 Reading Time: 2 minutes
Reading Time: 2 minutes

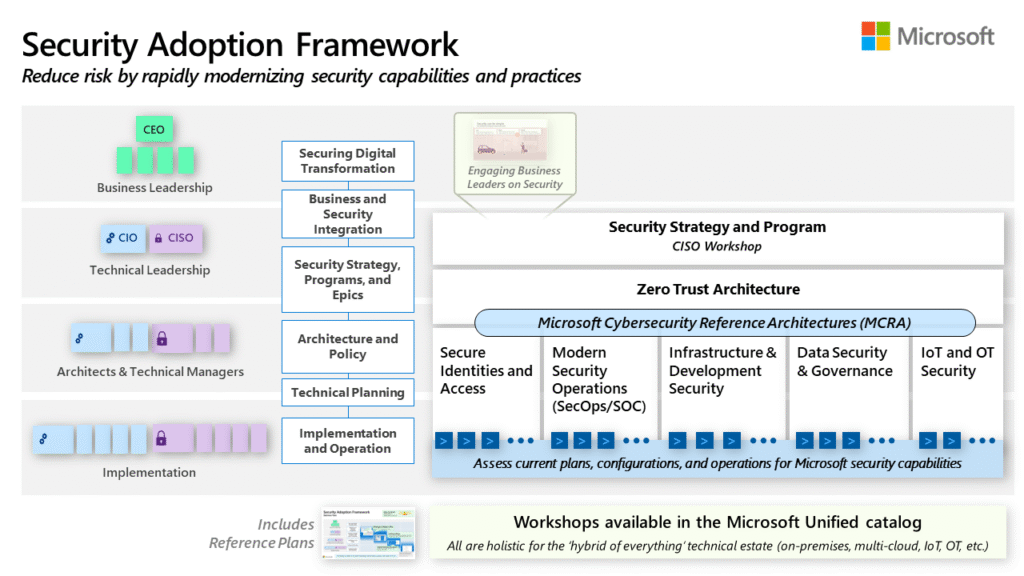
Image source: Security Adoption Resources | Microsoft Learn
Traditional security models that rely on a fortified perimeter are no longer enough. With the rise of remote work, cloud applications, and increasingly sophisticated cyber threats, organizations need a more dynamic and resilient strategy. Microsoft’s Zero Trust model offers a powerful framework to rapidly modernize your security posture.
This approach isn’t about building impenetrable walls around your network; it’s about shifting to a new mindset. As the name suggests, you “never trust, always verify.”
The Three Guiding Principles of Zero Trust
The Zero Trust model is built on three core principles, which are elegantly captured in a diagram on the Microsoft page. This visual shows how these principles should be applied across all aspects of your digital estate.
- Verify Explicitly: This is the cornerstone of Zero Trust. Instead of assuming a user or device is safe because it’s inside the corporate network, you must always authenticate and authorize based on all available data. This includes user identity, location, device health, service or workload, data classification, and known anomalies.
- Use Least Privileged Access: Grant users only the access they need, for only as long as they need it. This principle limits the potential damage a compromised account can cause. Implementing Just-In-Time and Just-Enough-Access (JIT/JEA) policies is critical. Think of it as giving out keys that only open specific doors for a limited time, rather than a master key that works everywhere, forever.
- Assume Breach: Don’t just prepare for the possibility of a breach—assume it has already happened or will happen. This proactive stance forces you to minimize the “blast radius” of an attack. By segmenting networks and encrypting all communications, you can prevent attackers from moving laterally across your systems to access more valuable assets.
Four Key Areas to Modernize
Microsoft outlines four critical areas where you should focus your modernization efforts based on the Zero Trust principles:
1. Identities
Identities—representing users, services, or devices—are a primary control plane. The goal is to move beyond simple passwords and strengthen authentication.
- Key Action: Implement multi-factor authentication (MFA) for all users. Better yet, adopt passwordless authentication methods like biometrics or authenticator apps for a more secure and user-friendly experience.
2. Endpoints & Devices
Every device accessing your network is a potential attack vector.
- Key Action: Onboard your endpoints into a modern Endpoint Detection and Response (EDR) or Extended Detection and Response (XDR) solution. This provides visibility into device health and compliance, allowing you to grant access only to secure and trusted devices.
3. Applications
Whether on-premises or in the cloud, your applications need to be secured.
- Key Action: Ensure applications are discovered, permissions are appropriate, and access is gated based on real-time analytics. Monitor for abnormal behavior and shadow IT to prevent unauthorized app usage.
4. Infrastructure
This includes everything from servers and virtual machines to containers and microservices.
- Key Action: Use telemetry to detect attacks and anomalies, automatically block and flag risky behavior, and enforce least privilege access across your entire infrastructure, whether it’s on-premises, in the cloud, or hybrid.
By focusing on these principles and areas, you can build a robust, flexible, and resilient security posture that is prepared for the challenges of the modern threat landscape.