 Reading Time: 4 minutes
Reading Time: 4 minutes

Status: Final Blueprint
Author: Shahab Al Yamin Chawdhury
Organization: Principal Architect & Consultant Group
Research Date: July 23, 2025
Location: Dhaka, Bangladesh
Version: 1.0
Executive Summary
Continuous Threat Exposure Management (CTEM) marks a strategic evolution from reactive, incident-driven security to a proactive, business-aligned framework for managing cyber risk. As digital attack surfaces expand, traditional periodic security assessments have become insufficient. CTEM provides a continuous, five-stage program to systematically identify, prioritize, validate, and remediate cyber exposures across an organization’s entire asset landscape. The core objective is to shift security efforts “left of breach” by addressing potential weaknesses before adversaries can exploit them. By aligning security operations with business-critical functions, CTEM translates technical vulnerabilities into quantifiable business impact, enabling strategic decision-making and demonstrably improving organizational resilience.
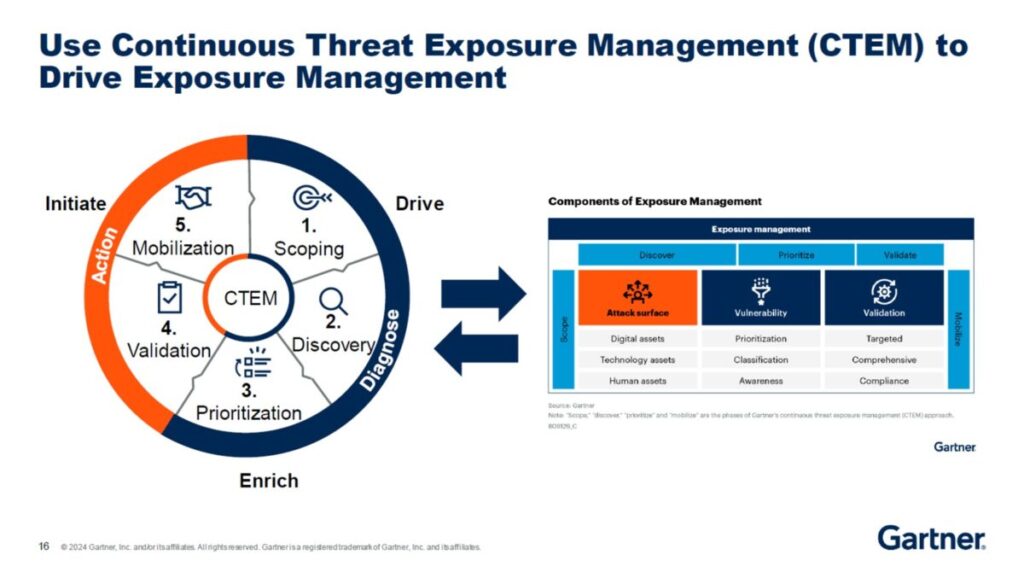
The Five-Stage CTEM Lifecycle
CTEM operates as a continuous, iterative cycle where each stage informs the next, ensuring the program adapts to changes in the business and threat landscape.
1. Scoping: Aligning Security with Business Priorities
The Scoping stage defines the operational boundaries for a CTEM cycle, ensuring security efforts are precisely aligned with business objectives. This foundational phase requires collaboration between security and business leaders to identify “crown jewel” assets and systems most critical to revenue, operations, and compliance. The output is a documented scope that guides all subsequent activities, focusing resources on protecting what matters most.
2. Discovery: Illuminating the Attack Surface
The Discovery stage executes a comprehensive and continuous search for all in-scope assets and their associated exposures. This goes beyond traditional vulnerability scanning to uncover a wide array of weaknesses, including misconfigurations, identity and access issues, and shadow IT across on-premises, cloud, and external environments. The goal is to create a complete and continuously updated inventory of potential risks.
