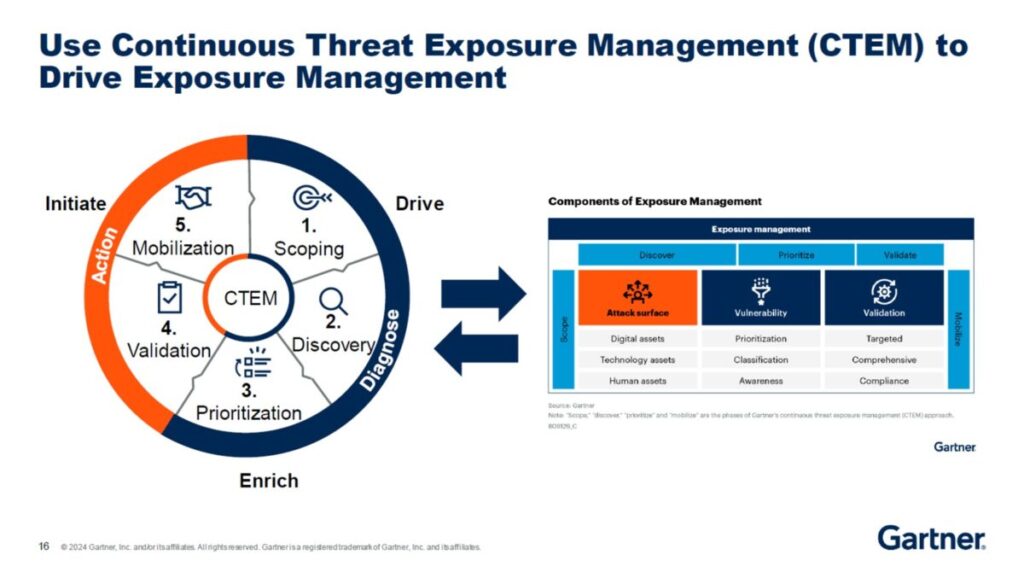
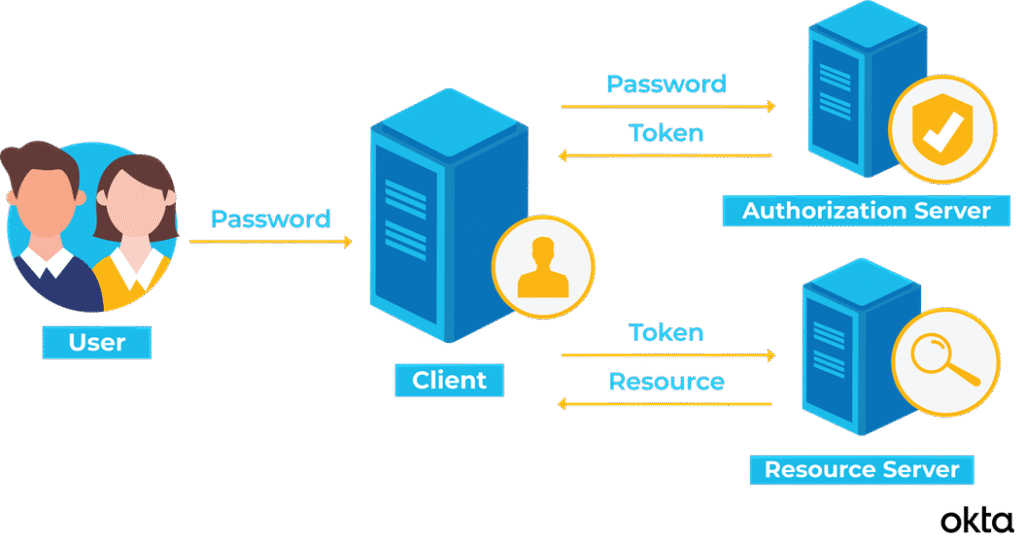
Reading Time: 6 minutesThis blueprint outlines the integration of Security Orchestration, Automation, and Response (SOAR) with proactive Threat Hunting. This synergy shifts organizations from reactive to proactive defense, enhancing cybersecurity posture, improving Security Operations Center (SOC) efficiency, and accelerating response times to advanced threats. Key recommendations include phased implementation, KPI-driven measurement, continuous improvement, and investment in human capital.