 Reading Time: 3 minutes
Reading Time: 3 minutes

Status: Final Blueprint
Author: Shahab Al Yamin Chawdhury
Organization: Principal Architect & Consultant Group
Research Date: January 24, 2025
Location: Dhaka, Bangladesh
Version: 1.0
Introduction: The CISO as a Strategic Business Partner
The modern Chief Information Security Officer (CISO) has evolved from a technical manager into a strategic business leader. In an era of enterprise-wide digital transformation, the CISO’s primary mandate is to architect digital trust, enabling secure business growth while managing cyber risk. This playbook provides a blueprint for establishing a mature, resilient, and business-aligned security program. Success hinges on strategic influence, robust governance, operational excellence, and a forward-looking perspective.
Part 1: Strategy, Governance, and Influence
A successful security program is built on a foundation of clear strategy, strong governance, and effective stakeholder management.
The CISO’s First 180 Days: A structured approach is critical for making an immediate impact and building credibility.
- Days 1-30 (Understand & Assess): Focus on listening and learning. Meet with key stakeholders (CEO, CFO, CIO), review existing documentation (audits, policies), and assess the security team’s capabilities and morale.
- Days 31-90 (Prioritize & Plan): Avoid “boiling the ocean.” Identify 2-3 high-impact, achievable “quick wins” to build momentum. Draft and socialize an interim security strategy and charter.
- Days 91-180 (Execute & Report): Deliver on the quick wins, establish formal governance forums, and report progress to all stakeholders, solidifying your brand as a credible and effective leader.
Governance and Frameworks: Governance provides the structure and authority for the security program.
- Hybrid Framework Model: The most effective approach is to leverage multiple frameworks. Use the NIST Cybersecurity Framework (CSF) for high-level structure and communication, map detailed controls from ISO/IEC 27002 for implementation guidance, and integrate processes from COBIT for formal governance and auditability.
- Risk Management: Implement a continuous risk management lifecycle (Frame, Assess, Respond, Monitor). Translate technical risks into financial terms using Cyber Risk Quantification (CRQ) to have meaningful conversations with the CFO and the board.
- RACI Matrix: For critical processes like incident response, a RACI (Responsible, Accountable, Consulted, Informed) matrix is essential. It eliminates confusion during a crisis by clearly defining roles and responsibilities, demonstrating mature governance.
Part 2: Building a Resilient and Operationally Excellent Program
This section focuses on the tangible architectural strategies, measurement systems, and operational capabilities required to build a defensible enterprise.
Pillars of Modern Security Architecture:
- Zero Trust: Shift from implicit trust to a “never trust, always verify” model. Key components include strong identity (MFA), micro-segmentation, and least privilege access.
- Cloud-Native Security: Utilize Cloud-Native Application Protection Platforms (CNAPP) to integrate posture management (CSPM), workload protection (CWPP), and entitlement management (CIEM) for a holistic view of cloud risk.
- Data-Centric Security: Protect data throughout its lifecycle: discover and classify sensitive data, apply protection controls like encryption and DLP, and monitor for anomalous access.
Measurement, Maturity, and the Human Firewall:
- Maturity Models (CMM): Use a maturity model to assess and communicate the program’s evolution from an initial, reactive state to an optimized, predictive one. This provides a clear roadmap for investment and improvement.
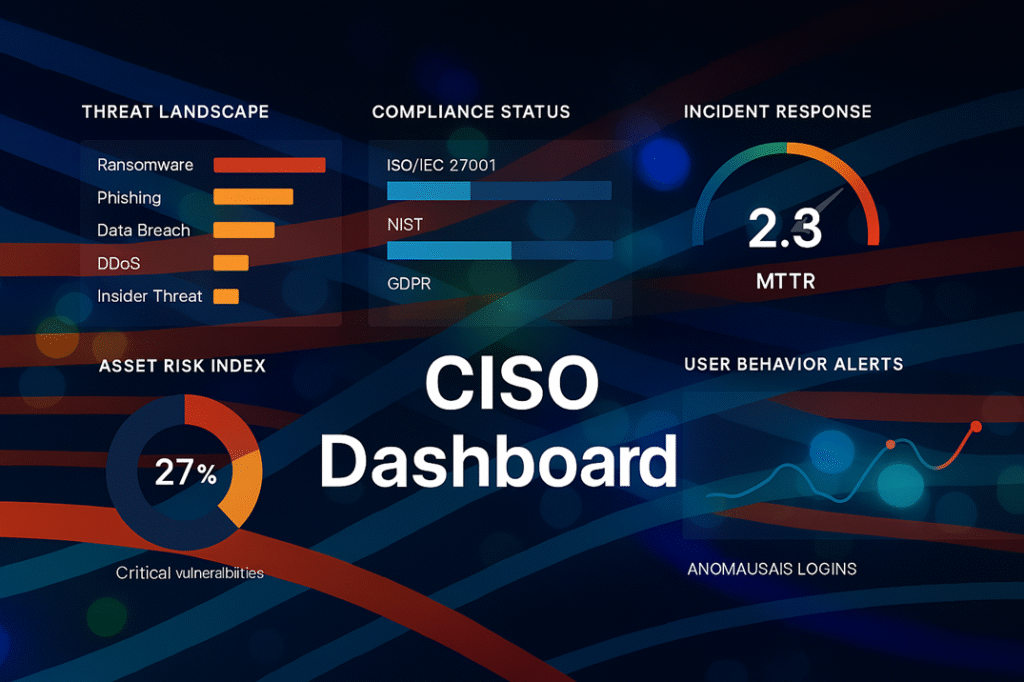
- The CISO Dashboard: Communicate value to the board with a dashboard focused on business-relevant Key Performance Indicators (KPIs), such as Security Posture Score, Mean Time to Resolve (MTTR), and Return on Security Investment (ROSI).
- Security Culture & Literacy: The “human firewall” is a critical defense layer. Cultivate a security-conscious culture through leadership engagement, non-punitive reporting, and continuous, role-based training reinforced with phishing simulations.
The Operational Engine (SOC & Incident Response):
- Modern SOC: The SOC is the command center for defense. Choose the right operating model (in-house, managed, or hybrid) and equip it with an essential technology stack: SIEM, EDR/XDR, and SOAR to automate workflows and combat analyst burnout.
- Incident Response (IR): Adopt the NIST IR Framework (Preparation, Detection & Analysis, Containment/Eradication/Recovery, Post-Incident Activity). Develop actionable playbooks for common, high-impact scenarios like ransomware to ensure a swift and coordinated response.
Part 3: The Future-Ready CISO
The CISO must be a perpetual change agent, navigating persistent challenges and embracing innovation.
Addressing Key Struggles:
- Burnout & Skills Gap: Combat alert fatigue with automation (SOAR) and address the skills gap by upskilling internal talent and strategically using managed services.
- Budget & ROI: Justify spending by consistently framing requests in terms of business value, risk reduction, and financial impact (CRQ).
The AI-Augmented CISO:
- AI for Defense: Leverage AI for predictive threat intelligence, advanced behavioral analytics, and automated incident response.
- AI Risk Management: Take a lead role in managing the risks of enterprise AI adoption, including data privacy, AI-powered attacks, and regulatory compliance.
Conclusion: The 3-Year Strategic Roadmap A forward-looking, multi-year strategic roadmap is essential for guiding the program’s evolution. By assessing the current state, defining a target maturity level, and creating a phased plan of initiatives, the CISO can secure long-term funding and demonstrate a clear, strategic vision to the board. The ultimate goal is to position the security program not as a cost center, but as a critical enabler of the enterprise’s future success.