Reading Time: 2 minutes
Reading Time: 2 minutes
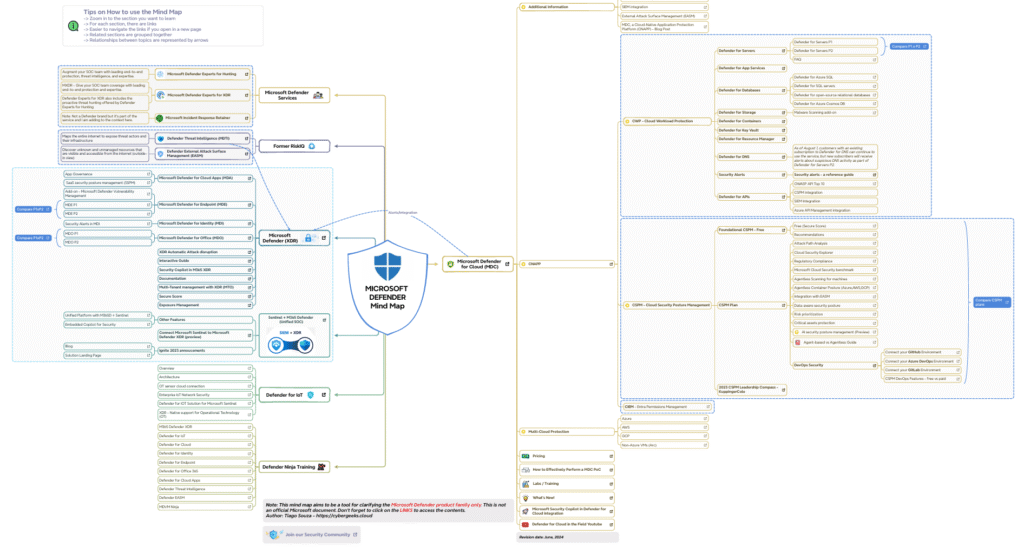
A mind map for Extended Detection and Response (XDR) can help visualize the components and concepts involved in XDR security solutions. This can be useful for understanding the scope, capabilities, and integration points of XDR, as well as for planning and implementing XDR solutions. Don’t forget that its also a strategic decision on how the features of an XDR will play out, here Microsoft Defender XDR, which also opens up a whole telemetry analysis for your SOC log ingestion which is naturally built in for Microsoft Sentinel.
Here’s a possible structure for an XDR mind map:
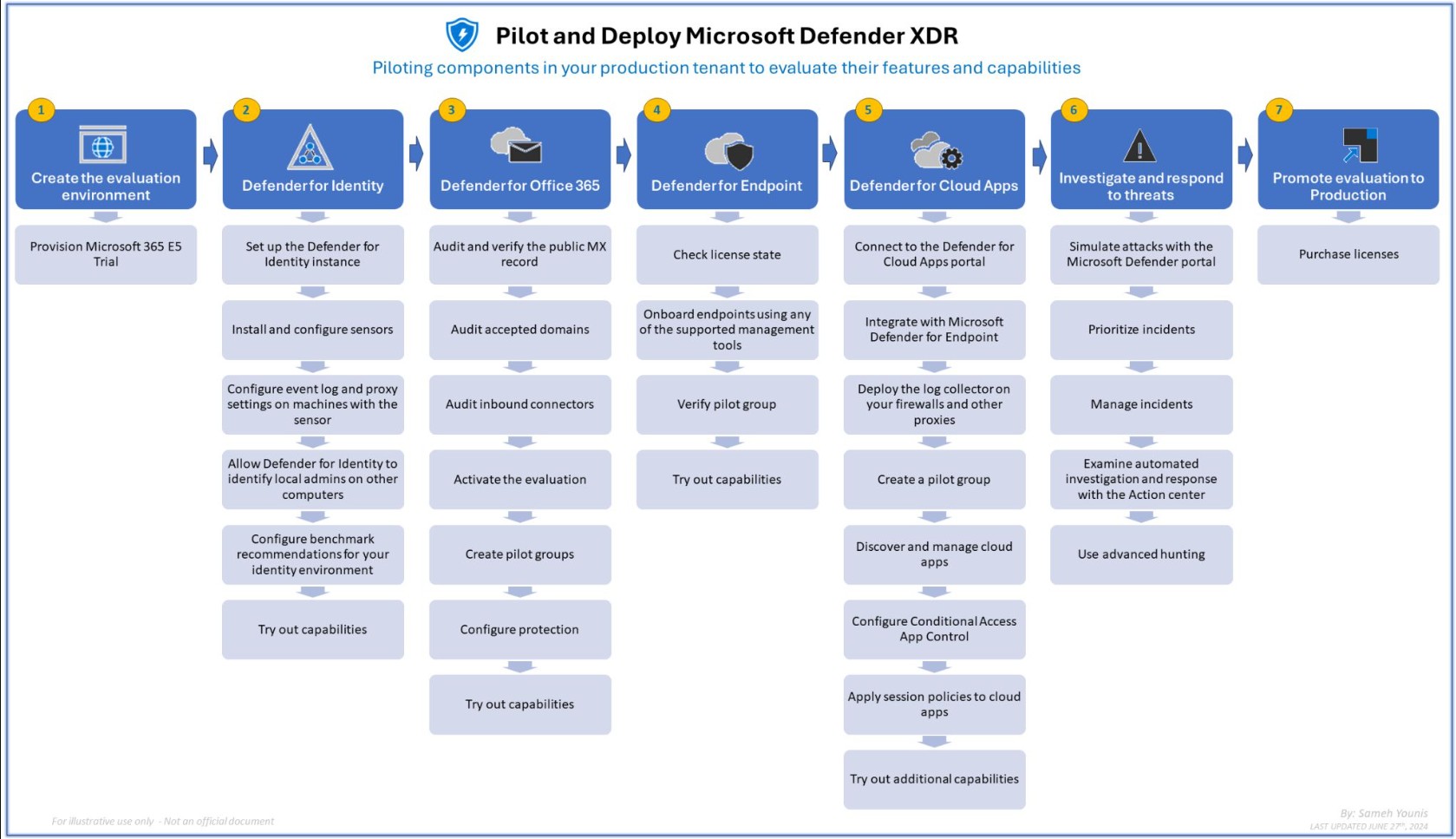
Picture Credit: SAMEH YOUNIS (https://www.linkedin.com/posts/samehyounis_cybersecurity-microsoftdefenderxdr-infographic-activity-7212063315408171008-3XWa
Central Topic: Extended Detection and Response (XDR)
Main Branches:
- Core Components:
- Endpoints: Coverage of devices, including laptops, desktops, and mobile devices.
- Cloud: Protection for cloud workloads, infrastructure, and applications.
- Email: Security for email systems and users.
- Identity: Protection for user identities and access.
- Server: Security for servers and other network infrastructure.
- Key Capabilities:
- Threat Detection: Identifying potential threats and vulnerabilities.
- Incident Response: Responding to identified threats and mitigating risks.
- Threat Hunting: Proactively searching for threats and vulnerabilities.
