 Reading Time: 5 minutes
Reading Time: 5 minutes

Status: Final Blueprint
Author: Shahab Al Yamin Chawdhury
Organization: Principal Architect & Consultant Group
Research Date: March 29, 2025
Location: Dhaka, Bangladesh
Version: 1.0
Executive Summary
This blueprint outlines a strategic and actionable plan for implementing the NIST Cybersecurity Framework (CSF) 2.0, the leading global standard for managing cyber risk. It emphasizes a proactive, governance-driven approach to enhance organizational resilience, optimize resource allocation, and streamline compliance, transforming cybersecurity into a core business enabler.
1. Introduction to the NIST Cybersecurity Framework 2.0
NIST CSF 2.0 is a flexible, risk-based framework for managing cybersecurity risks, applicable to any organization regardless of size or maturity. It emphasizes desired outcomes over prescriptive controls, fostering adaptability and clear communication.
1.1. Evolution, Purpose, and Guiding Principles of CSF 2.0
Published on February 26, 2024, CSF 2.0 expands its applicability beyond critical infrastructure to “any organization.” Its core purpose is to help manage and reduce cybersecurity risks through a non-prescriptive, outcome-driven, and adaptable methodology. The new “Govern” function highlights cybersecurity as an integral part of enterprise risk management.
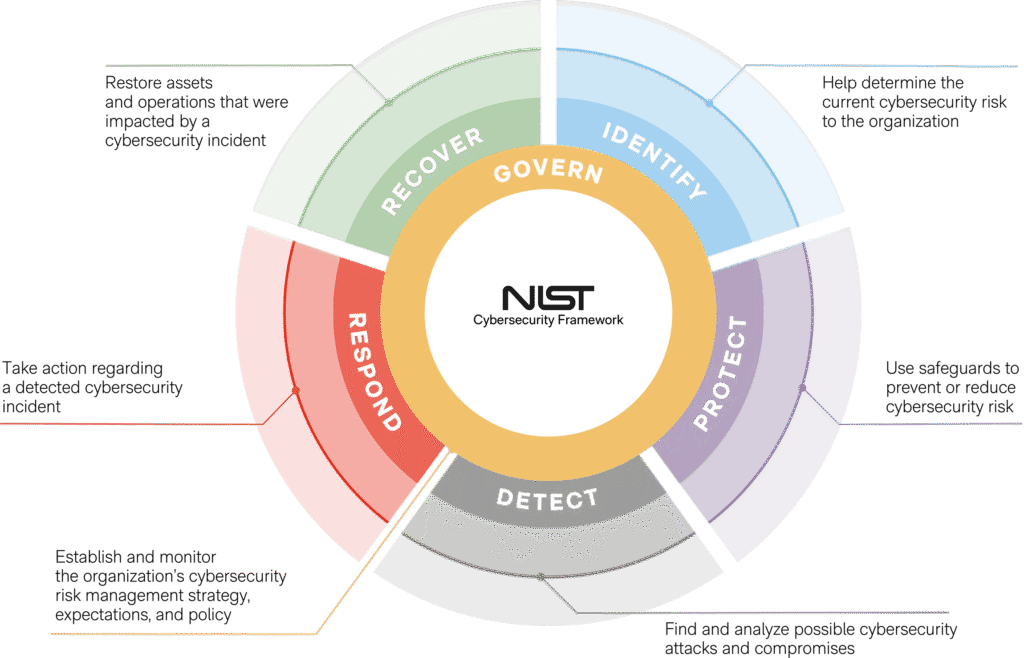
1.2. Core Components: Functions, Categories, Subcategories, and Informative References
The framework is structured hierarchically:
- Functions: Six high-level cybersecurity activities: GOVERN (GV), IDENTIFY (ID), PROTECT (PR), DETECT (DE), RESPOND (RS), and RECOVER (RC).
- Categories: Subdivide functions into specific areas (e.g., Asset Management under Identify).
- Subcategories: Most detailed level, outlining actionable tasks.
