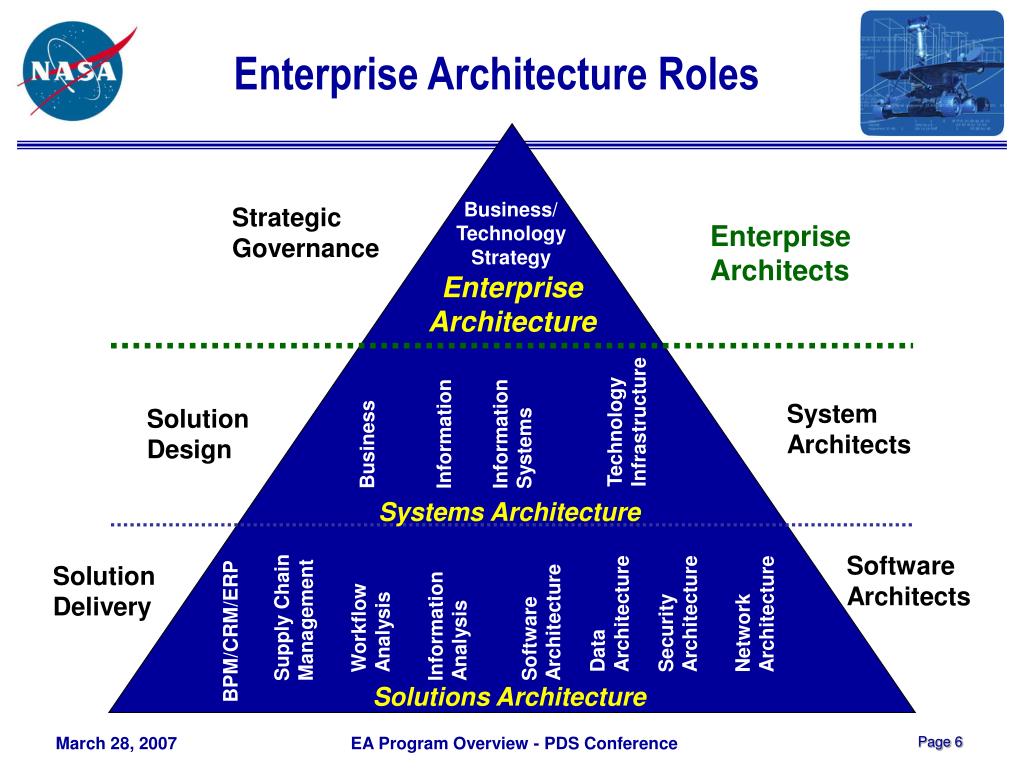
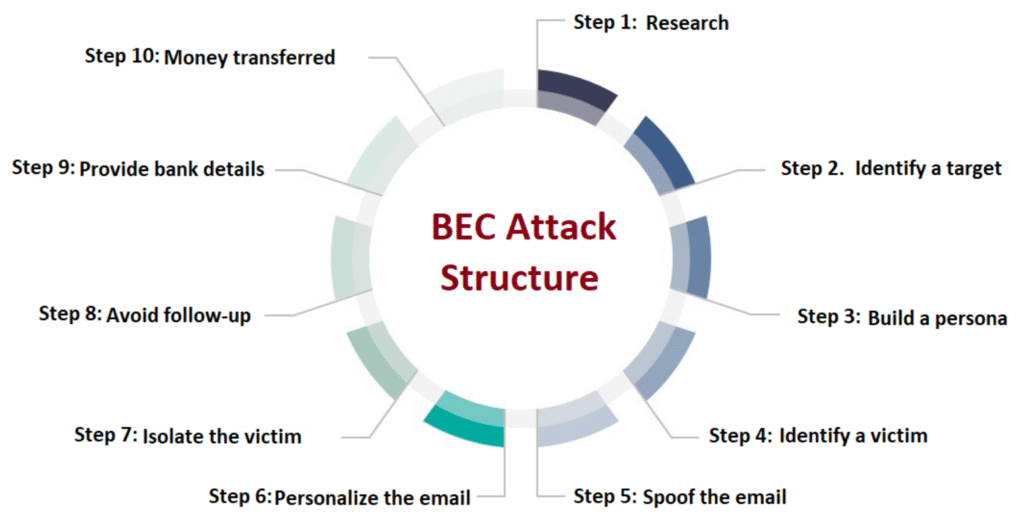
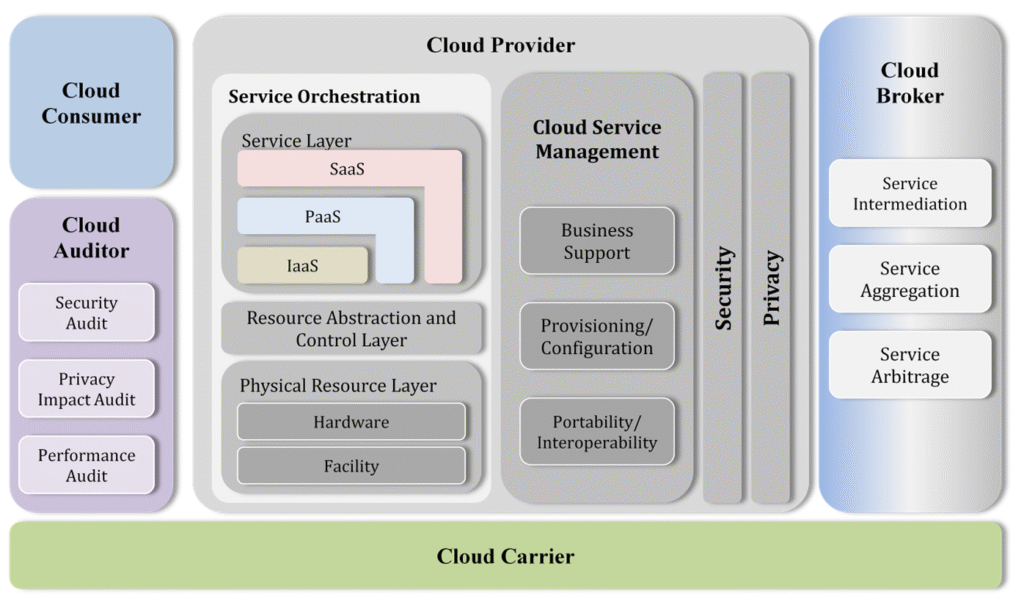
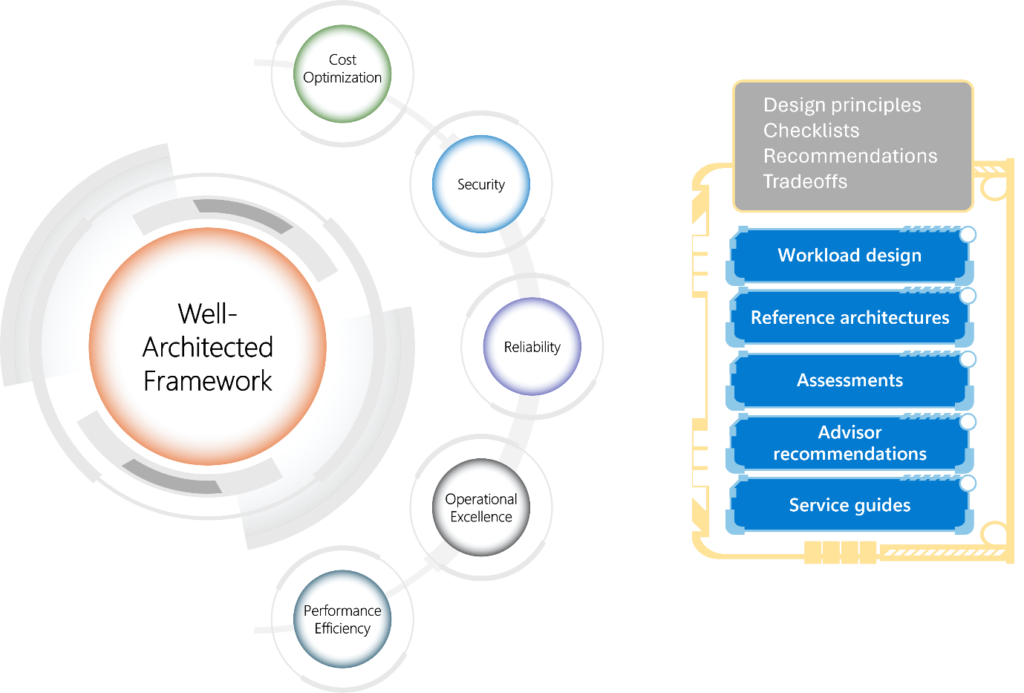
