 Reading Time: 7 minutes
Reading Time: 7 minutes

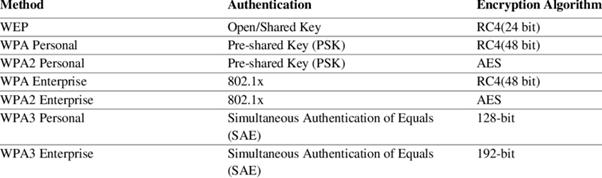
Wireless Pre-Shared Key (PSK)
A Pre-Shared Key (PSK) is a security mechanism used in Wi-Fi Protected Access (WPA) networks. It works by requiring both the wireless access point (AP) and the client device to have the same secret key before establishing a connection. This key is used to encrypt and decrypt data, ensuring secure communication. WPA-PSK is commonly used in home and small business networks because it doesn’t require a central authentication server.
Standards & Best Practices for Multi-Storied Wireless AP Design: designing a multi-story wireless network requires careful planning to ensure coverage, capacity, and minimal interference. Here are some best practices:
- Site Survey: Conduct a wireless site survey to identify signal strength, interference, and optimal AP placement.
- AP Placement: Install APs strategically to avoid dead zones. Place them centrally on each floor and stagger them vertically to minimize interference.
- Channel Optimization: Use 5GHz band where possible for better speed and less interference. Optimize channel selection to avoid congestion.
- Mesh Networking: Consider mesh Wi-Fi systems to improve coverage and seamless roaming.
- Transmit Power Adjustment: Avoid setting AP power to maximum, as it can cause interference and poor roaming performance.
Automatically Approving Legitimate Laptops Without Passwords: to allow trusted laptops to connect without requiring passwords, you can use:
- Windows Auto Login: Configure Windows auto-login using the netplwiz tool or registry settings.
- Certificate-Based Authentication: Deploy 802.1X authentication with EAP-TLS, where devices authenticate using digital certificates instead of passwords.
- MAC Address Whitelisting: Pre-register trusted MAC addresses in the network to allow automatic access.
- Single Sign-On (SSO): Use Active Directory (AD) integration to authenticate devices automatically.
- Biometric Authentication: Enable Windows Hello for password-free login using facial recognition or fingerprint scanning.
How does PSK compare to other security methods: Pre-Shared Key (PSK) is a simple and widely used authentication method, but it has some trade-offs compared to other security mechanisms. Here’s how it stacks up:
PSK vs. Enterprise-Level Security
- PSK (Personal/Home Use): Uses a single shared key for all users. It’s easy to set up but less secure because if the key is compromised, all devices are vulnerable.
- Enterprise Security (802.1X with RADIUS): Uses individual credentials for each user, often backed by a RADIUS server. This provides stronger security and better control over network access.
PSK vs. Public Key Infrastructure (PKI)
- PKI (Public Key Infrastructure): Uses public and private keys for authentication, offering higher security but requiring more complex setup and management.
- PSK: Relies on a shared secret key, making it easier to implement but more vulnerable to attacks if the key is leaked.
PSK vs. Other Encryption Methods
- Symmetric Encryption (PSK, AES): Uses the same key for encryption and decryption. Fast and efficient, but if the key is compromised, security is weakened.
- Asymmetric Encryption (PKI, RSA): Uses separate public and private keys, making it more secure but slower due to complex computations.
Best Use Cases
- PSK: Best for home networks, small businesses, and IoT devices where ease of setup is a priority.
- Enterprise Security & PKI: Ideal for large organizations, financial institutions, and government networks where security is critical.
What are the common vulnerabilities associated with PSK: while convenient, PSK has several vulnerabilities that can be exploited by attackers. Here are some of the most common risks:
1. Weak or Predictable Keys
- Many users set simple passwords that are easy to guess.
- Dictionary and brute-force attacks can crack weak PSKs, especially if they are short or commonly used.
2. Key Sharing & Exposure
- Since all devices use the same shared key, if one device is compromised, the entire network is at risk.
- Employees or guests may share the key, increasing the chances of unauthorized access.
3. Man-in-the-Middle (MITM) Attacks
- Attackers can intercept the four-way handshake process used in WPA-PSK authentication.