3. Prioritization: Focusing on Material Risk
Prioritization shifts the security mindset from an impossible mandate to “fix everything” to a strategic goal to “fix what matters”. This stage moves beyond static CVSS scores to a multi-factor risk model that incorporates threat intelligence, real-world exploitability (e.g., EPSS), asset criticality, and the presence of compensating controls. A key technique is attack path analysis, which identifies exposures that act as critical “choke points” in potential kill chains leading to high-value assets.
4. Validation: Confirming Real-World Exploitability
The Validation stage provides empirical, evidence-based proof of risk by testing whether prioritized exposures are actually exploitable in the organization’s specific environment. Methodologies include Breach and Attack Simulation (BAS) and penetration testing to safely simulate real-world attack scenarios. This stage eliminates false positives and provides the tangible evidence needed to drive consensus and action between security and IT teams.
5. Mobilization: Driving Remediation and Improvement
Mobilization is the action phase where validated insights are translated into concrete risk reduction. This involves orchestrating cross-functional remediation workflows, often by integrating with ITSM systems like ServiceNow or Jira to assign, track, and verify fixes. The outcomes and metrics from this stage, such as Mean Time to Remediate (MTTR), feed directly back into the Scoping phase of the next cycle, ensuring continuous improvement.
The CTEM Prioritization Matrix
To translate complex risk scoring into an actionable format, a visual prioritization matrix is an essential tool for all stakeholders. It provides a multi-dimensional view that immediately communicates both risk and the required urgency of action.
| Business Impact | Low Exploitability Likelihood | Medium Exploitability Likelihood | High Exploitability Likelihood | Actively Exploited (KEV) |
| Critical | Monitor & Plan: High-impact exposures that are currently difficult to exploit. Schedule for future remediation cycles or architectural review. | Remediate (High Priority): Significant business risk. Plan remediation within the next patch cycle. | Remediate Urgently: Critical business risk with a high probability of exploitation. Requires immediate attention. | REMEDIATE IMMEDIATELY: Active threat to critical business functions. Initiate emergency patching and incident response protocols. |
| High | Track & Review: Exposures on important systems that are not currently targeted. Review quarterly. | Schedule Remediation: Important risks that should be addressed in upcoming, planned maintenance windows. | Remediate (High Priority): High-impact exposures that are likely to be targeted. Address within the next patch cycle. | Remediate Urgently: Confirmed threat to high-value assets. Requires immediate attention and potential compensating controls. |
| Medium | Defer / Accept Risk: Low-impact, low-likelihood exposures. Formally accept risk or place in a long-term backlog. | Mitigate / Schedule Patching: Moderate risks. Can be addressed through routine patching schedules. | Schedule Remediation: Exposures that could cause moderate disruption. Address in upcoming maintenance windows. | Remediate (High Priority): Active threats that could cause operational disruption. Address promptly. |
| Low | Informational / Accept Risk: Minimal risk to business operations. Accept risk or address opportunistically. | Defer / Accept Risk: Low-impact exposures. Address if resources permit, otherwise accept risk. | Mitigate / Schedule Patching: Address through routine patching to maintain security hygiene. | Schedule Remediation: Active but low-impact threats. Address in routine patching cycles. |
Strategic Implementation & Recommendations
Adopting a CTEM program is a journey of maturation best approached in phases. Start with a foundational pilot program on a narrow but high-value scope, such as the external attack surface, to demonstrate value quickly. Subsequently, expand the program to cover more of the attack surface and additional business units. Finally, optimize the program by integrating automation and maturing metrics to focus on business-level outcomes like quantified risk reduction.
For enterprise leadership, the strategic imperatives are to:
- Champion a Culture of Shared Responsibility: CTEM requires breaking down silos. Foster collaboration between security, IT, and business units with executive sponsorship and clear governance.
- Invest in Integrated Platforms: Move away from tool sprawl. Prioritize unified exposure management platforms that can orchestrate the flow of data across the entire CTEM lifecycle.
- Measure and Communicate Business Value: Translate technical security data into the language of business impact. Use metrics and dashboards to continuously communicate the program’s performance and demonstrate a clear return on investment through measurable risk reduction.