 Reading Time: 4 minutes
Reading Time: 4 minutes

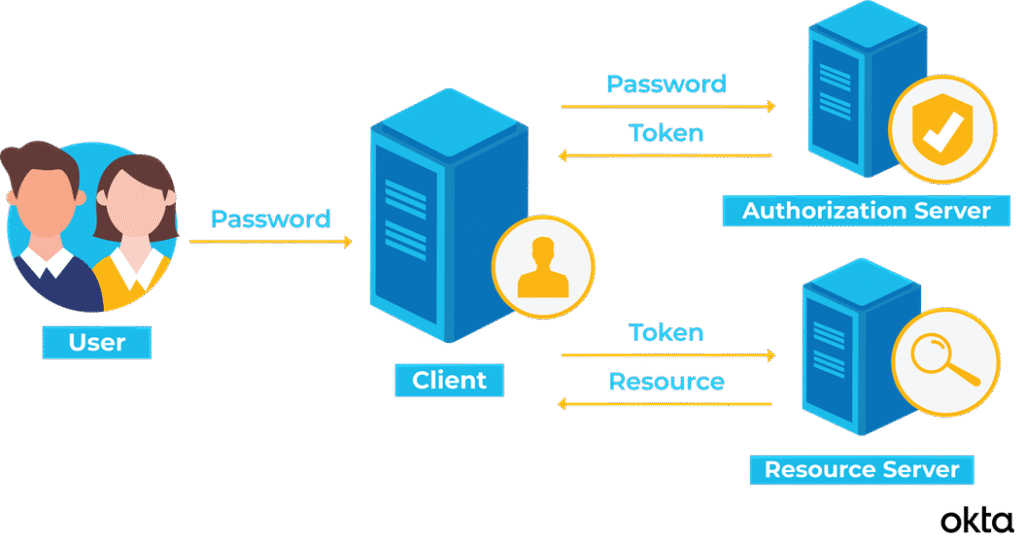
Image Source: TokenBasedAuthentication2.png (3121×1648)
Developing an authentication server is a crucial part of building secure applications. Here’s a structured approach to creating one:
1. Define Your Authentication Method: Decide whether you’ll use:
- Username & Password (traditional but requires good security practices)
- OAuth 2.0 & OpenID Connect (common for APIs and third-party logins)
- JWT (JSON Web Tokens) (lightweight, stateless authentication)
- Multi-Factor Authentication (MFA) (adds security layers)
- Biometric or Social Logins (for enhanced user experience)
2. Choose a Tech Stack: Pick a language and framework:
- Backend: Node.js with Express, Python with Flask/Django, Java with Spring, Go, etc.
- Database: MySQL, PostgreSQL, MongoDB, Redis (for sessions)
- Security Libraries: bcrypt for hashing passwords, Passport.js, Firebase Auth, Auth0
3. Implement User Authentication
- Registration: Store securely hashed passwords using bcrypt or Argon2.
- Login: Verify credentials and issue tokens (JWT or session-based).
- Token Handling: Generate JWT with expiration, use refresh tokens securely.
- Session Management: Decide whether to use cookies or token-based authentication.
4. Secure Your Server
- Encrypt Data: Use SSL/TLS for secure communication.
- Validate Inputs: Prevent SQL injection and other vulnerabilities.
- Rate Limiting: Protect against brute-force attacks.
- Use Environment Variables: Store secrets securely.
5. Add Authorization (Roles & Permissions)
- Define different roles (Admin, User, Guest).
- Restrict access to sensitive routes.
- Use middleware to enforce permissions.
6. Deploy & Monitor
- Containerization: Use Docker for scalability.
- Cloud Hosting: Deploy with AWS, Azure, or Google Cloud.
- Logging & Monitoring: Track suspicious activity using tools like Prometheus or ELK.
