 Reading Time: 7 minutes
Reading Time: 7 minutes

Status: Final Blueprint
Author: Shahab Al Yamin Chawdhury
Organization: Principal Architect & Consultant Group
Research Date: July 28, 2024
Location: Dhaka, Bangladesh
Version: 1.0
1. Executive Summary
The Sherwood Applied Business Security Architecture (SABSA) is a foundational, open-standard methodology for developing enterprise information security architectures. It’s business-driven and risk-focused, ensuring security isn’t just a technical add-on but a strategic enabler of business opportunities. SABSA provides a comprehensive roadmap from strategy to operations, fostering traceability and accountability. Its core pillars include a layered model (Contextual to Operational) and architectural perspectives (What, Why, How, Who, Where, When), all centered around the Business Attributes Profile (BAP) for requirements engineering. Successful SABSA implementation leads to reduced breaches, accelerated incident response, improved operational efficiency, and transforms security into a strategic enabler of growth and innovation.
2. Understanding the SABSA Framework
2.1. Core Principles
SABSA is fundamentally business-driven, with every security decision stemming from business requirements and a strong emphasis on risk management. It adopts a continuous lifecycle approach, integrating security from planning to retirement. This design shifts organizations from reactive compliance to a proactive, integrated, and continuously improving security posture, embedding security by design.
2.2. The SABSA Model: Layers and Perspectives
The SABSA Model is a multi-dimensional matrix combining six layers of abstraction with six perspectives:
- Layers: Contextual (Business), Conceptual (Architect’s), Logical (Designer’s), Physical (Builder’s), Component (Trade Specialist’s), and Operational (Manager’s). Each layer adds increasing detail.
- Perspectives: What (Assets), Why (Motivation), How (Process), Who (People), Where (Location), and When (Time). These ensure a holistic view.This matrix enforces top-down traceability, linking every security control to a specific business requirement, optimizing investments, and serving as a critical completeness check.
2.3. The SABSA Business Attributes Profile (BAP)
The BAP is central to SABSA, translating abstract business requirements into measurable security attributes (e.g., Accessible, Confidential, Scalable). It provides a shared taxonomy of stakeholder preferences, bridging the communication gap between business and technical teams. This ensures security investments are articulated in business terms, securing executive buy-in and fostering organizational alignment.
3. Strategic Alignment and Business Value Realization
3.1. Aligning Security with Business Strategy
SABSA meticulously aligns security with business objectives by deriving strategies from organizational goals. The SABSA Risk Model redefines risk management, focusing on removing uncertainty and optimizing for both opportunities and threats. This transforms risk from a barrier into a strategic enabler, leading to informed, risk-optimized decisions and efficient security spending.
3.2. Defining the Business Case: TCO, ROI, and Value Proposition
Quantifying security value is crucial. SABSA supports articulating this through:
- Total Cost of Ownership (TCO): Comprehensive cost including implementation, training, support, integration, and ongoing maintenance.
- Return on Investment (ROI): Quantifies profitability (Net Profit / TCO) x 100%, measuring efficiency gains, customer satisfaction, and cost savings.
- Value Proposition: A holistic view focusing on “Value Drivers” that impact P&L, competitive advantage, and operational resilience, transforming security into a strategic asset.
3.3. Strategic Roadmaps for Security Transformation
SABSA advocates for phased, iterative implementation roadmaps, rather than “big bang” transformations. These roadmaps guide the security evolution, incorporating advanced modules and ensuring continuous improvement. This approach allows for incremental value realization, adaptability to changing landscapes, and gradual building of internal competencies.
4. Governance, Risk, and Compliance (GRC) Integration
4.1. SABSA-Driven Cybersecurity Governance
Effective cybersecurity governance is paramount, establishing clear authority and responsibility for cybersecurity within the corporate structure. It’s an ongoing process requiring continuous monitoring and oversight to ensure components remain relevant and provide intended guidance. Governance acts as an enabler of trust and accountability, breaking down silos and fostering collaboration.
4.2. Roles, Responsibilities, and Accountability (RACI) Framework
The RACI framework (Responsible, Accountable, Consulted, Informed) clarifies roles across the security lifecycle. A well-defined RACI matrix, especially the SABSA-Extended RACI Model, is crucial for operationalizing governance, ensuring clear accountability, and preventing gaps or overlaps in security tasks.
4.3. Regulatory Compliance and Framework Integration
SABSA is highly compatible with frameworks like NIST Cybersecurity Framework (CSF) and ISO 27001. While each has distinct characteristics (e.g., jurisdiction, level of detail, cost), SABSA serves as an overarching framework that integrates them seamlessly. This harmonizes compliance with strategic architecture, making regulatory adherence a natural byproduct of a well-designed, business-aligned security program.
4.4. Security Policy Framework and Lifecycle Management
Security policies are foundational documents that translate objectives into rules. Within SABSA, policies are dynamic, living architectural artifacts requiring continuous lifecycle management. This involves proper communication, regular testing, and active enforcement, ensuring policies adapt to evolving threats and business needs, contributing to organizational security literacy.
