 Reading Time: 7 minutes
Reading Time: 7 minutes

Status: Final Blueprint
Author: Shahab Al Yamin Chawdhury
Organization: Principal Architect & Consultant Group
Research Date: March 27, 2025
Location: Dhaka, Bangladesh
Version: 1.0
1. Executive Summary
Cybersecurity assessment frameworks are structured methodologies guiding organizations to establish and maintain robust cybersecurity postures. They provide a roadmap for identifying, assessing, and managing risks to digital assets, enhancing resilience, streamlining operations, and building trust. Cybersecurity is a core business enabler, requiring agile, adaptive security, strong governance, and leveraging a complementary ecosystem of frameworks to tailor security to unique needs. This blueprint provides a deep understanding of frameworks, their components, comparative analysis, strategic implementation, performance measurement, and financial considerations.
2. Introduction to Cybersecurity Assessment Frameworks
Defining Cybersecurity Frameworks: Purpose and Principles
Cybersecurity frameworks are structured guidelines designed to help organizations establish a strong cybersecurity posture. They serve as a roadmap for identifying, assessing, and managing risks to digital assets, safeguarding systems, and meeting regulatory compliance. Key principles include standardization and adaptability. NIST CSF 2.0, for example, includes Govern, Identify, Protect, Detect, Respond, and Recover functions, emphasizing a systematic approach to risk management.
The Imperative for Structured Cybersecurity: Benefits
Adopting a structured framework offers significant benefits: improved risk management, regulatory compliance, operational efficiency, enhanced trust and reputation, cost savings, increased organizational awareness, and improved incident response capabilities.
Evolution and Current Landscape
Cybersecurity frameworks continuously evolve, with regular updates (e.g., NIST CSF 2.0 in 2024) to adapt to new threats and expand applicability. A key trend is increasing interoperability and alignment among different frameworks (e.g., CIS Controls with NIST CSF, GDPR, ISO 27001), allowing for comprehensive and tailored security strategies. The emphasis on cybersecurity governance signifies its recognition as a strategic business concern.
3. Core Components of Cybersecurity Assessment
Principles of Effective Cybersecurity Assessment
Effective assessment is guided by: a risk-based approach, continuous improvement, a holistic view (people, processes, technology, third-party risks), clarity and communication, and a proactive stance.
Governance of Cybersecurity Programs
Cybersecurity governance is the blueprint guiding an organization’s approach to protecting digital assets, encompassing policies, procedures, and processes for management and monitoring. It aligns cybersecurity strategies with business objectives and ensures compliance. Key activities include establishing decision-making hierarchies, assigning responsibilities (e.g., CISO), defining risk appetite, and setting up oversight processes.
Risk Management and Analysis: Impact, Risk, Control
This systematic process identifies, analyzes, and evaluates potential threats, vulnerabilities, and their impacts on digital assets. Steps include: identifying and prioritizing assets; assessing cyber threats and vulnerabilities; analyzing and prioritizing risks; implementing security controls; and continuous monitoring and review. The Business Impact Analysis (BIA) is crucial for understanding potential consequences of disruptions and prioritizing recovery plans.
Compliance and Regulatory Landscape (GDPR, HIPAA, PCI DSS, CCPA, etc.)
Frameworks are indispensable for navigating complex regulatory landscapes and ensuring compliance with mandates like GDPR, HIPAA, PCI DSS, and CCPA, thereby avoiding costly fines and reputational damage. Many frameworks (e.g., NIST, ISO 27001, CIS Controls) align with these regulations, allowing for a unified approach to control implementation.
Critical Data Identification and Protection
Protecting critical digital assets is a core purpose of cybersecurity frameworks, ensuring confidentiality, integrity, and availability (CIA triad). This involves: identification (inventory and classification); protection measures (encryption, access control, DLP, secure configurations); and data recovery capability.