- Alerting and Reporting: Generating alerts and providing reports on detected threats.
- Integration Points:
- SIEM: Integration with Security Information and Event Management (SIEM) systems for centralized logging and analysis.
- Threat Intelligence: Integration with threat intelligence feeds for proactive threat detection.
- Other Security Tools: Integration with other security tools and platforms for comprehensive protection.
- Use Cases:
- Endpoint Detection and Response (EDR): Focusing on endpoint security and threat detection.
- Cloud Security Posture Management (CSPM): Assessing and managing cloud security posture.
- Identity Threat Detection: Identifying and mitigating identity-related threats.
- Benefits:
- Improved Threat Detection: Enhanced visibility and detection of threats across the entire organization.
- Faster Incident Response: Streamlined and efficient incident response processes.
- Reduced Attack Surface: Proactive threat hunting and vulnerability management.
- Compliance: Meeting regulatory requirements and industry standards.
Optional Sub-branches:
- Specific XDR Platforms: (e.g., Microsoft Defender XDR, CrowdStrike Falcon, TrendMicro).
- XDR vs. EDR: Comparing and contrasting XDR and EDR.
- XDR Implementation Steps: Planning, deployment, and configuration of XDR.
By organizing XDR information in a mind map, you can gain a more comprehensive understanding of the technology and its applications, as well as its role in modern cybersecurity.
For further reading, study this: MicrosoftDefender_MindMap-1.pdf