 Reading Time: 3 minutes
Reading Time: 3 minutes

Status: Final Blueprint Summary
Author: Shahab Al Yamin Chawdhury
Organization: Principal Architect & Consultant Group
Research Date: April 4, 2024
The SOC as a Strategic Business Enabler
The modern Security Operations Center (SOC) has evolved from a technical cost center into a strategic business asset. Its mission is no longer confined to defense but extends to enabling business resilience, building stakeholder trust, and providing the security confidence required for rapid innovation. An effective SOC must be explicitly aligned with business objectives and risk appetite, serving as the operational arm of the organization’s Governance, Risk, and Compliance (GRC) strategy.
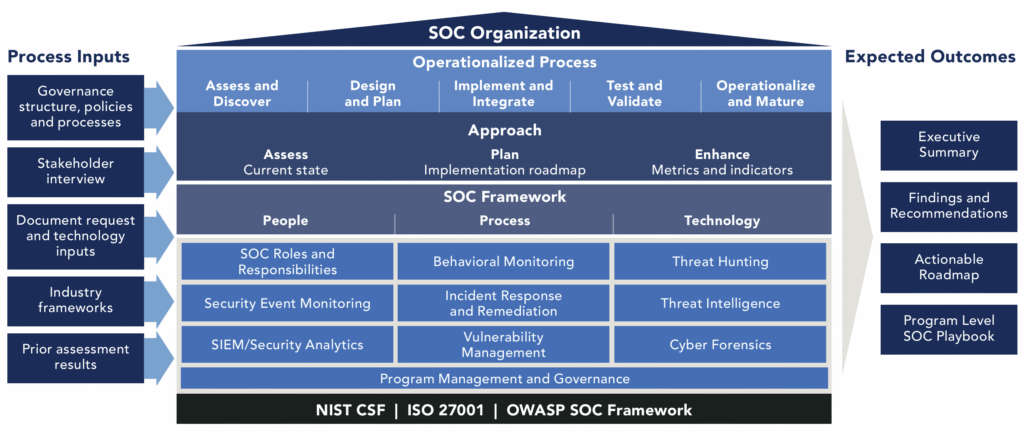
The Three Foundational Pillars of SOC Capability
The effectiveness of a SOC rests on the balanced maturity of three interdependent pillars. Weakness in one pillar undermines the others.
1. People & Organization
People are the most critical component. Technology and processes are merely force multipliers for human expertise.
- Modern Team Structures: Organizations are moving from traditional tiered models to more agile structures like cross-functional “Pods” and hybrid models that blend in-house talent with outsourced MSSP/MDR services.
- Core Roles: A mature SOC requires well-defined roles including Analysts (Tiers 1-3), Engineers, a Manager/Lead, Threat Intelligence Analysts, and specialists in Forensics and Compliance.
- Skills Matrix: A competency matrix is essential for assessing skills, identifying gaps, and planning training. Key skill areas include:
- Technical: SIEM, EDR/NDR, Cloud Security, Scripting (Python/PowerShell).
- Soft Skills: Critical Thinking, Complex Problem-Solving, Communication, and Adaptability.
2. Process & Governance
Well-defined, repeatable processes ensure consistency, reduce error, and enable automation.
- Incident Response (IR) Lifecycle (NIST SP 800-61): The cornerstone of SOC operations.
- Preparation: Establishing plans, teams, and tools before an incident.
- Detection & Analysis: Identifying, validating, and scoping incidents.
- Containment, Eradication & Recovery: Limiting damage and restoring operations.
- Post-Incident Activity: Learning lessons to improve future defenses.
- SOC Playbooks (SOPs): Detailed, step-by-step guides for handling specific incident types (e.g., Ransomware, Phishing), ensuring a swift and consistent response.
- Vulnerability Management: A continuous cycle of discovering, prioritizing, remediating, and verifying vulnerabilities to reduce the attack surface.
- Threat Intelligence Integration: Systematically using threat intelligence to move from a reactive to a proactive posture, informing detection, hunting, and response.
3. Technology & Architecture
Technology provides the visibility, analytics, and response capabilities necessary to operate at scale.
- The SOC Visibility Triad (Gartner): The architectural foundation for comprehensive threat visibility.
- SIEM: The central hub for log aggregation, correlation, and alerting.
- EDR: Deep visibility and response capabilities on endpoints (laptops, servers).
- NDR: Monitoring network traffic to detect lateral movement and internal threats.
- Key Platforms:
- SOAR: To automate and orchestrate repetitive workflows.
- Threat Intelligence Platforms (TIPs): To manage and operationalize threat data.
- Case Management: To track incidents and document investigations.
A Multi-Framework Approach to Excellence
A world-class SOC integrates multiple industry standards into a cohesive strategy.
- MITRE ATT&CK®: The tactical framework for understanding and modeling adversary behavior. Used for detection engineering, threat hunting, and adversary emulation.
- NIST Cybersecurity Framework (CSF): The strategic framework for managing and communicating cybersecurity risk to leadership, organized around Govern, Identify, Protect, Detect, Respond, and Recover.
- ISO 27001: The international standard for an Information Security Management System (ISMS), providing auditable controls for mature and repeatable SOC processes.
Measuring Success: Maturity and Performance
The SOC Capability Maturity Model (SOC-CMM)
The SOC-CMM provides a structured path for assessing and improving operational effectiveness across five domains: Business, People, Process, Technology, and Services. Maturity is measured on a scale from Level 0 (Non-Existent) to Level 5 (Optimizing). This allows a SOC to benchmark its current state, define a target state, and create a data-driven roadmap for improvement.
Performance Measurement (KPIs & KRIs)
A data-driven SOC demonstrates its value through metrics. Dashboards must be tailored for different audiences (Analysts, CISO, Board).
- Key Detection Metrics: Mean Time to Detect (MTTD), Detection Coverage (vs. ATT&CK).
- Key Response Metrics: Mean Time to Respond (MTTR), Incident Closure Rate.
- Key Business Metrics: Risk Reduction, Return on Security Investment (ROSI).
The Future-Ready SOC
The SOC must continuously evolve to meet future threats and business needs.
- Automation (SOAR): Essential for managing alert volume and freeing up analysts for high-value tasks.
- AI & Advanced Analytics: Leveraging AI/ML for behavioral analytics (UEBA), AI-powered triage, and predictive threat intelligence.
- Architectural Evolution: Adapting to secure cloud-native environments and the convergence of IT and Operational Technology (OT).
Top Strategic Recommendations
- Establish a Business-Aligned Charter: Define a formal SOC mission that is explicitly linked to enterprise goals and risk appetite.
- Implement Continuous Maturity Assessment: Use the SOC-CMM to benchmark capabilities, identify gaps, and create a tangible improvement roadmap.
- Prioritize Process Definition: Focus relentlessly on documenting and standardizing core processes, especially incident response playbooks, before making major technology investments.
- Adopt a Data-Driven Approach: Implement a comprehensive metrics program to measure performance and communicate the SOC’s value in terms of risk reduction and ROSI.