Cybersecurity Lifecycle Management (Identify, Protect, Detect, Respond, Recover)
This continuous, cyclical process manages and protects information systems from evolving threats. The NIST Cybersecurity Framework (CSF) provides a widely recognized model: Identify, Protect, Detect, Respond, and Recover. NIST CSF 2.0 added Govern to emphasize strategic oversight.
Roles, Responsibilities, and RACI Matrix for Implementation
Establishing clear accountability and seamless collaboration is paramount. The RACI matrix (Responsible, Accountable, Consulted, Informed) clarifies roles and responsibilities for tasks like threat detection, incident response, and risk management, enhancing team performance and streamlining decision-making.
4. Leading Cybersecurity Assessment Frameworks: A Deep Dive and Comparison
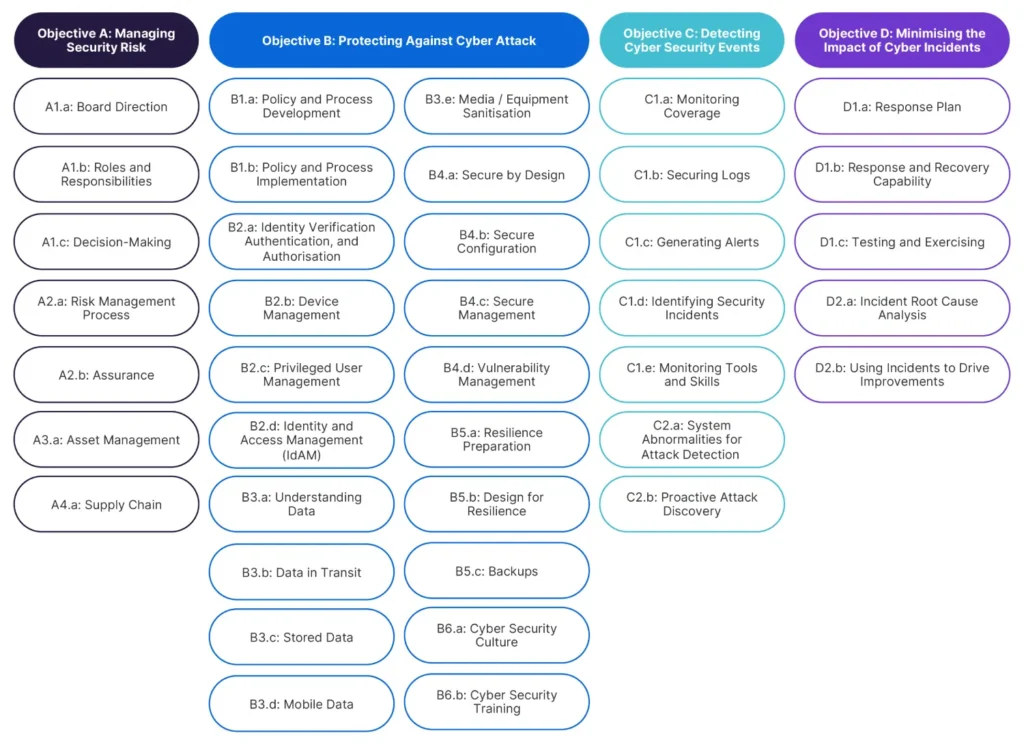
- NIST Cybersecurity Framework (CSF): Voluntary guide for managing and reducing cybersecurity risks for any organization size or sector. Flexible, outcome-driven, strong U.S. government alignment.
- ISO/IEC 27001 & 27002: International standard for establishing, implementing, and improving an Information Security Management System (ISMS). Globally recognized, certifiable, systematic risk management.
- CIS Critical Security Controls (CIS Controls): Prescriptive, prioritized set of best practices to strengthen cybersecurity and defend against pervasive attacks. Highly practical, cost-effective, excellent for SMBs.
- COBIT (Control Objectives for Information and Related Technologies): Comprehensive framework for IT governance, risk management, and cybersecurity. Strong IT-business alignment, comprehensive GRC, suitable for large enterprises.
