
Reading Time: 3 minutesThis document provides a condensed overview of the comprehensive blueprint for establishing an Information Security Management Framework (ISMF) within a modern enterprise.
Meeting of Brilliant Syche – IT Pro's Corner

Reading Time: 3 minutesStatus: Final Blueprint (Condensed) Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: January 6, 2022 Location: Dhaka, Bangladesh Version: 1.0 (Summary) Executive Summary In a landscape of relentless cyber threats, traditional, point-in-time security assessments are Read More …
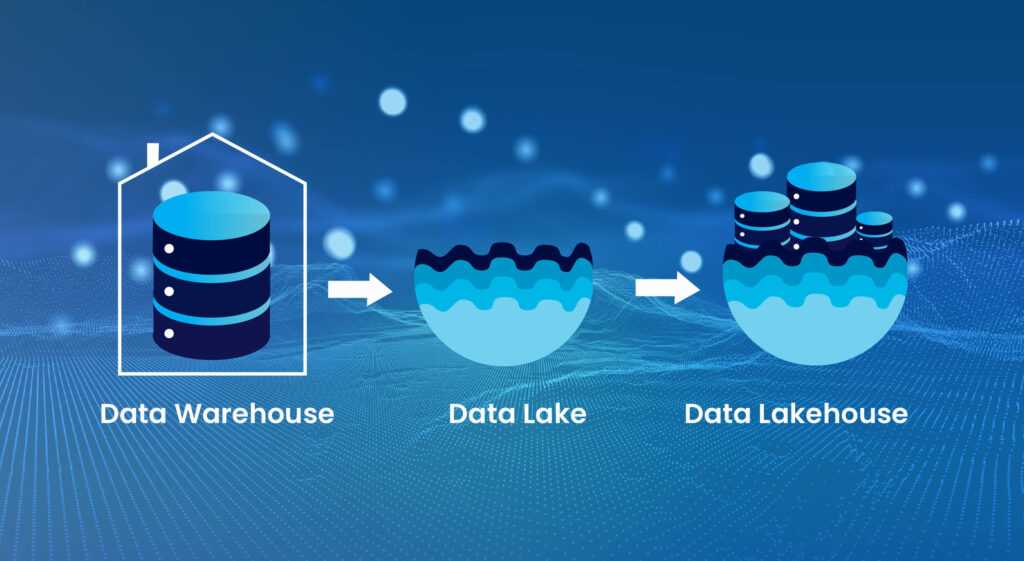
Reading Time: 4 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: October 26, 2023 Location: Dhaka, Bangladesh Version: 1.0 Executive Summary The Data Lakehouse paradigm marks a critical evolution in enterprise data architecture, merging the Read More …
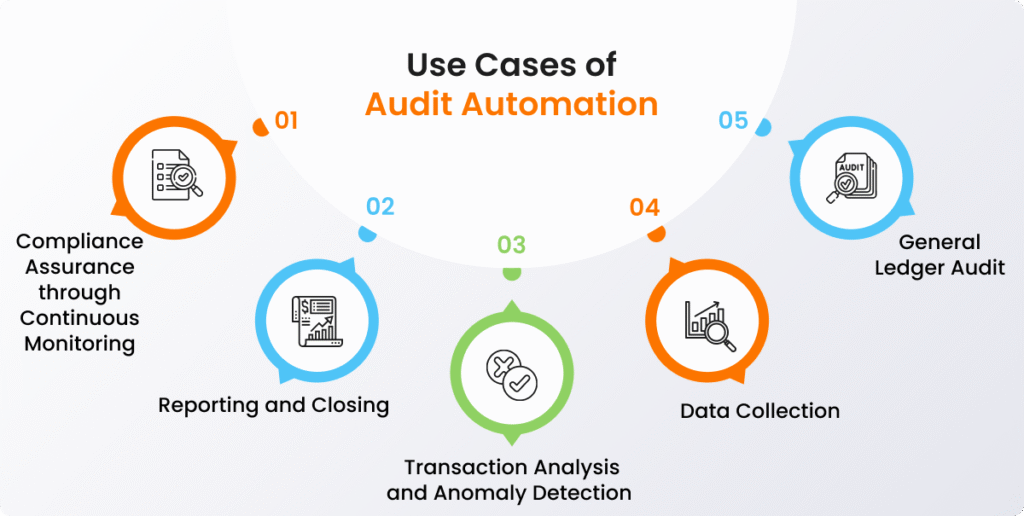
Reading Time: 5 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: December 9, 2024 Location: Dhaka, Bangladesh Version: 1.0 I. Executive Summary The internal audit function is undergoing a significant transformation, driven by complex business Read More …