- Informative References: External resources (standards, guidelines, regulations) providing practical implementation guidance, dynamically updated online.
1.3. Understanding CSF Profiles and Implementation Tiers
- CSF Profiles: Tools to “understand, tailor, assess, and prioritize cybersecurity outcomes.” Organizations create a “Current Profile” (existing posture) and a “Target Profile” (desired state) to identify gaps and develop action plans. Community Profiles offer baseline starting points.
- Implementation Tiers: Four levels (Partial, Risk-Informed, Repeatable, Adaptive) describe the rigor and sophistication of an organization’s cybersecurity risk governance. They are not a traditional maturity model but guide continuous improvement, integrating cybersecurity into enterprise processes.
2. Strategic Implementation of NIST CSF 2.0
Implementation is an iterative, seven-step process integrating cybersecurity into an organization’s strategic and operational fabric.
2.1. The Seven-Step Implementation Process
- Prioritize and Scope: Define strategic goals and critical assets.
- Orient the Organization: Understand internal/external context, existing practices, and compliance.
- Create a Current Profile: Assess current practices against CSF Core.
- Conduct a NIST CSF Risk Assessment: Identify, analyze, and prioritize cybersecurity risks.
- Create a Target Profile: Define desired cybersecurity outcomes based on risk appetite.
- Identify, Analyze, and Prioritize Gaps: Compare profiles to pinpoint and rank missing outcomes.
- Implement an Action Plan: Execute controls and process improvements, continuously monitoring progress.
2.2. Program Management Best Practices: Governance, Communication, and Resource Allocation
- Governance: Clear leadership (executives setting goals, managers planning, practitioners executing) and a formal structure (e.g., Cybersecurity Governance Committee) are crucial for accountability and strategic alignment.
- Communication: CSF Profiles serve as vital tools to translate technical posture into clear narratives for diverse stakeholders, fostering shared understanding and buy-in.
- Resource Allocation: Prioritize investments based on risk, leverage automation, and seek external support when internal expertise is limited.
2.3. Roles and Responsibilities: Applying the RACI Matrix
A RACI (Responsible, Accountable, Consulted, Informed) matrix clarifies roles for the 367 tasks mapped to 106 Core Desired Outcomes across typical organizational roles (e.g., Director of Information Security, CFO, Organizational Leadership). Customization to specific organizational structures is essential for clarity and accountability.
2.4. Integration with Enterprise Systems and Frameworks
NIST CSF is designed for seamless integration:
- Enterprise Risk Management (ERM): Promotes a holistic view of risk, aligning cyber risk with broader business objectives and strategic decision-making.
- Other Frameworks: Complements NIST SP 800-53/171 (detailed controls), ISO/IEC 27001 (ISMS), COBIT (IT governance), ITIL (service management), PCI DSS (cardholder data), CMMC (DoD contractors), and DevSecOps/Agile (secure software development). This reduces duplication and streamlines compliance.
3. Advanced Operationalization and Performance Measurement
Embedding the framework into daily operations requires continuous monitoring, measurement, and adaptation.
3.1. Operationalizing NIST CSF Controls
Involves integrating CSF principles into daily security operations:
- Microsegmentation: Enhances Protect and Govern functions by automating granular access controls, isolating assets, providing continuous monitoring, and accelerating incident response.
- Technical Controls: Examples include Access Control (RBAC, MFA), Data Security (encryption, DLP, backups), Platform Security (configuration management, secure SDLC), and Technology Infrastructure Resilience (avoiding single points of failure, load balancing).
3.2. Monitoring, Observability, and Telemetry (MELT) Strategies
Crucial for Detect and Respond functions:
- Security Observability Architecture: Layered approach (Edge Collection, Telemetry Transport, Central Analysis) for high-volume, real-time data processing.
- Security Observability Signals (MELT): Metrics (quantitative), Events (state changes), Logs (detailed records), and Traces (end-to-end flows) provide deep insights.