- FAIR (Factor Analysis of Information Risk): International standard quantitative model for information security and operational risk, quantifying cyber risk in financial terms. Provides financial risk quantification, aids executive communication, complements other frameworks.
- Other Notable Frameworks: Include MITRE ATT&CK® (adversary tactics), Cyber Defense Matrix (visualizing capabilities), CMMC 2.0 (DoD contractors), C2M2 (maturity in critical infrastructure), and OCTAVE (organizational risk assessment).
5. Strategic Implementation and Operationalization
Cybersecurity Strategy and Planning
A robust strategy is a dynamic roadmap for protecting a business from threats, continuously adapting to emerging risks. It involves risk assessment, goal setting, framework selection, policy development, and continuous evaluation. Core principles include Defense-in-Depth and Zero Trust.
Agile Cybersecurity Framework Implementation
An agile strategy is built on continuous improvement, rapid response, and proactive threat mitigation, well-suited for dynamic cybersecurity environments. It involves continuous risk assessment, adaptive security technologies, collaborative security culture, and incident response agility.
Standard Practices and Best Practices for Adoption
Effective adoption requires: regular asset inventories, MFA, automated threat detection, incident response drills, up-to-date backups, strong passwords, robust patch management, secure configurations, and employee education. It also involves customizing frameworks and avoiding pitfalls like underestimating scope or focusing solely on compliance.
Operational Requirements and Execution
Translating strategy into tangible measures involves: continuous inventory of assets and software, secure configuration, effective account management, continuous vulnerability management, audit log management, and robust data recovery capabilities. Operational Technology (OT) cybersecurity requires specific attention.
Quality Assurance and Reliability in Implementation
Ensuring quality involves: regular testing and validation (penetration testing, vulnerability assessments, security audits); continuous monitoring (enhanced by automation); evidence collection for audit readiness; and incident response testing.
Design and Platform Considerations
Framework implementation is tied to thoughtful design and platform selection. Frameworks act as a design blueprint and are increasingly designed for platform integration (e.g., NIST CSF linking to resources for various tools). Cloud and hybrid environments are critical considerations, with frameworks adapting to their unique challenges. Automation is a key design principle for efficiency and scalability.
Integration with Existing Enterprise Systems and Tools
Successful integration is crucial for a unified security posture. Frameworks like COBIT are designed for easy integration with other IT standards. Specialized tools are critical, including SIEM (Security Information and Event Management), XDR (Extended Detection and Response), SOAR (Security Orchestration, Automation, and Response), vulnerability assessment platforms, penetration testing tools, and threat intelligence platforms.
Support and Monitoring Mechanisms
Robust support and continuous monitoring are essential: continuous monitoring (enhanced by automation); telemetry (continuous data collection and analysis from IT infrastructure); observability (granular, comprehensive views into system states); and security ratings (objective measurements of performance).
6. Measuring Performance and Maturity
Key Performance Indicators (KPIs) for Cybersecurity Assessment
KPIs are measurable values assessing security strategy effectiveness, tracking threat detection, incident response, and vulnerability management. They provide data-driven insights and “proof of impact”. KPIs are categorized into: Tactical Metrics (e.g., # incidents, MTTD, MTTR), Operational Metrics (e.g., Patch Compliance Rate, Security Posture Score), and Strategic Metrics (e.g., CMM Level, Business Risk Alignment).
Cybersecurity Maturity Models
Maturity models assess the sophistication of an organization’s cybersecurity program, helping identify areas for improvement and prioritize enhancements. Key models include: NIST Cybersecurity Framework Tiers (Partial, Risk-Informed, Repeatable, Adaptive), ISO 27000, CIS Controls Implementation Groups (IGs), and C2M2 (Cybersecurity Capability Maturity Model).