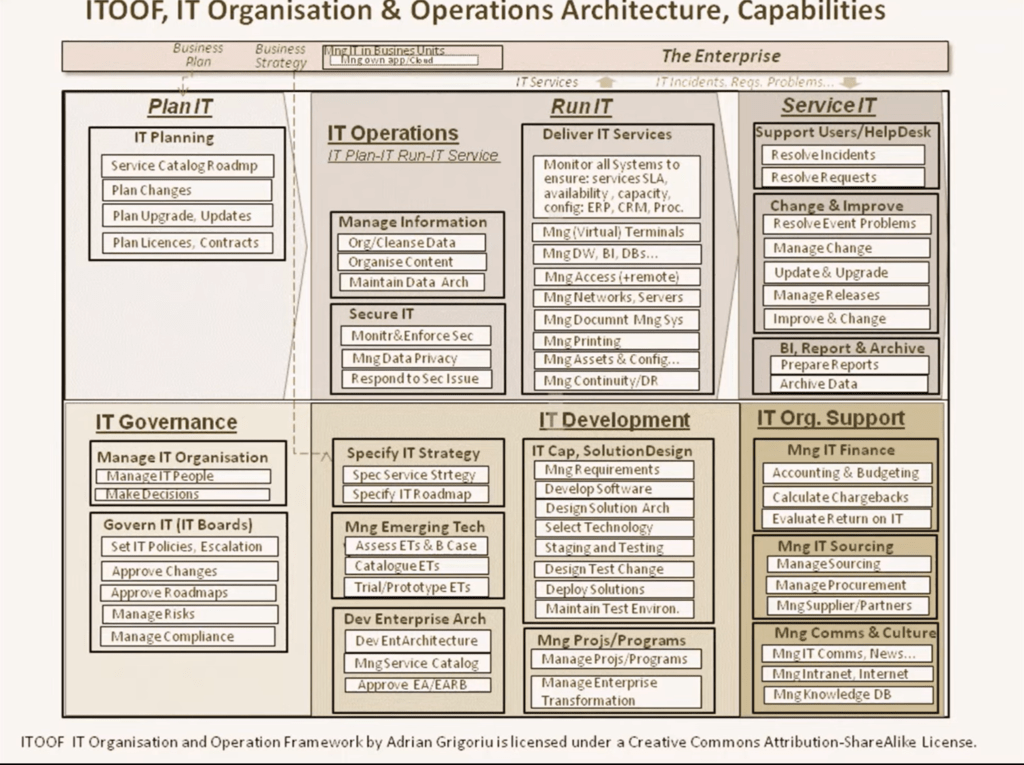
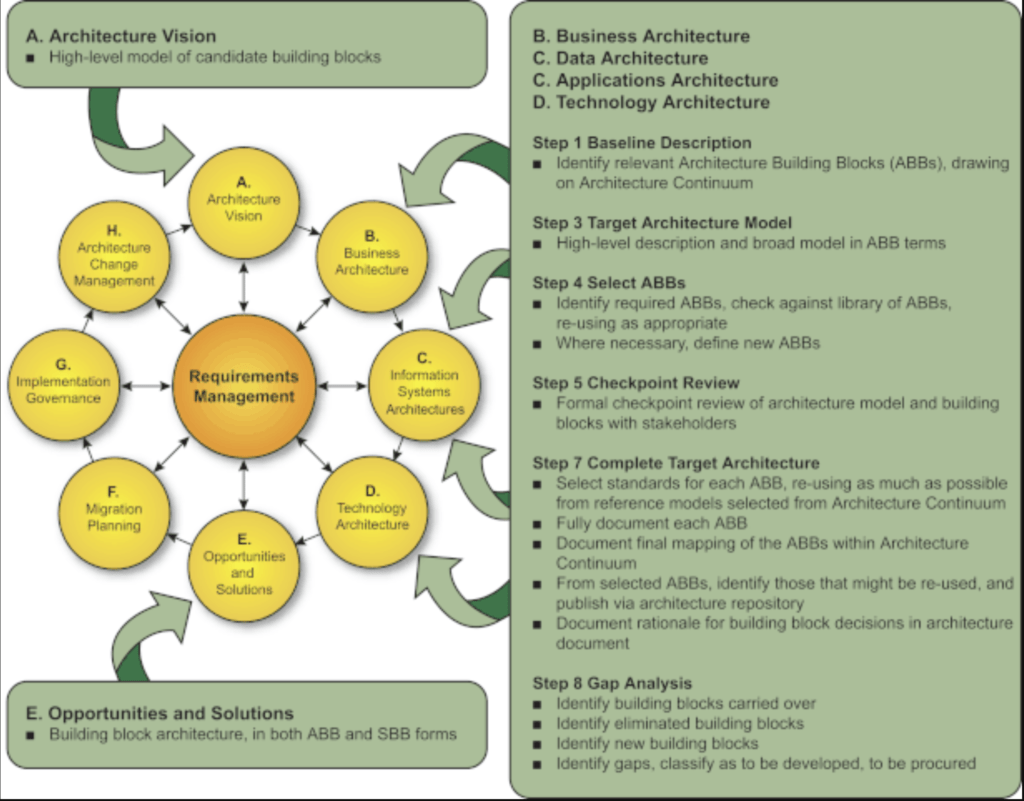
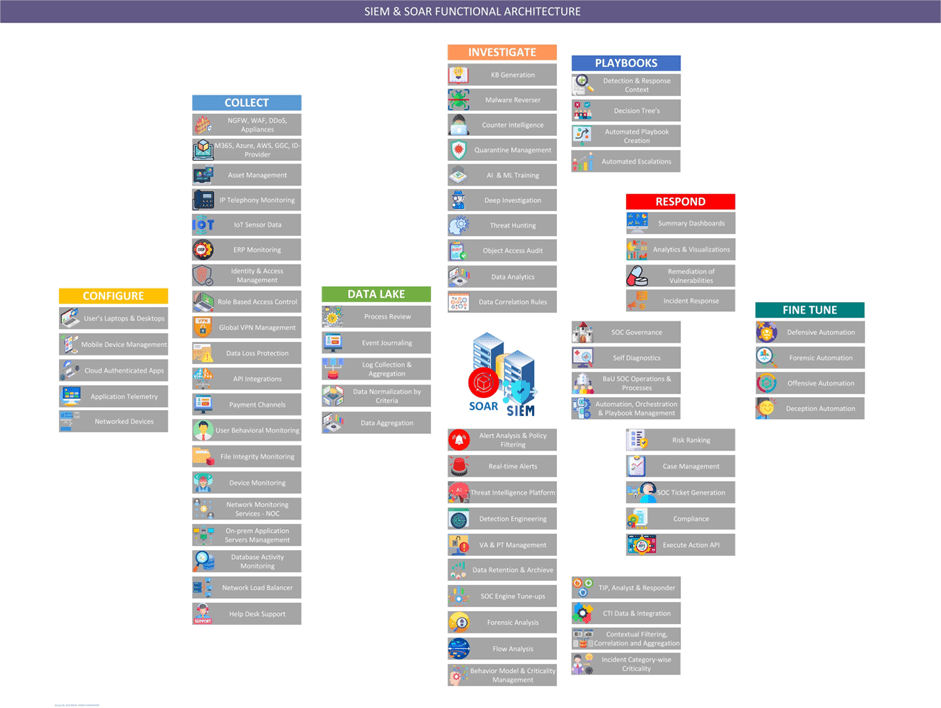
Reading Time: 3 minutesApplication Portfolio Management (APM) is a strategic discipline for managing an enterprise’s software applications as a portfolio of assets. The Gartner TIME Model is the industry-standard framework for this process, enabling organizations to make data-driven decisions to optimize costs, reduce risk, and align IT investments with business objectives.