- If they capture the handshake, they can attempt to crack the key offline.
4. Lack of Individual User Authentication
- Unlike 802.1X authentication, PSK does not provide unique credentials for each user.
- This makes it difficult to track or revoke access for specific users.
5. Rogue Access Points
- Attackers can set up fake Wi-Fi networks with the same SSID and PSK.
- Unsuspecting users may connect to the rogue AP, exposing their data.
6. Limited Scalability
- In large networks, managing PSKs becomes challenging.
- Changing the key requires updating all devices manually, which can be disruptive.
How to Mitigate These Risks?
- Use strong, complex PSKs (long and random).
- Implement WPA2-Enterprise with 802.1X authentication for better security.
- Regularly rotate PSKs to minimize exposure.
- Enable MAC address filtering and network segmentation to limit access.
How does PSK compare to WPA2-Enterprise authentication: PSK (Pre-Shared Key) and WPA2-Enterprise are two different authentication methods used in Wi-Fi security, each with its own strengths and weaknesses. Here’s how they compare:
1. Authentication Method
- PSK (WPA2-Personal): Uses a single shared password for all devices. Simple to set up but less secure.
- WPA2-Enterprise: Uses 802.1X authentication with a RADIUS server, providing individual credentials for each user.
2. Security Level
- PSK: If the key is compromised, all devices are vulnerable.
- WPA2-Enterprise: Each user has unique credentials, making it much harder for attackers to gain access.
3. Scalability
- PSK: Best for small networks (homes, small offices).
- WPA2-Enterprise: Ideal for large organizations where centralized authentication is needed.
4. Ease of Use
- PSK: Simple to configure but requires manual key updates.
- WPA2-Enterprise: More complex to set up but offers better security and management.
5. Vulnerabilities
- PSK: Susceptible to brute-force attacks and key sharing.
- WPA2-Enterprise: Stronger security, but requires proper RADIUS server configuration.
How can an attacker exploit wireless networks, and how to stay secure: Wireless networks are convenient but can be vulnerable to various attacks. Here are some common threats and ways to stay secure:
Common Wireless Network Attacks
- Evil Twin Attack – An attacker sets up a fake Wi-Fi network with the same SSID as a legitimate one, tricking users into connecting and exposing their data.
- Man-in-the-Middle (MITM) Attack – Hackers intercept communication between a user and the network, allowing them to steal sensitive information.
- Packet Sniffing – Attackers capture unencrypted data packets traveling over the network, potentially revealing passwords and other private details.
- Denial-of-Service (DoS) Attack – Hackers flood the network with excessive traffic, causing disruptions and making it unusable.
- Brute Force Attacks – Attackers attempt to crack weak Wi-Fi passwords using automated tools.
How to Stay Secure
- Use Strong Encryption – Enable WPA2 or WPA3 encryption to protect data transmission.
- Change Default SSID & Passwords – Avoid using default router credentials, as they are easy to guess.
- Enable MAC Address Filtering – Restrict access to known devices only.
- Use a VPN – Encrypt your internet traffic to prevent interception.
- Regularly Update Firmware – Keep your router’s software up to date to patch security vulnerabilities.
- Disable WPS (Wi-Fi Protected Setup) – WPS can be exploited by attackers to gain access to your network.
Example of actual wireless network attack: here are some real-world examples of wireless network attacks:
1. Evil Twin Attack
- Attackers set up a fake Wi-Fi hotspot with the same SSID as a legitimate network.
- Unsuspecting users connect, allowing hackers to steal login credentials and sensitive data.
2. Man-in-the-Middle (MITM) Attack
- Hackers intercept communication between a user and a network.
- They can modify or steal data being transmitted, including passwords and financial information.
3. Packet Sniffing
- Attackers use tools like Wireshark to capture unencrypted data packets.
- This allows them to read sensitive information such as login credentials.
4. Denial-of-Service (DoS) Attack
- Hackers flood a wireless network with excessive traffic.
- This disrupts connectivity, making the network unusable.
5. Rogue Access Points
- Attackers install unauthorized access points within a network.
- This allows them to bypass security controls and gain access to sensitive data.
6. WEP/WPA Cracking
- Hackers exploit weaknesses in outdated encryption protocols.