Reading Time: 3 minutesStatus: Final Blueprint (Summary) Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: February 2, 2025 Location: Dhaka, Bangladesh Version: 1.0 (Summary) 1. Executive Summary Application Programming Interfaces (APIs) are the central nervous system of the Read More …
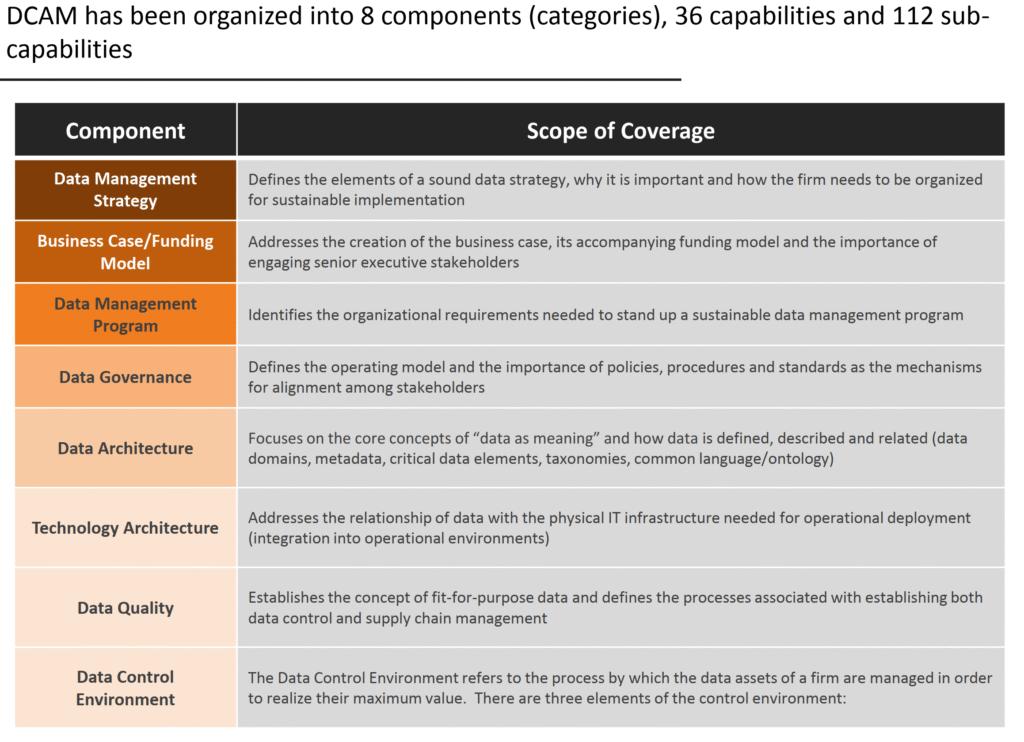
Reading Time: 3 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultancy Group Version: 1.0 Date: July 26, 2024 1. The Strategic Imperative In the modern digital economy, data is a primary strategic asset. The ability to manage, govern, Read More …

Reading Time: 4 minutesStatus: Final Blueprint (Summary) Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: October 4, 2024 Location: Dhaka, Bangladesh Version: 1.0 (Summary) 1. Executive Summary: The Strategic Imperative for Software-Defined Resilience The function of data protection Read More …
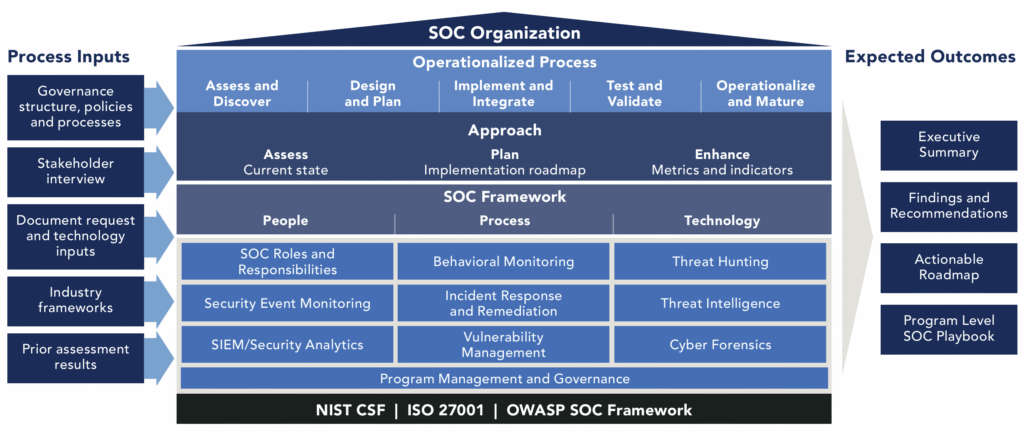
Reading Time: 3 minutesStatus: Final Blueprint Summary Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: April 4, 2024 The SOC as a Strategic Business Enabler The modern Security Operations Center (SOC) has evolved from a technical cost center Read More …
Reading Time: 3 minutesStatus: Final Blueprint (Summary) Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: July 24, 2025 Location: Dhaka, Bangladesh Version: 1.0 1. Executive Summary: The Agentic Enterprise is Here The enterprise is at a pivotal moment, Read More …
Reading Time: 3 minutesStatus: Final Blueprint (Summary) Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: February 6, 2024 Location: Dhaka, Bangladesh Version: 1.0 1. Executive Summary Phishing has evolved from a nuisance into a primary and financially devastating Read More …

