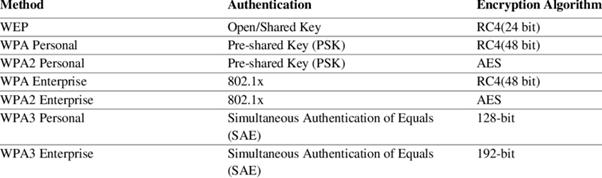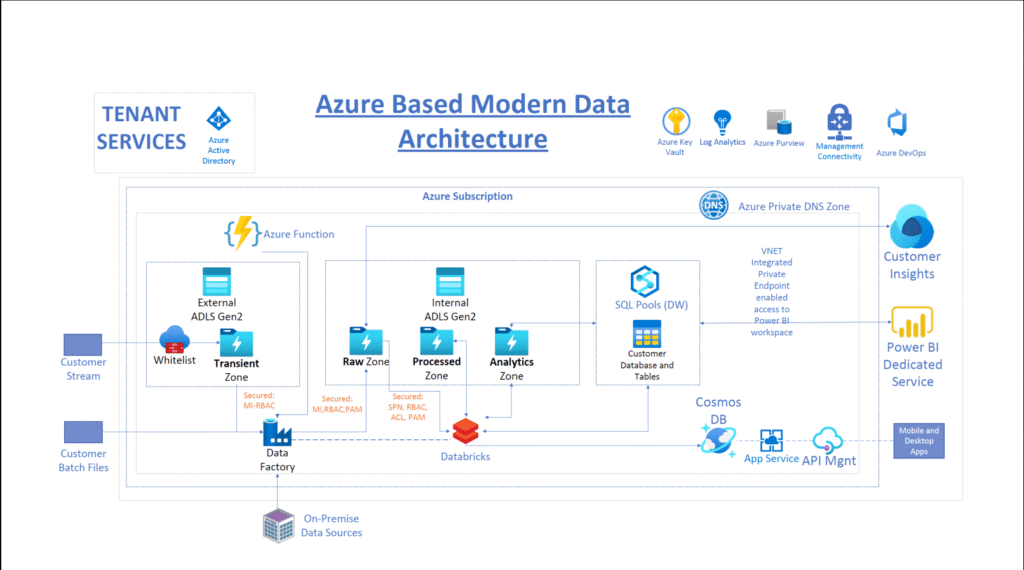
Reading Time: 6 minutesAzure Data Lake Architecture Overview Data Sources: Ingestion Layer: Storage Layer: Processing Layer: Analytics & Serving Layer: Governance & Security: Monitoring: +——————-+ +——————-+ +——————-+ | Data Sources | —> | Ingestion Layer | —> | Storage Layer | | (Structured, Read More …