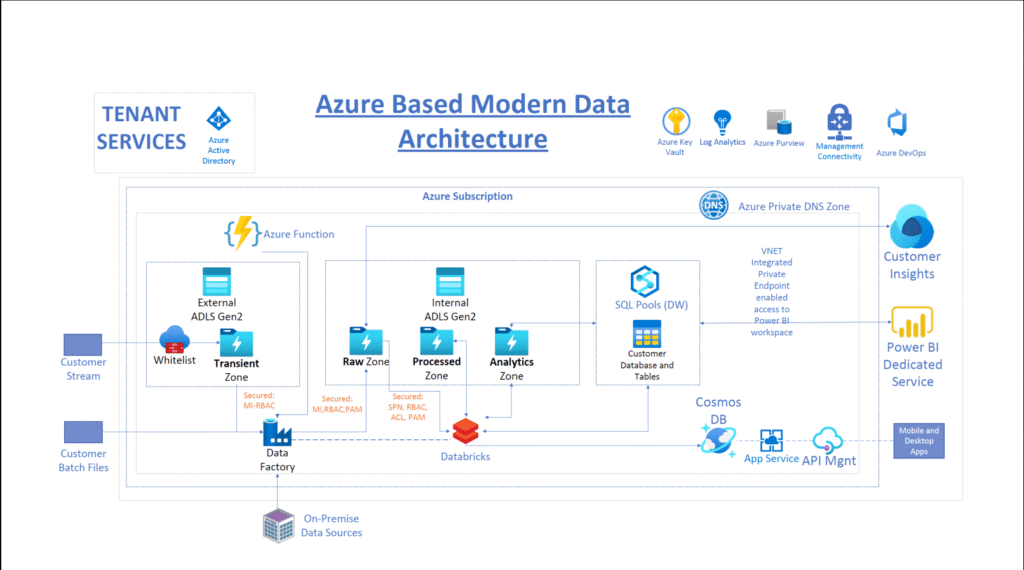
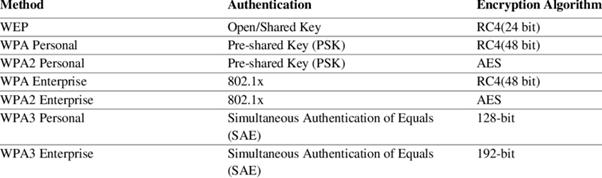
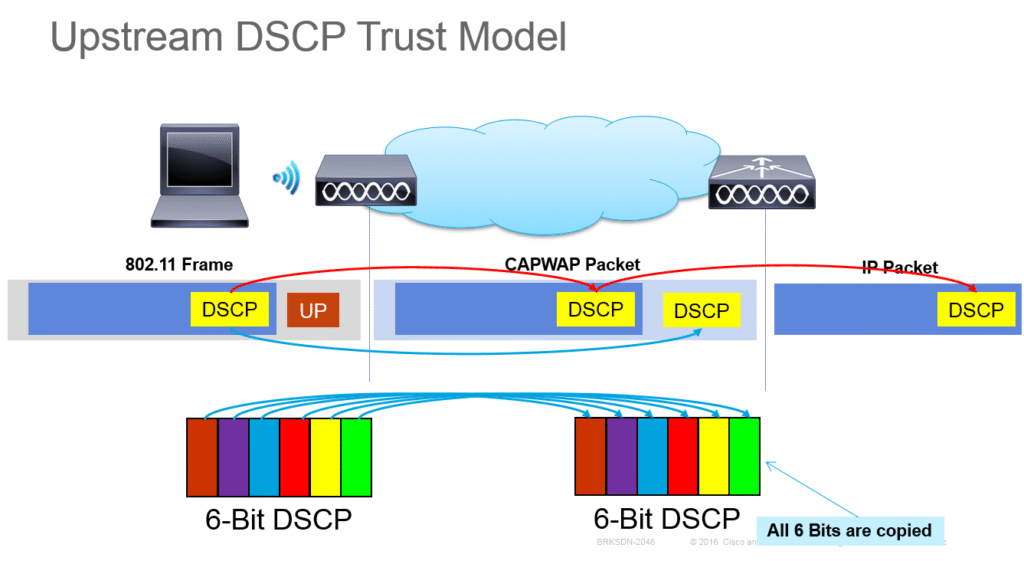
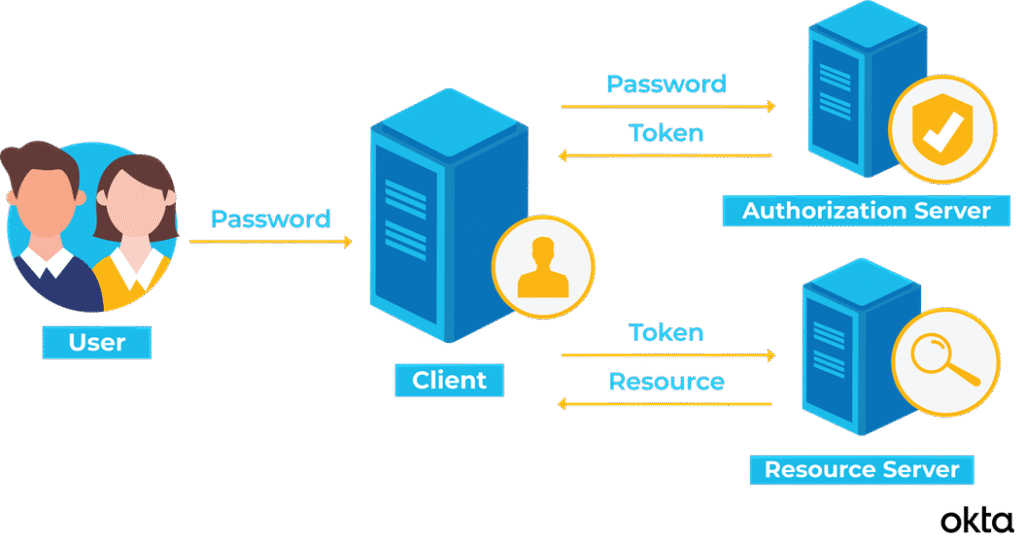
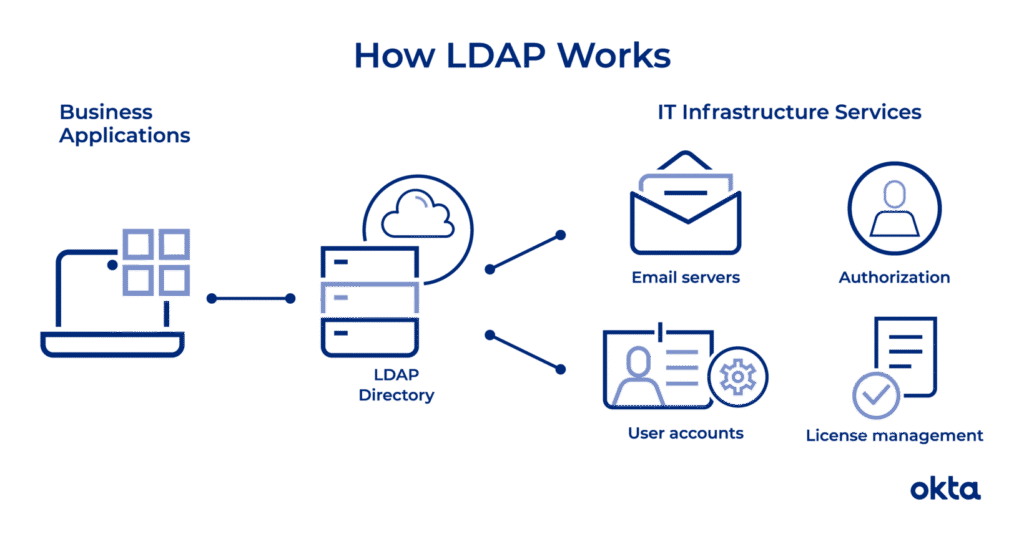