Reading Time: 3 minutesStatus: Summary Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: July 24, 2025 Location: Dhaka, Bangladesh Version: 1.0 1. Executive Summary The modern enterprise faces a critical paradox: the need to defend against costly Read More …

Reading Time: 3 minutesStatus: Final Blueprint (Summary) Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: July 23, 2025 Location: Dhaka, Bangladesh Version: 1.0 1. The Proactive Imperative In the modern threat landscape, organizations must operate under the assumption Read More …

Reading Time: 4 minutesStatus: Final Blueprint (Summary) Author: Shahab Al Yamin Chawdhury Version: 1.0 1. Executive Summary: The Illusion of a Single Defense In the modern digital landscape, relying solely on a Distributed Denial-of-Service (DDoS) appliance creates a dangerous false sense of security. Read More …

Reading Time: 4 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: September 10, 2023 Version: 1.0 Executive Summary The modern software development environment has evolved into a distributed, cloud-native, and AI-augmented ecosystem, fundamentally changing the Read More …
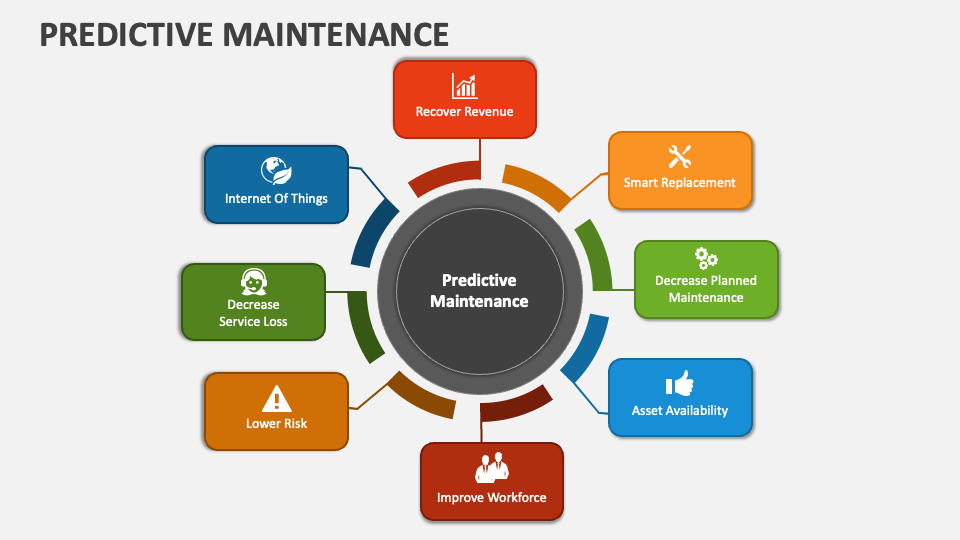
Reading Time: 3 minutesStatus: Summary of Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: October 9, 2024 Version: 1.0 1. The Challenge: The Predictive Maintenance Paradox For years, traditional predictive maintenance (PdM) based on machine learning Read More …
Reading Time: 4 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: May 4, 2024 Location: Dhaka, Bangladesh Version: 1.0 1. Executive Summary Modern enterprises face a paradox: a landscape of abundant cybersecurity frameworks has led Read More …

Reading Time: 3 minutes1.0 Purpose and Mandate This Security Program Aggregate (SPA) document establishes the formal, high-level governance framework for the organization’s security operations. It serves as the central charter, summarizing the policies and principles that are implemented through the comprehensive suite of Read More …