5. The SABSA Architecture Development Lifecycle
5.1. Overview of the SABSA Development Process
The SABSA Development Process is a systematic methodology with continuous traceability from initial business requirements through all phases:
- Strategy and Planning: Defining security strategy aligned with business objectives and risk.
- Design: Developing detailed security architectures based on SABSA layers.
- Implement: Translating designs into deployable solutions.
- Manage and Measure: Ongoing operation, monitoring, maintenance, and incident response.
5.2. Detailed Activities and Functions per Lifecycle Phase
Each phase involves specific activities:
- Strategy and Planning: Business impact analysis, security goal alignment, risk context establishment (PESTELIM, SWOT), threat/opportunity identification.
- Design: Defining conceptual architecture, developing blueprints for asset protection.
- Implement: Defining physical and component architectures, selecting and deploying technologies.
- Manage and Measure: Defining operational architecture, continuous monitoring, reviews, and updates.This lifecycle is iterative, with feedback loops ensuring continuous refinement and adaptation.
5.3. Ensuring Traceability and Continuous Improvement
Traceability is a defining characteristic, linking every security measure to a business need or risk via the BAP. This ensures accountability, justifies investments, and optimizes spending. Continuous improvement is inherent, with ongoing assessment and enhancement guided by SABSA maturity models, ensuring the architecture remains effective and aligned with evolving contexts.
6. Deep Dive into SABSA Architecture Design Components
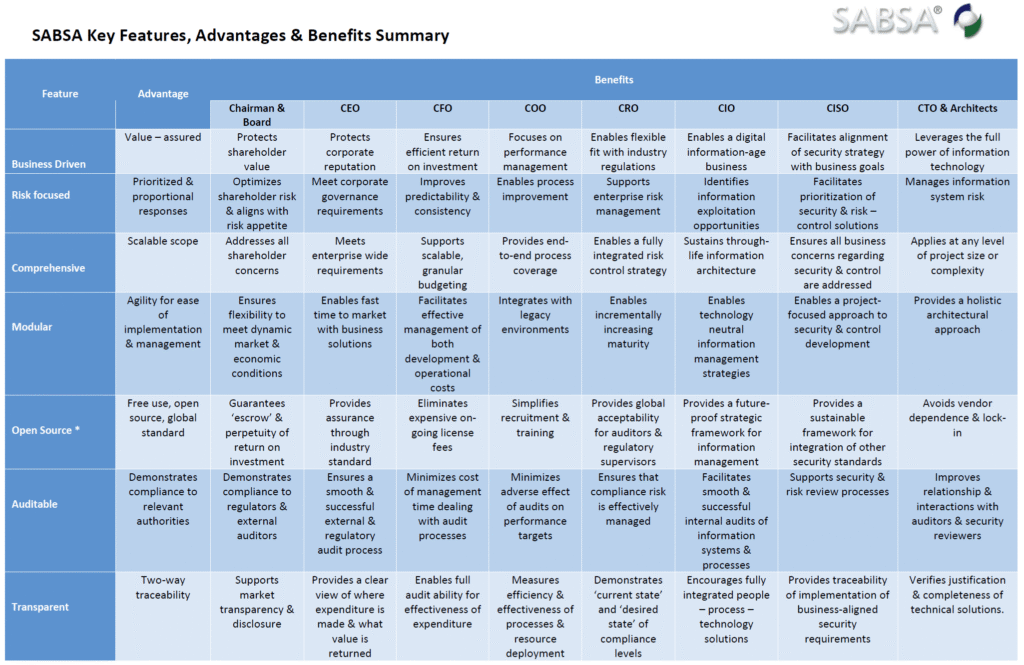
6.1. Conceptual Architecture: Control Objectives and Security Strategies
This “Architect’s Layer” defines high-level security concepts. It produces Control Objectives (desired security outcomes aligned with BAP) and Security Strategies (overarching approaches like defense-in-depth). This layer is critical for ensuring strategic intent guides all subsequent technical designs.
6.2. Logical Services Architecture: Security Policies and Services
The “Designer’s Layer” translates strategies into functional requirements. It defines Security Policies (rules without specific technologies) and Security Services (functional capabilities like authentication, authorization). This layer provides modular, reusable building blocks for secure capabilities, streamlining implementation.
6.3. Physical Infrastructure Architecture: Security Mechanisms and Controls
The “Builder’s Layer” transforms logical services into concrete technical solutions. It maps security to platform and network infrastructure, specifying Security Mechanisms (e.g., firewalls, encryption, IAM) and detailed rules. This layer ensures technical feasibility and operational efficiency, making the architectural design tangible.