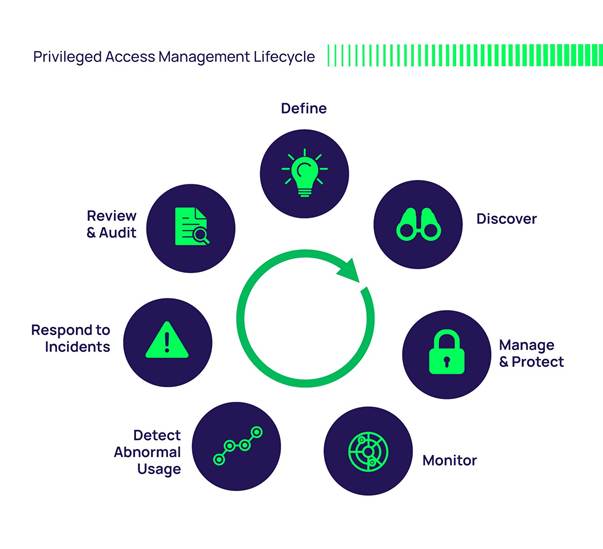
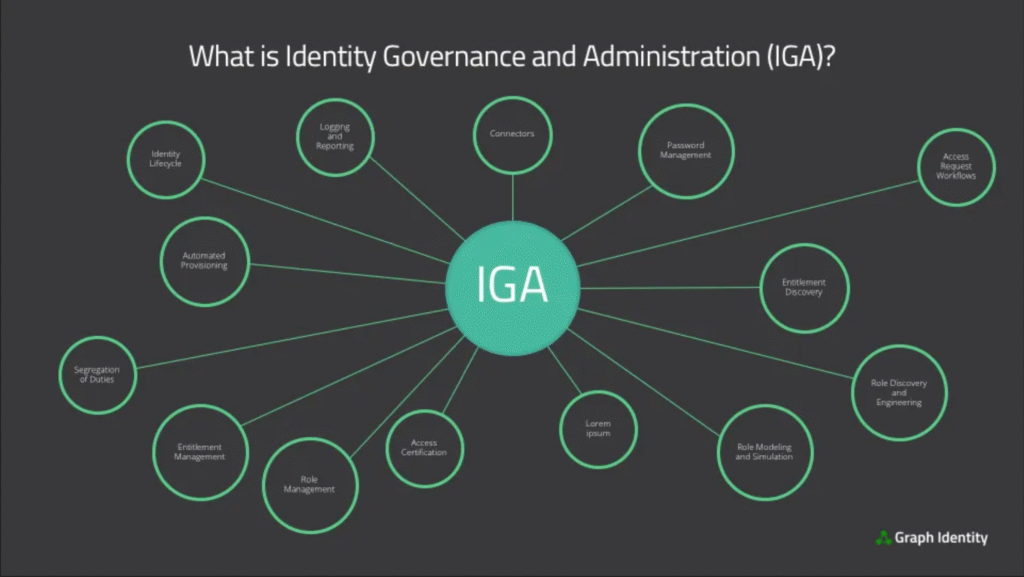
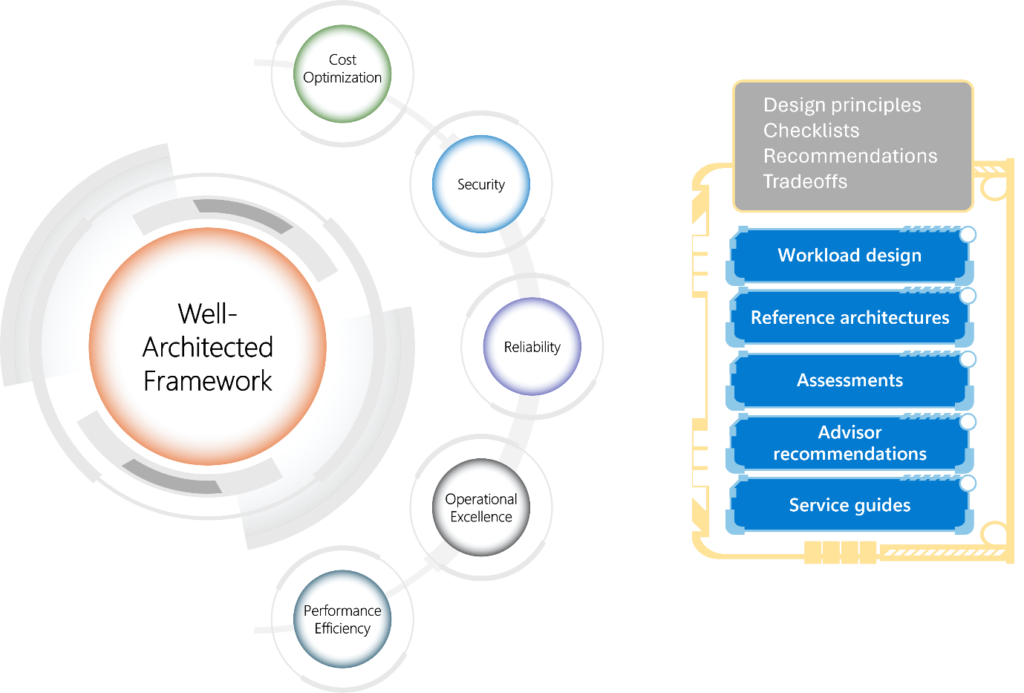
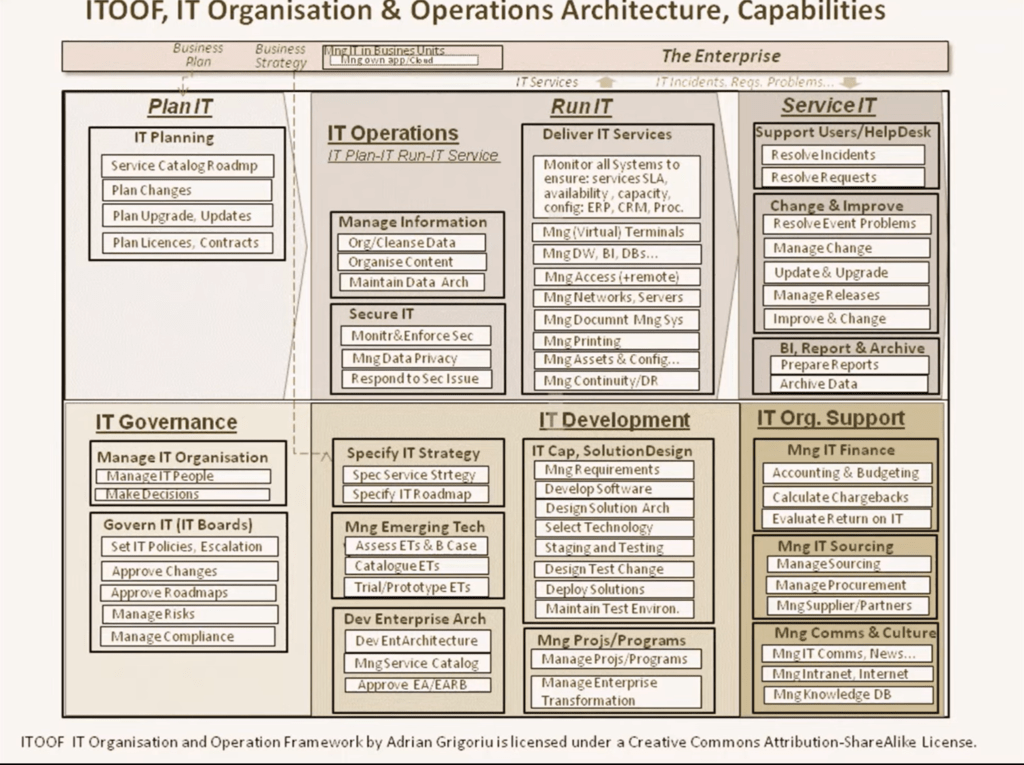