Reading Time: 5 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: August 28, 2024 Location: Dhaka, Bangladesh Version: 1.0 Executive Summary This blueprint provides a strategic framework for developing Security Operations Center (SOC) playbooks to Read More …
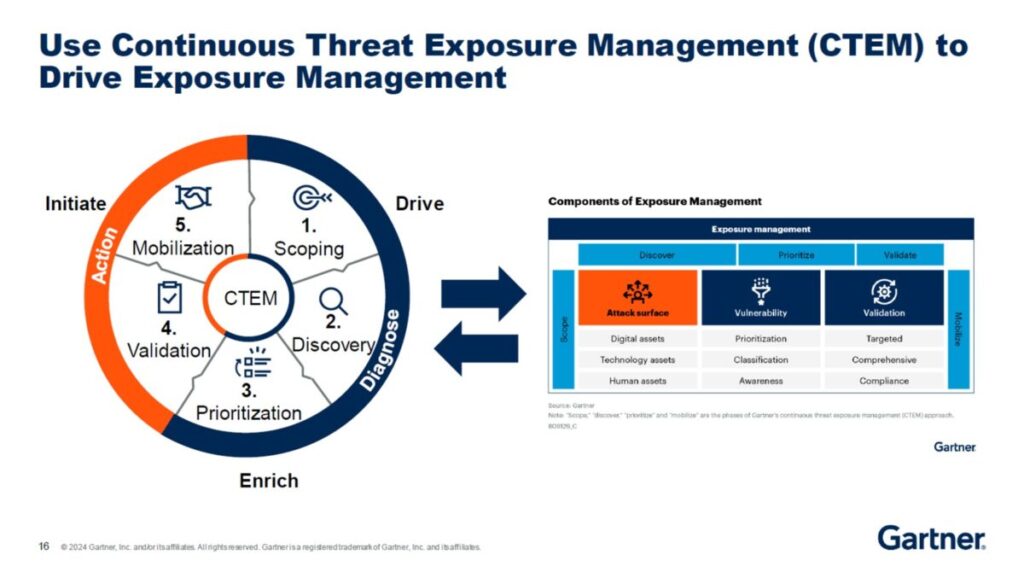
Reading Time: 4 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: July 23, 2025 Location: Dhaka, Bangladesh Version: 1.0 Executive Summary Continuous Threat Exposure Management (CTEM) marks a strategic evolution from reactive, incident-driven security to Read More …

Reading Time: 4 minutesStatus: Condensed Summary Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: February 9, 2024 Location: Dhaka, Bangladesh Version: 1.0 (Summary) Executive Summary The Information Systems (IS) auditing profession faces a seismic transformation driven by relentless Read More …
Reading Time: 3 minutesStatus: Final Blueprint (Summary) Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: September 11, 2023 Location: Dhaka, Bangladesh Version: 1.0 (Summary) Page 1: Strategic Overview & Core Differences 1. The Core Dichotomy: Automated Hygiene vs. Read More …

Reading Time: 5 minutesExecutive Summary The role of the Chief Information Security Officer (CISO) is at a critical inflection point. The immense pressure of the position has created a “Crisis of Command,” where ego-driven leadership fosters a toxic cycle of team burnout, high Read More …

Reading Time: 3 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: October 9, 2024 Location: Dhaka, Bangladesh Version: 1.0 1. Executive Summary This document addresses the strategic question of whether Internet Service Providers (ISPs) should Read More …

Reading Time: 4 minutesExecutive Summary The central thesis that IT/IS personnel lack the personal drive to upskill is a fundamental misdiagnosis. The core issue is not a failure of individual will but a failure of organizational design. While IT professionals are highly motivated Read More …

Reading Time: 5 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: September 23, 2023 Location: Dhaka, Bangladesh Version: 1.0 1.0 Executive Summary: Beyond Consolidation Unified virtual machine (VM) management has evolved from simple hypervisor consolidation Read More …

Reading Time: 5 minutesThe Enterprise Control Imperative In the modern enterprise, Information Technology General Controls (ITGCs) and IT Application Controls (ITACs) are the bedrock of financial reporting integrity and operational stability. Their effective implementation and auditing are critical for regulatory compliance, particularly with Read More …

Reading Time: 4 minutesStatus: Final Blueprint (Summary) Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: July 22, 2024 Version: 1.0 The Strategic Imperative & Modern Architectural Blueprints The Strategic Imperative: Business-Driven Design The modern enterprise network is not Read More …

Reading Time: 5 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: April 22, 2023 Location: Dhaka, Bangladesh Version: 1.0 Executive Summary: An Enterprise-Level Risk Ransomware has evolved from a niche cybersecurity issue into a fundamental Read More …