Tools you should use for building an authentication server: Building an authentication server requires a mix of tools for security, data management, and scalability. Here are some essential ones:
1. Authentication & Security
- bcrypt or Argon2 (for password hashing)
- OAuth 2.0 & OpenID Connect (for third-party authentication)
- JSON Web Tokens (JWT) (for secure stateless authentication)
- Auth0 / Firebase Auth / Okta (prebuilt authentication solutions)
- 2FA libraries (like Google Authenticator or Twilio Verify)
2. Backend & APIs
- Express.js (Node.js) / Flask / Django / Spring Boot (server-side frameworks)
- GraphQL / REST APIs (for communication between client and server)
- Postman (for API testing)
3. Database & Storage
- PostgreSQL / MySQL / MongoDB (for storing user credentials)
- Redis (for session management and caching)
- Vault by HashiCorp (for managing API keys & secrets)
4. Encryption & Security Best Practices
- SSL/TLS (for encrypting communication)
- CORS & CSRF Protection (to secure requests)
- Rate Limiting (e.g., express-rate-limit) (to prevent brute-force attacks)
5. Deployment & Monitoring
- Docker (for containerizing your authentication server)
- Kubernetes (for scalable deployment)
- Prometheus & Grafana (for monitoring)
- Cloud Services (AWS Cognito, Azure AD, Google IAM) (for authentication in cloud-based applications)
Best practices for secure authentication servers: Building a secure authentication server requires careful implementation of best practices to protect user data and prevent unauthorized access. Here are some essential guidelines:
1. Secure Password Handling
- Use strong password hashing algorithms like bcrypt or Argon2.
- Enforce password complexity requirements (length, special characters, etc.).
- Implement rate limiting to prevent brute-force attacks.
2. Use Secure Authentication Methods
- Prefer OAuth 2.0, OpenID Connect, or SAML for authentication.
- JSON Web Tokens (JWT) should include expiration and be signed using RS256 or HS256.
- Enable Multi-Factor Authentication (MFA) for added security.
3. Encrypt Data & Secure Transmission
- Use TLS/SSL to encrypt data in transit.
- Store sensitive information using AES encryption.
- Do not expose credentials in URLs or logs.
4. Secure APIs & Access Management
- Implement Role-Based Access Control (RBAC) or Attribute-Based Access Control (ABAC).
- Use access tokens with proper expiration and renewal mechanisms.
- Validate API requests using CORS policies and CSRF protection.
5. Protect Against Common Threats
- Implement rate limiting to prevent credential stuffing attacks.
- Use security headers like `X-XSS-Protection`, `Content-Security-Policy`, and `Strict-Transport-Security`.
- Sanitize and validate all inputs to prevent SQL injection and XSS.
6. Log, Monitor, and Audit
- Maintain audit logs of authentication attempts.
- Use tools like ELK Stack, Prometheus, Grafana for monitoring.
- Detect suspicious activity with intrusion detection systems (IDS).
7. Use Secure Session Management
- Prefer short-lived access tokens with refresh tokens.
- Set secure cookies with `HttpOnly` and `SameSite` attributes.
- Automatically log out inactive users after a set period.
When developing your own authentication server, it’s crucial to follow established security control frameworks to ensure robust protection against threats. Here are some recommended frameworks:
1. NIST Cybersecurity Framework (CSF)
- Provides a structured approach to managing cybersecurity risks.
- Focuses on Identify, Protect, Detect, Respond, and Recover functions.
- Helps in securing authentication mechanisms and access control.
2. ISO/IEC 27001
- An international standard for Information Security Management Systems (ISMS).
- Covers risk management, security policies, and continuous improvement.
- Ensures compliance with global security standards for authentication systems.
3. CIS Controls
- Developed by the Center for Internet Security (CIS).
- Includes 20 critical security controls to protect authentication servers.
- Covers access control, secure configurations, and monitoring.
4. OWASP Application Security Verification Standard (ASVS)
- Defines security requirements for authentication and access control.
- Helps in implementing secure password storage, session management, and multi-factor authentication.
- Ensures protection against common vulnerabilities like credential stuffing and brute-force attacks.
5. Zero Trust Architecture (ZTA)
- Based on the principle of never trust, always verify.
- Requires continuous authentication and authorization checks.
- Helps in securing APIs and user authentication workflows.
6. IdentityServer & OAuth 2.0 Framework
- IdentityServer8 is an OpenID Connect and OAuth 2.0 framework.
- Provides centralized authentication and access control for APIs.
- Supports single sign-on (SSO), federated identity, and token-based authentication.
7. Role-Based & Attribute-Based Access Control (RBAC & ABAC)
- RBAC assigns permissions based on user roles.
- ABAC considers attributes like user location, device, and risk level.
- Helps in enforcing fine-grained access control policies.