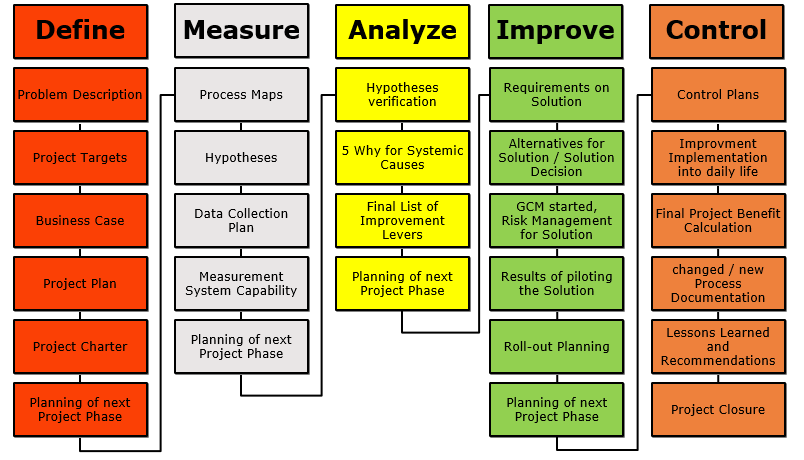
Reading Time: 3 minutesProtecting an organization from DDoS attacks requires a multi-layered approach, including prevention, mitigation, and continuous monitoring. Here’s a breakdown of key strategies: Image Source: How Cloudflare auto-mitigated world record 3.8 Tbps DDoS attack Strategy 1. Preventing DDoS Attacks 2. Securing Read More …