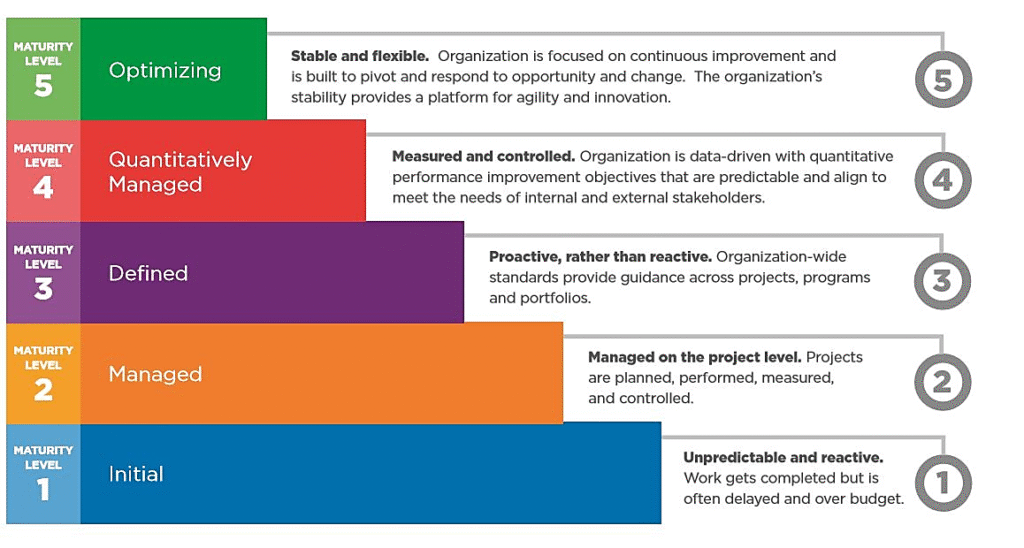
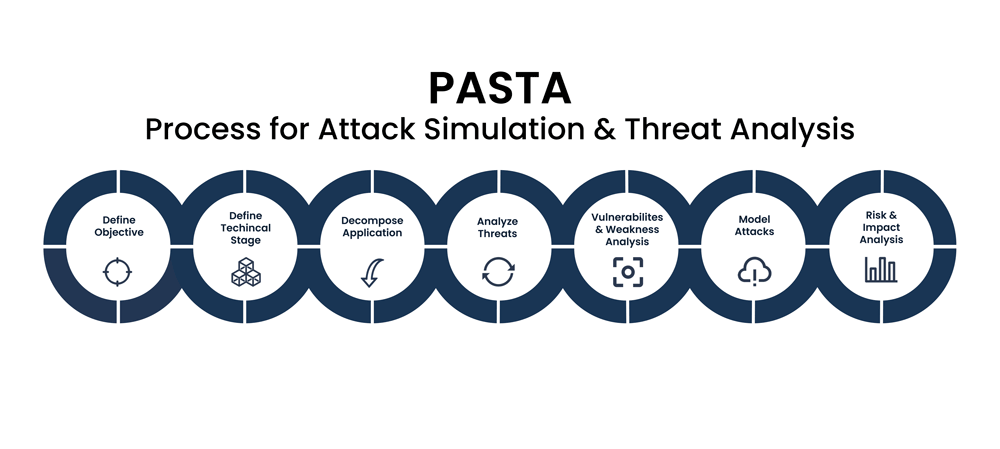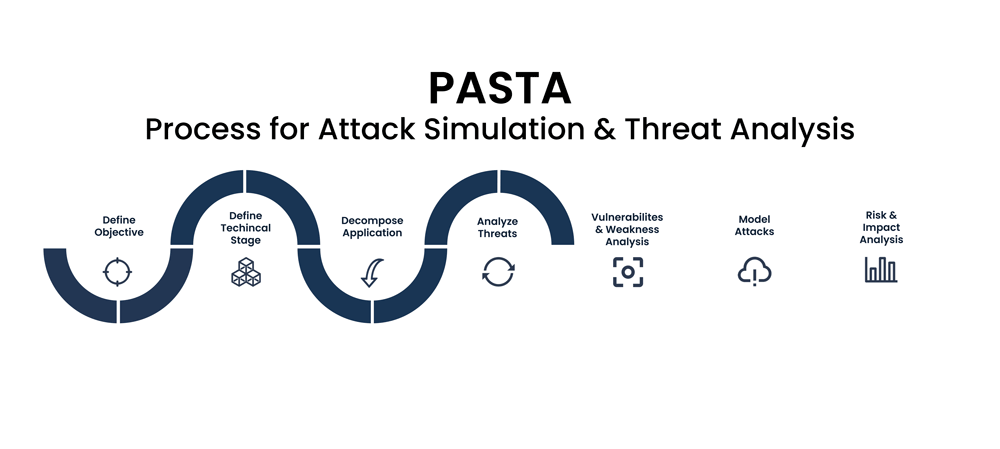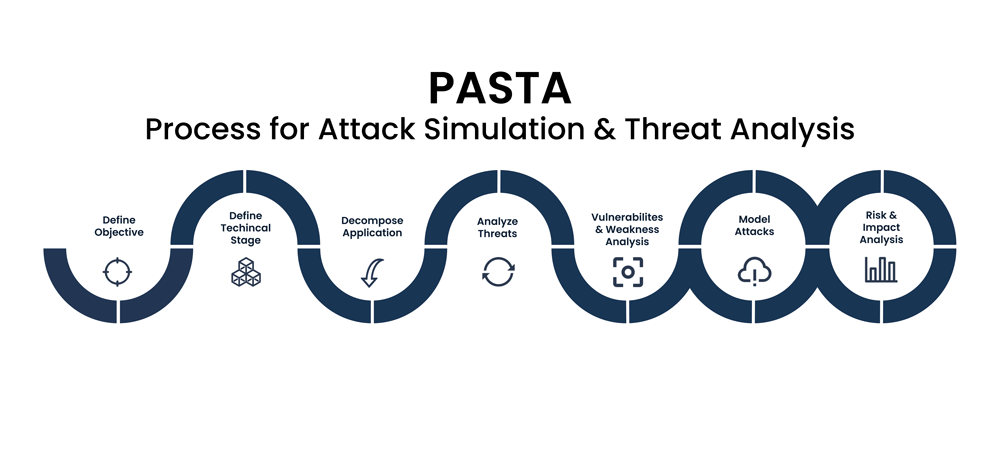