- Using tools like Aircrack-ng, they can break weak Wi-Fi passwords.
How aircrackng can be used to compromise a wireless network: Aircrack-ng is a powerful suite of tools used for penetration testing and security auditing of wireless networks. While it is primarily designed for ethical hacking and security assessments, attackers can misuse it to compromise Wi-Fi networks. Here’s how:
How Aircrack-ng Can Be Used to Compromise a Wireless Network
- Monitor Mode Activation – Attackers enable monitor mode on their wireless adapter using airmon-ng, allowing them to capture network traffic.
- Packet Capture – Using airodump-ng, they collect packets from a target Wi-Fi network, including authentication handshakes.
- Deauthentication Attack – With aireplay-ng, attackers force a device to disconnect from the network, triggering a new handshake capture.
- Cracking WPA/WPA2 Encryption – Once the handshake is captured, aircrack-ng is used to brute-force the password using a wordlist.
- Fake Access Points – Attackers can set up rogue APs using airbase-ng to trick users into connecting to a malicious network.
How to Stay Secure
- Use Strong Passwords – Ensure your Wi-Fi password is long and complex.
- Enable WPA3 Encryption – If available, WPA3 offers stronger security than WPA2.
- Disable WPS (Wi-Fi Protected Setup) – WPS is vulnerable to brute-force attacks.
- Monitor Network Activity – Regularly check for unauthorized devices.
- Use MAC Address Filtering – Restrict access to known devices only.
Attack methods can be used in WEP: WEP (Wired Equivalent Privacy) is an outdated wireless security protocol that is highly vulnerable to attacks. Here are some common methods attackers use to exploit WEP:
1. Chop-Chop Attack
- Allows an attacker to decrypt packets without knowing the encryption key.
- Works by removing bytes from a captured packet and analyzing responses from the network.
2. Fragmentation Attack
- Exploits WEP’s weak encryption by breaking packets into smaller fragments.
- Attackers use these fragments to reconstruct the encryption key.
3. Dictionary Attack
- Attackers use a precomputed list of possible WEP keys to crack the encryption.
- If the key is weak or commonly used, it can be cracked within minutes.
4. FMS Attack (Fluhrer, Mantin, and Shamir)
- Exploits weak initialization vectors (IVs) in WEP encryption.
- Attackers collect a large number of packets and use statistical analysis to recover the key.
5. Fake Authentication Attack
- Attackers impersonate a legitimate client to gain access to the network.
- They send authentication requests to the access point, bypassing security checks.
6. ARP Cache Poisoning
- Attackers inject malicious ARP packets into the network.
- This allows them to redirect traffic and capture sensitive data.
Why is WEP So Vulnerable?
- Uses RC4 encryption, which is weak and predictable.
- Short IVs (24-bit) make key reuse common.
- No key management, meaning once a key is cracked, the entire network is compromised.
How to Stay Secure
- Upgrade to WPA2 or WPA3 for stronger encryption.
- Use long, complex passwords to prevent dictionary attacks.
- Monitor network activity for suspicious behavior.
The PTW attack (Pyshkin, Tews, Weinmann) is an advanced method used to crack WEP encryption in wireless networks. It improves upon earlier attacks like FMS (Fluhrer, Mantin, Shamir) by requiring fewer data packets to recover the WEP key.
How the PTW Attack Works
- Capturing Packets – Attackers use tools like Aircrack-ng to collect encrypted packets from a target Wi-Fi network.
- Exploiting Weak IVs – WEP uses short initialization vectors (IVs), which can be reused, making it easier to analyze patterns.
- Statistical Analysis – The PTW method applies mathematical techniques to extract the encryption key from captured packets.
- Key Recovery – Once enough packets are collected, the attacker can decrypt the WEP key, gaining unauthorized access to the network.
Why is WEP Vulnerable?
- Weak encryption (RC4) makes it easy to exploit.
- Short IVs (24-bit) lead to key reuse.
- No individual authentication, meaning once the key is cracked, all devices are compromised.
How to Stay Secure
- Upgrade to WPA2 or WPA3 for stronger encryption.
- Use long, complex passwords to prevent brute-force attacks.
- Monitor network activity for suspicious behavior.