Reading Time: 4 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: July 21, 2024 Location: Dhaka, Bangladesh Version: 1.0 1.0 Executive Summary 2.0 The Evolving Threat Landscape 3.0 Amplified Risk Factors in Hybrid Environments 4.0 Read More …
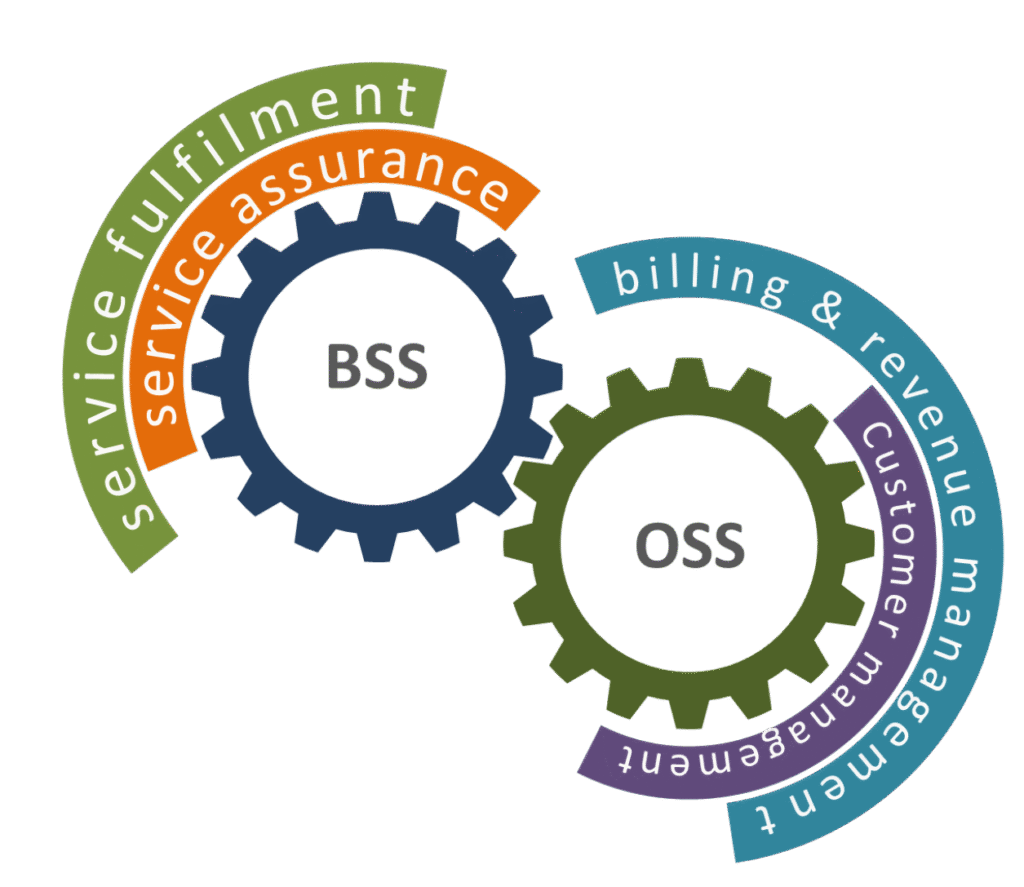
Reading Time: 4 minutes1. Executive Summary This document outlines a comprehensive blueprint for Operations Support Systems (OSS) and Business Support Systems (BSS) requirements within modern enterprise applications. Traditionally the domain of telecommunications, the principles of OSS and BSS are now critical for any Read More …

Reading Time: 4 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: July 21, 2025 Location: Dhaka, Bangladesh Version: 1.0 1. Executive Summary 2. Deep Dive: Laravel-Specific Concerns for Enterprise Use 3. Deep Dive: MySQL-Specific Concerns Read More …

Reading Time: 6 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: July 22, 2024 Location: Dhaka, Bangladesh Version: 1.0 Executive Summary The enterprise Business Intelligence (BI) landscape is undergoing a seismic shift, driven by the Read More …

Reading Time: 8 minutesExecutive Summary The advent of publicly available generative Artificial Intelligence (AI) represents a paradigm shift in the cybersecurity landscape. While offering immense productivity benefits, these tools have also been weaponized, providing adversaries with the means to automate, scale, and enhance Read More …

Reading Time: 4 minutes1. Executive Summary This document presents a strategic blueprint for leveraging the Cyber Attack Kill Chain model as a proactive framework for cybersecurity. The primary objective is to shift organizational defense from a reactive posture to a predictive and preventative Read More …

Reading Time: 5 minutes1.0 Executive Summary This document provides a comprehensive architectural blueprint for the strategic implementation of honeypots within an enterprise network. Honeypots serve as a proactive defense mechanism, acting as decoy systems designed to attract, deceive, and analyze the activities of Read More …

Reading Time: 6 minutes1.0 Executive Summary & 2025-2026 Focus Areas This document provides a comprehensive, multi-domain blueprint of the modern cybersecurity landscape, designed for Chief Information Security Officers (CISOs) and security leadership. It maps critical functions, responsibilities, technologies, and metrics across all major Read More …

Reading Time: 5 minutes1. Executive Summary This document provides a deep-dive analysis into the global Managed Detection and Response (MDR) market. It outlines current and emerging trends, analyzes adoption drivers and challenges, and offers a strategic blueprint for service providers and enterprises. The Read More …

