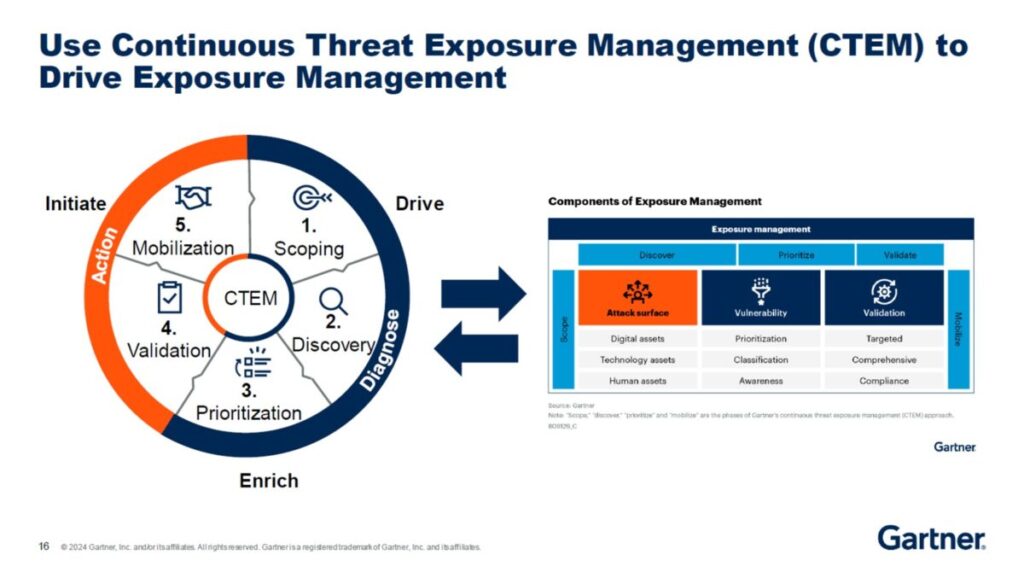
Reading Time: 3 minutes1.0 Purpose and Mandate This Security Program Aggregate (SPA) document establishes the formal, high-level governance framework for the organization’s security operations. It serves as the central charter, summarizing the policies and principles that are implemented through the comprehensive suite of Read More …