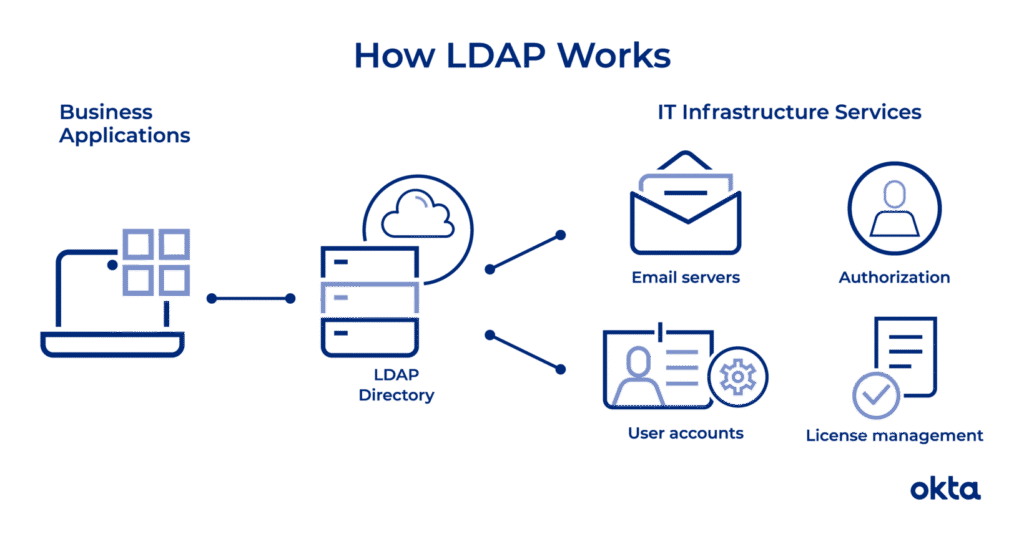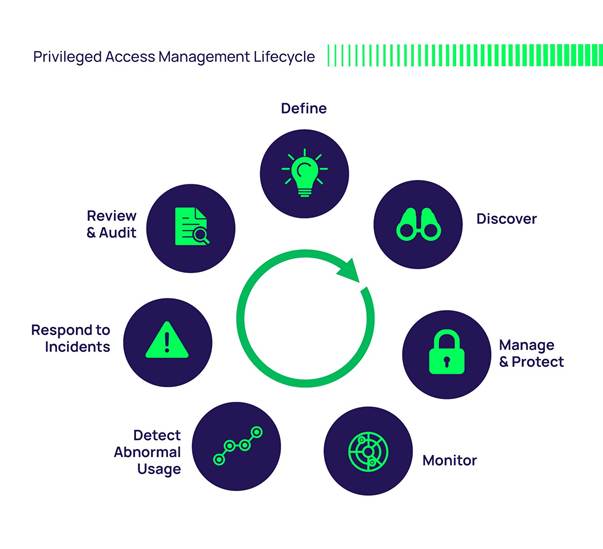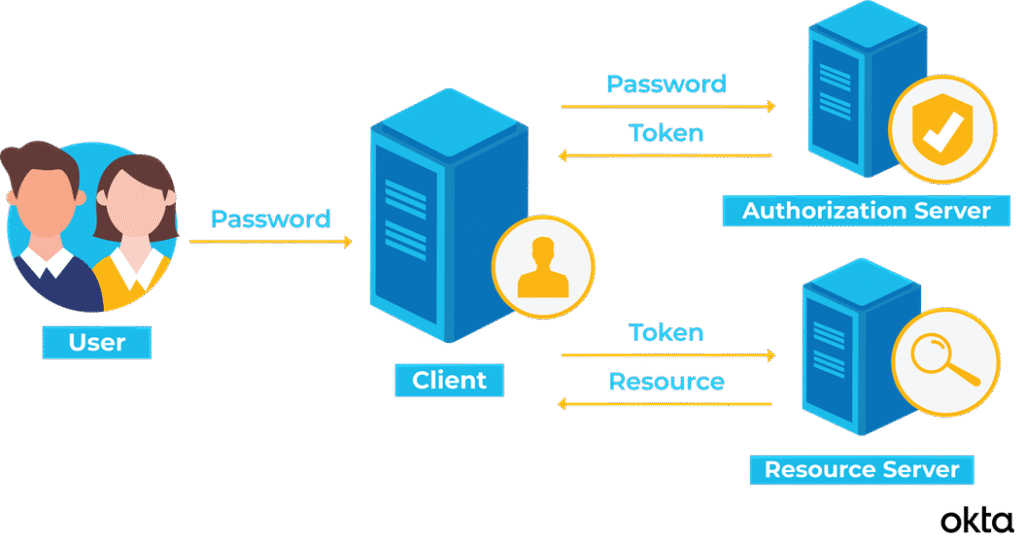
Reading Time: 4 minutesImage Source: TokenBasedAuthentication2.png (3121×1648) Developing an authentication server is a crucial part of building secure applications. Here’s a structured approach to creating one: 1. Define Your Authentication Method: Decide whether you’ll use: 2. Choose a Tech Stack: Pick a language Read More …