Reading Time: 7 minutesThis document outlines the architectural blueprint for an AI-driven system designed to proactively predict burnout and resignation risk among technical employees. The attrition of skilled technical talent represents a significant and escalating cost to our organization, encompassing recruitment expenses, productivity Read More …
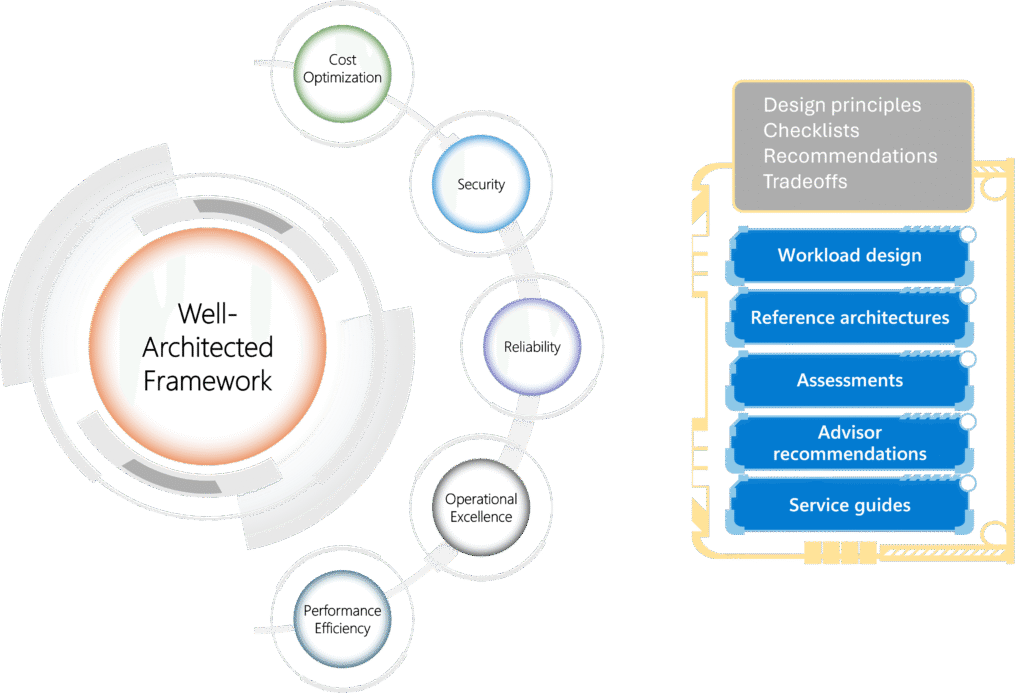
Reading Time: 5 minutes1. Introduction The Azure Reliability Maturity Model is a framework designed to help organizations assess and improve the reliability of their workloads running on Azure. It provides a structured path for continuous improvement, moving from reactive problem-solving to proactive, automated, Read More …

Reading Time: 4 minutesOverview To conduct a deep-dive investigation into the principles, practices, and challenges of identifying, tracking, and analyzing malicious actor activities within a corporate network. This document will culminate in a comprehensive, interactive report designed for C-suite executives, IT security leadership, Read More …

Reading Time: 2 minutesIT risk taxonomy is a structured framework that categorizes and classifies various types of IT-related risks, enabling organizations to manage and mitigate these risks effectively. Image Source: https://www.pwc.com/us/en/services/consulting/cybersecurity-risk-regulatory/library/technology-risk.html What is IT Risk Taxonomy? IT risk taxonomy is a systematic approach Read More …
Reading Time: < 1 minuteIn 2025, popular and effective visual HTML page generators include website builders like Wix, Webflow, and Squarespace, as well as tools like Froala, TinyMCE, and Codia AI for more specialized needs. These tools offer a range of features, from drag-and-drop Read More …