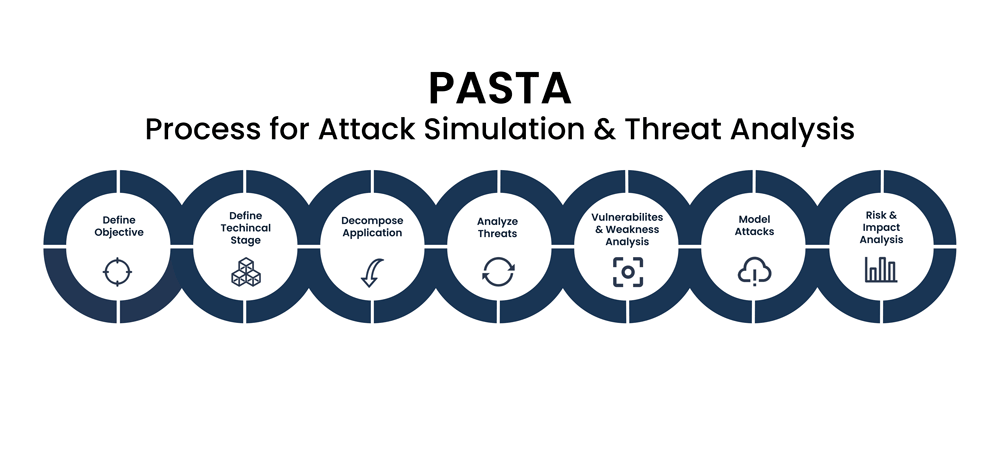
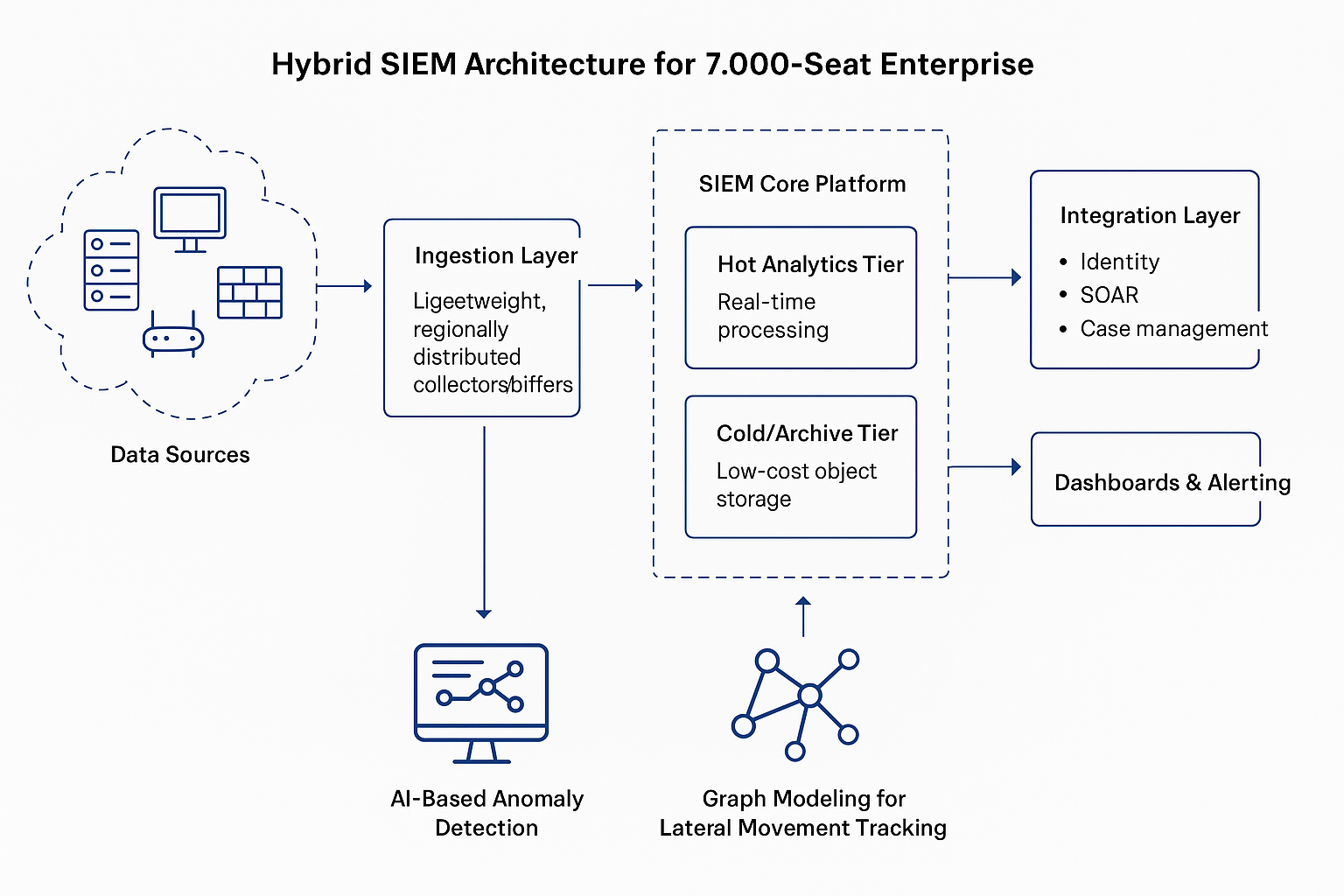
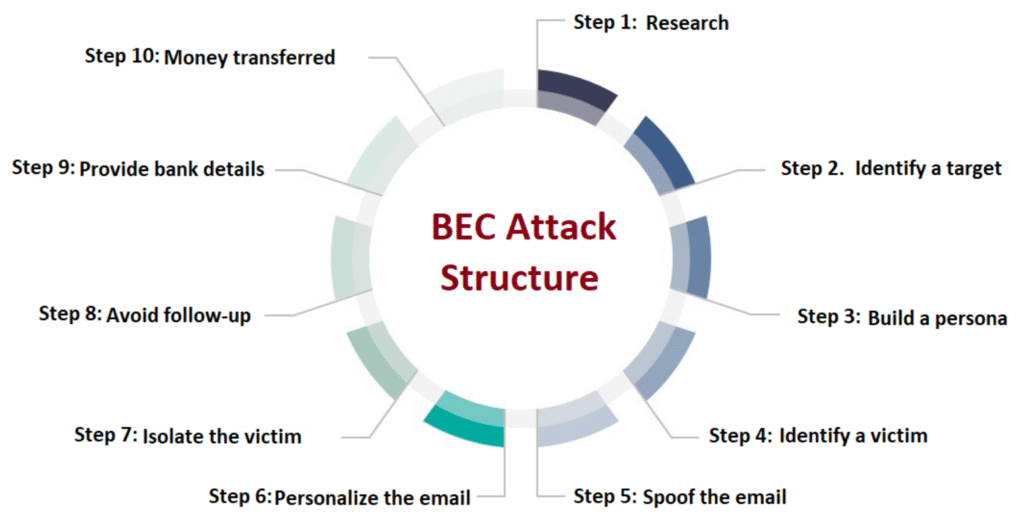
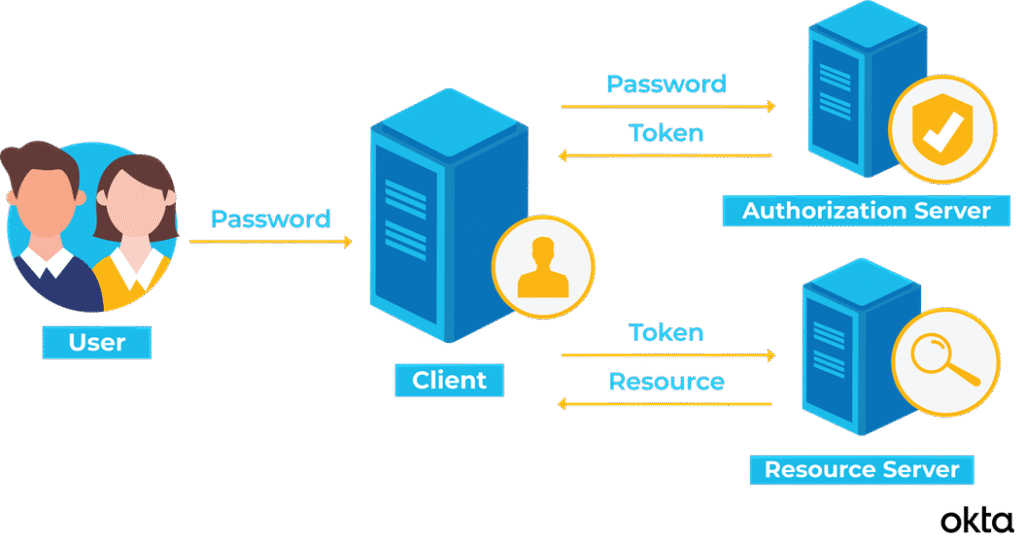
Reading Time: 3 minutesDetection‑as‑Code (DaC) is moving from niche practice to mainstream SOC engineering discipline. By embedding detection logic into CI/CD‑style pipelines, organizations are achieving faster deployment cycles, higher detection accuracy, and measurable reductions in false positives.