6.4. Component Architecture: Technology and Product Selection
This “Trade Specialist’s Layer” focuses on granular technology and product selection. It specifies detailed data structures, security standards, and specific products (e.g., Zero-Trust stacks, XDR). Strategic sourcing and vendor alignment are crucial here to build an integrated security ecosystem, not just disparate point solutions, impacting TCO and operational efficiency.
6.5. Operational Architecture: Service Management and Support
The “Manager’s Layer” ensures continuous practice and sustained value. It focuses on operational continuity, risk management, and security service management and support. This layer defines roles, procedures, monitoring plans, and incident response, providing the essential feedback loop for continuous improvement and validating the efficacy of all other architectural layers.
7. Critical Data and Information Asset Management
7.1. Methodology for Identifying Critical Information Assets
Identifying critical information assets is fundamental. It involves business impact analysis and asset valuation, with Information Asset Owners classifying data (e.g., Confidential, Internal, Public) to determine protection levels. This business-driven approach prioritizes security resources for the “crown jewels.”
7.2. Data Classification and Handling Rules
Once identified, assets require systematic data classification and detailed handling rules. These rules specify where, how, and by whom information can be accessed, stored, or processed, extending to third-party engagements via contractual agreements.
7.3. Data Governance and Protection Strategies
Data governance is crucial for managing access and minimizing risks, defining responsibilities and policies. Protection strategies involve multi-layered defenses (encryption, access control, incident response). SABSA’s layered approach ensures integrated data lifecycle security, from creation to disposal, maintaining confidentiality, integrity, and availability.
8. Performance Measurement and Maturity Models
8.1. Key Performance Indicators (KPIs) and Key Risk Indicators (KRIs)
KPIs (e.g., Risk Burndown, Production Incidents) and KRIs (e.g., Risk Arrival, Risk Inter-arrival) are vital for monitoring security efficacy and demonstrating value. They translate technical data into business-focused metrics, enabling data-driven strategic decisions and securing continuous funding.
8.2. SABSA Maturity Model Assessment
Maturity models (e.g., Initial to Optimized) assess an organization’s security capabilities. They provide a structured framework for identifying weaknesses and developing pragmatic roadmaps for improvement. This frames SABSA implementation as a phased journey, allowing for incremental progress and continuous value delivery.
8.3. Roadmaps for Security Maturity Improvement
Insights from maturity assessments drive improvement roadmaps, aligning with strategic goals and identifying focus areas for highest ROI. Annual assessments ensure these roadmaps remain relevant and effective, reinforcing SABSA’s commitment to continuous improvement.
9. Technology Landscape, Integration, and Observability
9.1. Current Security Product Landscape and Technology Stacks
Security architecture is a blueprint, not a product. It guides the strategic selection of security stacks (e.g., Zero-Trust, XDR, MDM, CSPM, Backup/DR), which are curated collections of integrated tools (firewalls, SIEM, IAM). This shifts focus from disparate point solutions to cohesive, integrated ecosystems, reducing complexity and improving operational efficiency.
9.2. Integration with Enterprise Architecture Tools
Effective SABSA implementation requires integration with Enterprise Architecture (EA) tools (e.g., ArchiMate with its Security Overlay). This allows for model-driven EA, enhancing agility, communication, and reusability of architectural components. EA tools operationalize the framework, making it more agile and cost-effective.
9.3. Monitoring, Observability, and Telemetry
Modern security relies on observability and telemetry data (MELT: Metrics, Events, Logs, Traces). This provides critical early indicators for proactive prevention and rapid response. A robust security observability architecture (Edge Collection, Telemetry Transport, Central Analysis) ensures continuous insights, transforming security into a proactive, data-driven capability.
10. Conclusion and Recommendations
The “Implementation Plan – SABSA” blueprint advocates for a business-driven, risk-focused approach to security architecture, integrating seamlessly with core business processes. Its strength lies in enforcing traceability from business requirements to technical controls, optimizing investments, and demonstrating tangible value. Integration with NIST CSF and ISO 27001 fosters harmonized compliance, while continuous improvement through maturity models and KPIs ensures adaptability. Leveraging modern EA tools and robust observability operationalizes designs and provides real-time insights.
Recommendations:
- Establish a Dedicated SABSA Program: Ensure executive sponsorship and a multi-disciplinary team.
- Conduct Comprehensive BAP Workshops: Critical for capturing precise business requirements and alignment.
- Adopt a Phased, Iterative Roadmap: Avoid “big bang” deployments; deliver incremental value.
- Integrate with Existing EA and GRC Tools: Streamline documentation, traceability, and analysis.
- Develop a Robust Performance Measurement Framework: Use business-centric KPIs/KRIs to demonstrate ROI.
- Foster Continuous Learning and Adaptation: Embed continuous improvement, regular assessments, and feedback loops.
- Define Clear Roles and Responsibilities with RACI: Minimize ambiguity and ensure efficient collaboration.
By following this blueprint, organizations can build a security architecture that defends against threats and actively enables business growth, innovation, and sustained competitive advantage.
Chat for Professional Consultancy Services