Reading Time: 4 minutesTable of Contents 1. Executive Summary Enterprises embracing two or more public clouds face unique security challenges: inconsistent controls, blind spots, and operational complexity. This report outlines a holistic architecture—spanning network fabric, resilient application platforms, identity-centric access, client-specific handling, and Read More …
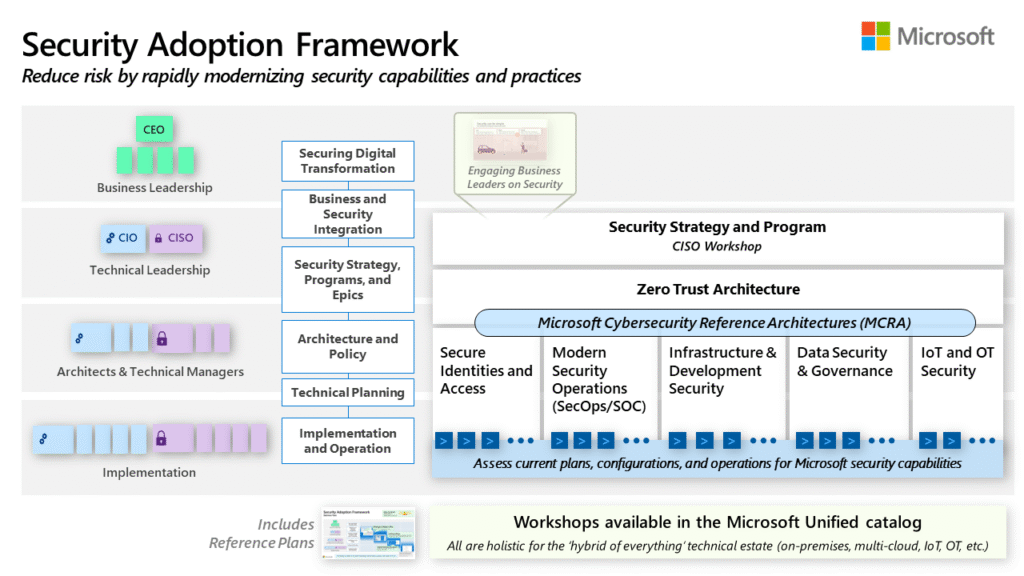
Reading Time: 2 minutesImage source: Security Adoption Resources | Microsoft Learn Traditional security models that rely on a fortified perimeter are no longer enough. With the rise of remote work, cloud applications, and increasingly sophisticated cyber threats, organizations need a more dynamic and Read More …
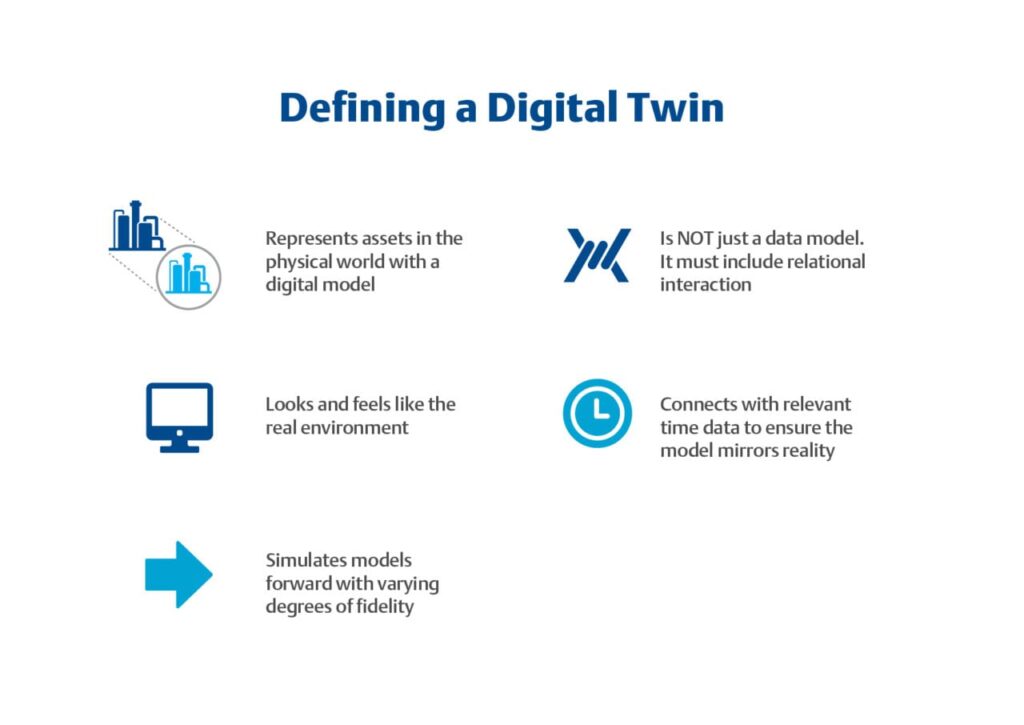
Reading Time: 2 minutesA digital twin is a virtual representation of a real-world object, system, or process, designed to accurately reflect its physical counterpart. It uses real-time data from sensors and other sources to create a dynamic, constantly updating model that mirrors the physical entity. This Read More …
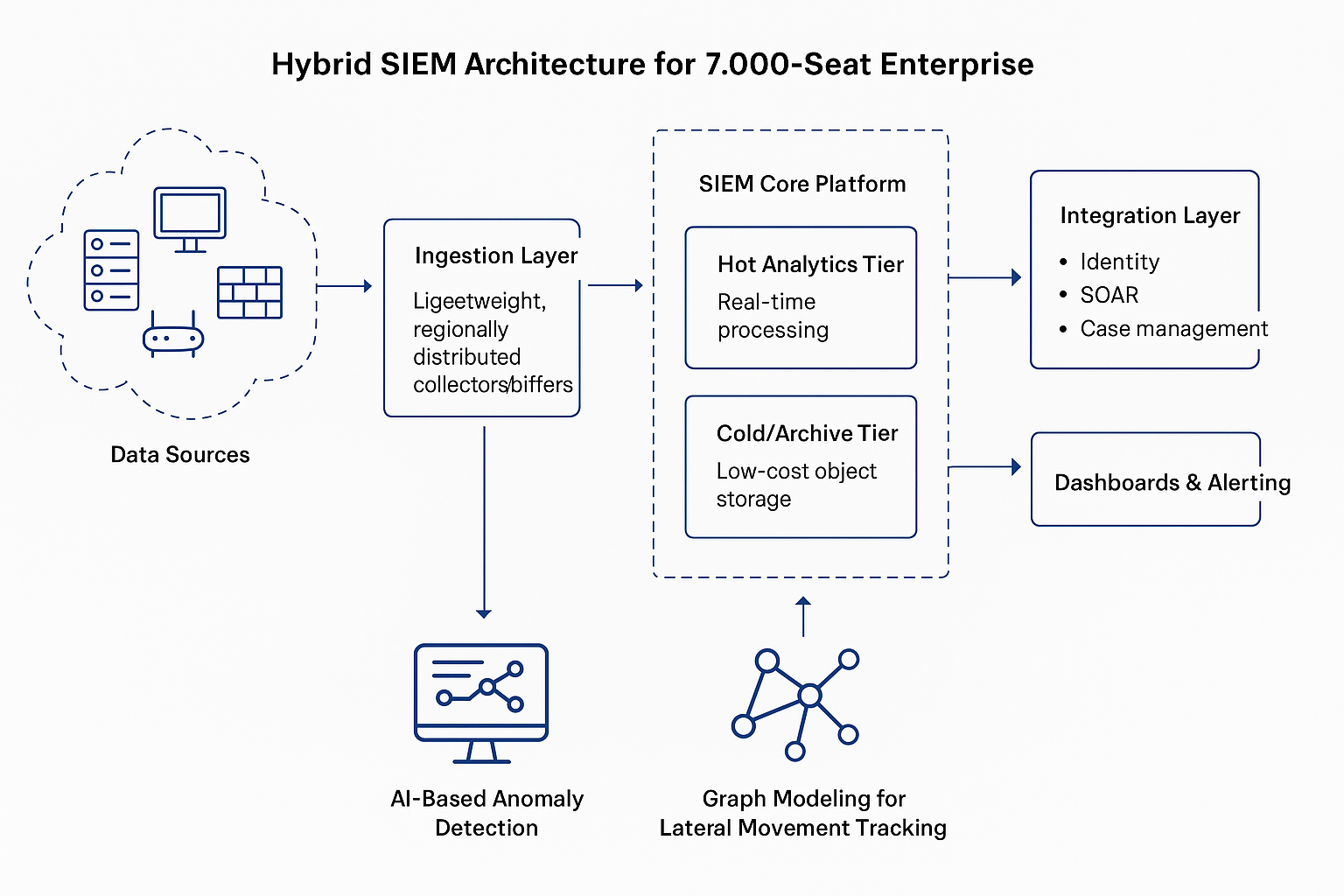
Reading Time: 8 minutesSIEM sizing is all about estimating the resources your Security Information and Event Management (SIEM) system that needs to handle log data efficiently—without overprovisioning or underestimating. The two key metrics used are: To calculate SIEM sizing, you typically keep the Read More …