Performance Evaluation and Continuous Improvement
Performance evaluation is integral to continuous improvement. Frameworks are not static; they require regular updates to adapt to new threats and changes within the organization. This involves continuous monitoring, regular audits, and assessments to ensure effectiveness.
Roadmaps for Maturity Advancement
Maturity models inherently provide roadmaps. For example, NIST Tiers offer a clear progression from reactive to adaptive security, guiding strategic planning and investment justification.
7. Challenges and Pitfalls in Framework Adoption
Common Struggles and Barriers to Effective Governance
Organizations face several challenges: framework complexity, fostering a cybersecurity culture, technical challenges (integration, standardization, automation), resource limitations (staff, budget, tools), regulatory complexity, misalignment with business processes, rapidly evolving threat landscape, and difficulty in measuring performance.
Common Pitfalls in Cybersecurity Assessments
Mistakes during assessments include: underestimating scope and resources, insufficient documentation and evidence, lack of communication and collaboration, neglecting pre-audit assessments and remediation, focusing solely on compliance (not true security), poor cyber hygiene, uncontrolled administrative privileges, and neglecting employee education.
8. Financial Considerations: Total Cost of Ownership (TCO) and Return on Investment (ROI)
Calculating TCO for Cybersecurity Framework Implementation
Total Cost of Ownership (TCO) in cybersecurity encompasses all costs associated with implementing, maintaining, and managing security measures over their lifetime, including direct (licensing, hardware, training) and indirect costs (business continuity, staff productivity). For example, NIST CSF implementation can range from $10,000 to $35,000, while ISO 27001 certification can range from $6,000 to over $75,000 for a three-year cycle.
Evaluating ROI of Cybersecurity Frameworks
Return on Investment (ROI) in cybersecurity measures the return on security investments, often quantified by “cost avoidance.” It helps organizations align security initiatives with business objectives, evaluate control effectiveness, optimize spending, and communicate value to stakeholders. Benefits include reduced risk, improved compliance, and avoided losses from breaches (financial, reputational, operational downtime, fines). The FAIR model explicitly quantifies cyber risk in financial terms, enabling cost/benefit analysis and informed decision-making.
9. Conclusions and Recommendations
Strategic Imperatives for Enterprise Cybersecurity
Cybersecurity must be integrated as a strategic business enabler, not just an IT function. This requires continuous adaptation through agile methodologies, strong governance, and a complementary ecosystem of frameworks tailored to unique organizational needs.
Actionable Recommendations for Principal Architects
- Champion Integrated Framework Adoption: Advise clients to select a primary framework (e.g., NIST CSF or ISO 27001) complemented by specialized frameworks (e.g., CIS Controls for hygiene, FAIR for quantitative risk, MITRE ATT&CK for threat intelligence) to build a comprehensive, tailored security posture.
- Prioritize Governance & Executive Buy-in: Emphasize establishing clear governance structures, roles (RACI), and accountability to ensure C-suite involvement and resource allocation.
- Advocate for Quantitative Risk Management: Promote the adoption of methodologies like FAIR to translate cyber risks into financial terms, enabling data-driven investment justification and strategic decision-making.
- Integrate Agile Methodologies: Recommend agile approaches for framework implementation to foster continuous improvement, rapid adaptation to evolving threats, and efficient resource utilization.
- Invest in Advanced Monitoring & Observability: Guide clients towards solutions that leverage comprehensive telemetry and AI/ML for proactive threat detection, predictive planning, and enhanced operational resilience.
- Focus on Foundational Cyber Hygiene: Stress the critical importance of consistent operational execution of basic controls (asset inventory, patch management, secure configurations, access control) as the bedrock for any advanced security program.
- Leverage Automation: Encourage the use of automation tools for compliance, continuous monitoring, and incident response to overcome resource limitations and improve efficiency.
- Ensure Continuous Training & Awareness: Highlight the human element as a critical defense layer, advocating for regular, mandatory security awareness training for all employees.
Chat for Professional Consultancy Services
