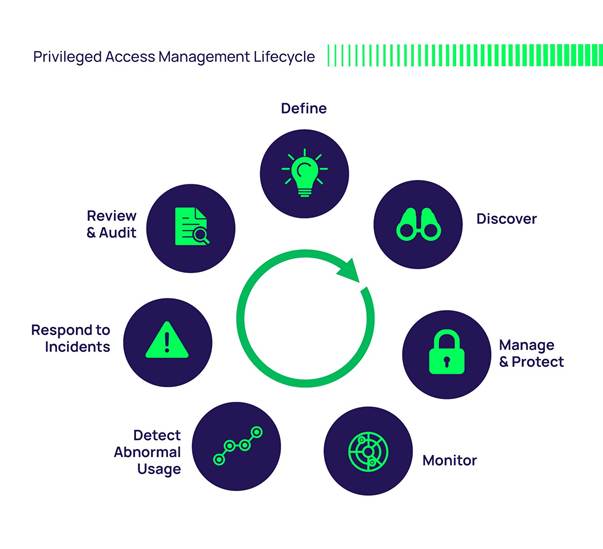
Reading Time: 4 minutesIntroduction In an era where cybersecurity threats are growing in complexity, organizations must continually adapt their security measures to protect sensitive information. Privileged Access Management (PAM) plays a critical role in safeguarding access to high-level accounts that control systems and Read More …