Reading Time: 3 minutesMachine Identity Security (MIS) or Machine Identity Management (MIM) is another critical aspect of cybersecurity that focuses on securing and managing the digital identities of machines, such as servers, applications, and IoT devices, which is currently overlooked due to lack Read More …
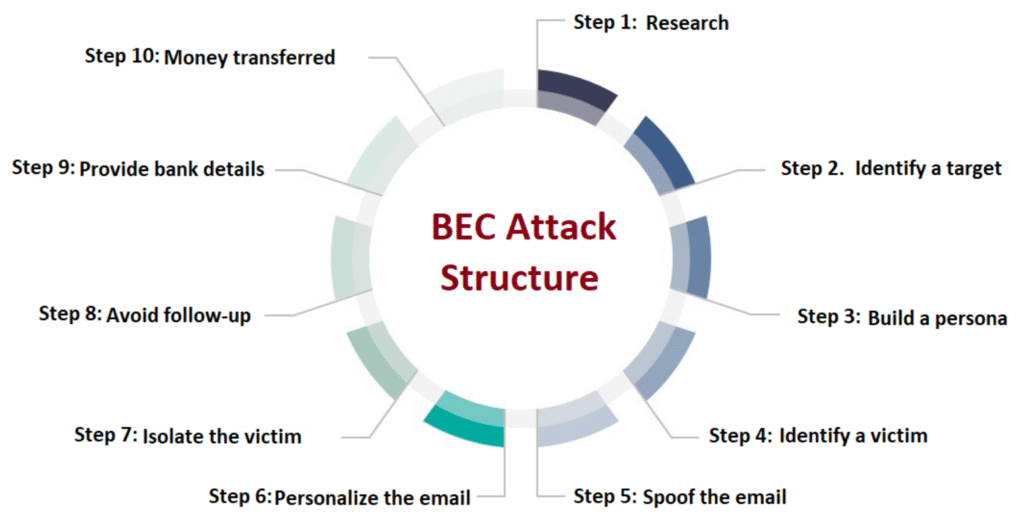
Reading Time: 3 minutesIn a typical Business Email Compromise (BEC) attack, attackers impersonate trusted individuals or organizations to deceive employees into taking harmful actions like transferring funds or sharing sensitive information. This involves research, email manipulation, and often social engineering tactics to exploit Read More …