 Reading Time: 3 minutes
Reading Time: 3 minutes
Organizations face significant challenges in securing sensitive information while navigating an evolving threat landscape. Effective data security practices require a strategic approach to identify, assess, and mitigate risks. This concept paper explores key aspects of data security risks, solutions, and the prioritization of high-risk, high-impact scenarios for efficient mitigation. These concepts are also part of a Zero Trust model component, but we are not discussing the merits of Zero Trust right now, that will have to be stated in a different post.

Data Exposure Security Risks
Data exposure occurs when sensitive information is inadvertently or maliciously made accessible to unauthorized individuals. This risk stems from factors such as insecure storage practices, improper data handling, misconfigured systems, and human errors. Breaches can lead to financial loss, reputational damage, and regulatory penalties.
How to Mitigate Emergency Risks
In emergency situations, swift actions are critical to minimize damage. Organizations can mitigate risks through:
- Incident Response Plans: Predefined procedures for addressing security incidents effectively.
- Regular Training: Educating employees on emergency protocols and phishing detection.
- Automated Monitoring: Implementing real-time monitoring tools to detect anomalies and trigger alerts.
Risk Mitigations and Risk Realizations
Mitigation strategies include:
- Encryption: Securing data in transit and at rest.
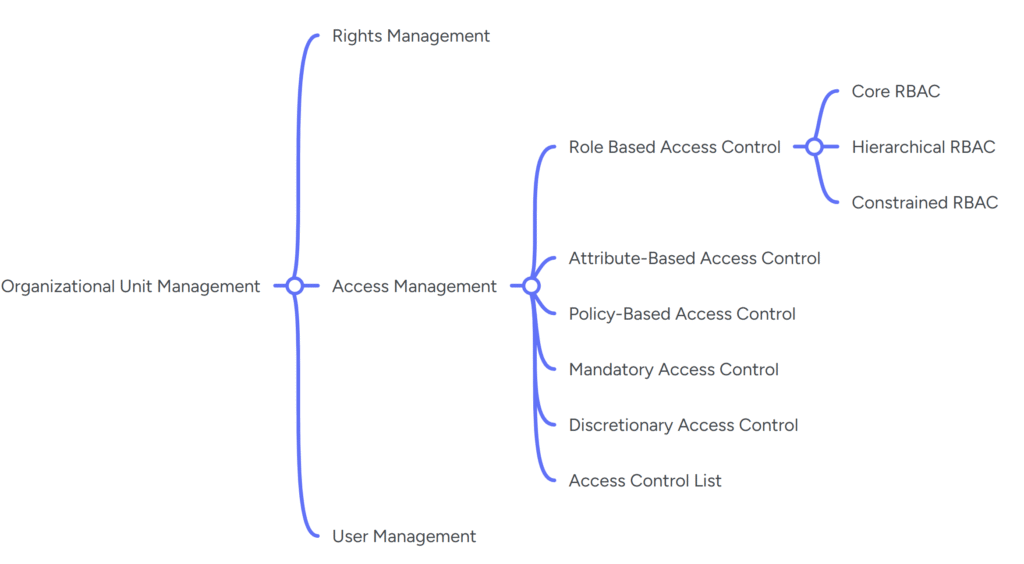
- Access Controls: Limiting data access based on roles and responsibilities. Also check the below image for access control types and available mechanisms through partner products.
- Backup Systems: Ensuring data recovery in the event of a breach or ransomware attack.
Risk realizations occur when mitigation measures fail, emphasizing the importance of proactive monitoring, robust contingency plans, and ongoing risk assessments.
Example: Best Practices for Secure Data Handling
Consider an organization that handles customer financial data. To safeguard this information:
- Risk Identification: Assess risks, such as external hacking attempts or insider threats.
- Mitigation: Employ multi-factor authentication, end-to-end encryption, and regular audits.
- Outcome: Reduced risk of unauthorized data access and enhanced customer trust.
Data Access Risks
Unauthorized or excessive access to sensitive data creates vulnerabilities. Risks arise from weak authentication, excessive privileges, or lack of oversight. To address these challenges:
- Use least privilege principles to restrict access.
- Conduct periodic access reviews and revoke unnecessary permissions.
- Implement user activity monitoring to detect unusual behaviors.
Mitigation and Solutions Based on Criteria
1. Fusing Insights to Unify Risk Indicators
Specialized analytics tools consolidate data from various sources, providing a unified view of risk indicators. This approach enables accurate risk scoring and better prioritization.
2. Prioritizing Events with High Impact
Focus on high-risk, high-impact events, such as database breaches or ransomware attacks, which pose significant business consequences. Prioritize preventive actions, such as patch management and threat intelligence integration.
3. Speeding Actions with Specific Recommendations
Leverage advanced AI-driven systems to provide actionable recommendations for addressing vulnerabilities. Speed up mitigation efforts by automating routine tasks, such as vulnerability scanning and patch deployment.
Conclusion
By unifying risk indicators, prioritizing critical events, and accelerating response times, organizations can strengthen their defenses and reduce the likelihood of costly breaches. Safeguarding data is not just a technical challenge; it is a strategic imperative for sustaining trust and success in a data-driven world.