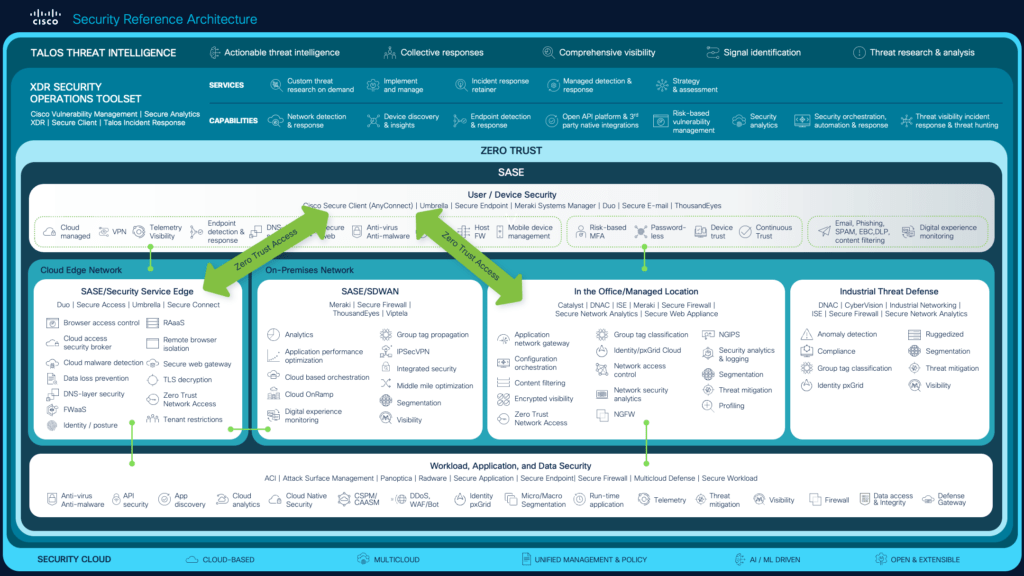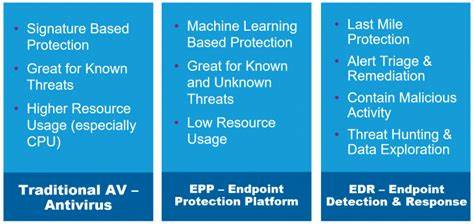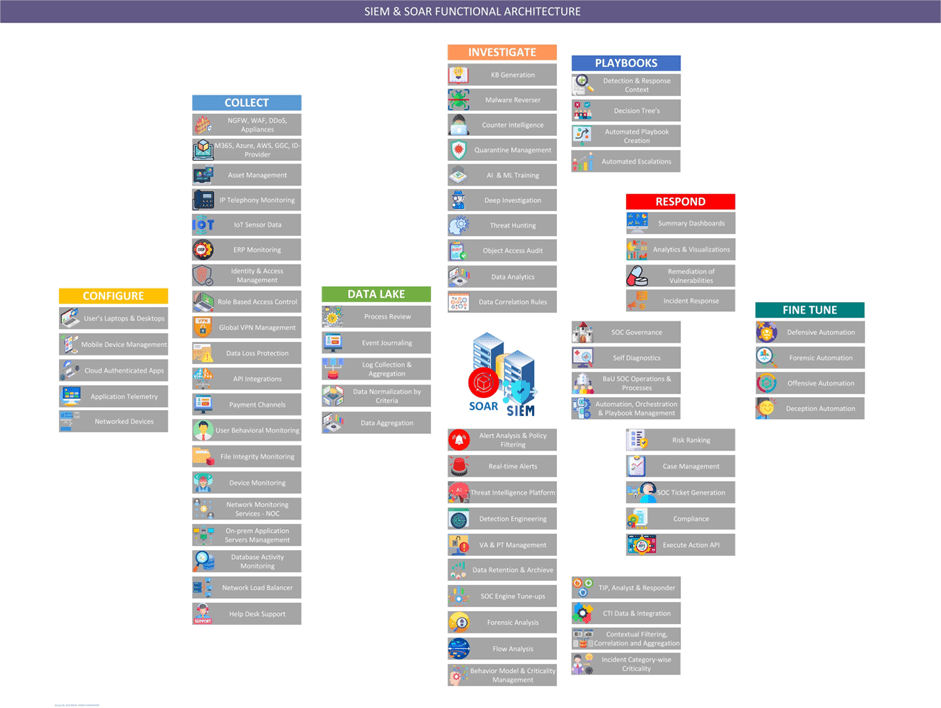
Reading Time: 2 minutesThe below picture illustrates operational architecture of the SIEM & SOAR in an integrated function: This is where the big picture comes in, from ingress to egress. As you can see in the picture the data collectors need to be configured in Read More …