- SOC Tools: SIEM (Security Information and Event Management) for correlation/analysis and SOAR (Security Orchestration, Automation, and Response) for automated actions streamline threat detection and response.
3.3. Key Performance Indicators (KPIs) and Metrics
Quantifiable insights into program health, aligned with business goals:
- Govern: Policy review frequency, board engagement, supply chain risk assessment completion.
- Identify: Critical asset inventory coverage, vulnerability identification rate, risk assessment frequency.
- Protect: MFA adoption, training completion, sensitive data encryption, patch compliance.
- Detect: Mean Time to Detect (MTTD), anomaly detection rate, monitoring coverage.
- Respond: Mean Time to Respond (MTTR), Mean Time to Contain (MTTC), incident mitigation within SLA.
- Recover: Recovery Time Objective (RTO)/Recovery Point Objective (RPO) adherence, backup success rate.
3.4. Continuous Validation and Auditing
Ensures sustained compliance and adaptive security:
- Continuous Monitoring and Validation: Automated testing and assessments verify control effectiveness.
- Regular Audits: Comprehensive internal/external reviews identify weaknesses and assess governance.
- Gap Analysis and Remediation: Prioritize and address identified gaps.
- Documentation and Evidence: Maintain thorough records for audits.
- Post-Incident Reviews: Incorporate lessons learned for continuous improvement.
4. Strategic Planning and Future Evolution
NIST CSF adoption is a dynamic journey, requiring iterative planning and anticipation of future trends.
4.1. Strategic Planning Approaches for NIST CSF Adoption
Embrace an iterative and agile approach:
- Alignment with Business Objectives: Cybersecurity strategy must directly support organizational goals and risk tolerance.
- Iterative and Agile Security Practices: Use a “Security Deployment Lifecycle” with Profiles as “sprints” for incremental improvements, allowing for rapid adaptation and “fail fast” learning.
- Maturity Levels (Tiers) as a Roadmap: Progressing through tiers signifies increasing sophistication in risk management and integration.
- Cost-Benefit Analysis (CBA): Justify investments by demonstrating a viable decrease in cybersecurity risk.
4.2. Total Cost of Ownership (TCO) and Return on Investment (ROI)
Crucial for justifying cybersecurity expenditures:
- Total Cost of Ownership (TCO): Includes direct (hardware, software, services, staffing), indirect (business continuity, productivity, risk management, efficiency), and hidden costs (user interaction, supplier management).
- Return on Investment (ROI): Quantifies cost savings from prevented threats. Formulas like ROSI (Return on Security Investment) and ALE (Annualized Loss Expectancy) help demonstrate financial benefits. Automation can significantly reduce TCO and improve ROI.
4.3. Cybersecurity Product and Solution Selection Criteria
Select solutions aligned with CSF functions and organizational needs:
- Alignment with Functions: Products should support Govern, Identify, Protect, Detect, Respond, and Recover objectives.
- Key Features: Look for GRC platforms, asset management, attack surface management, access control, security ratings, threat intelligence, SIEM/SOAR, and cyber risk remediation management.
- General Considerations: Prioritize automation, integration with other frameworks, and external guidance when lacking in-house expertise.
4.4. Future Trends Impacting NIST CSF Adoption and Evolution
The framework is a “living document” that will continue to evolve with:
- Emerging Technologies: Increased focus on AI (AI Risk Management Framework) and IoT cybersecurity.
- Supply Chain Risk Management (SCRM): Enhanced emphasis on third-party risk (dedicated GV.SC category).
- Human-Centered Cybersecurity: Prioritizing human factors in security outcomes.
- Privacy Integration: Deeper integration of privacy considerations.
- Cybersecurity Workforce Development: Continued focus on addressing skills gaps.
- Automation and Tools: Increased reliance on advanced management and monitoring tools.
- Global Adoption: Continued international engagement and translations.
Conclusions
The “Implementation Plan – NIST CSF” blueprint highlights NIST CSF 2.0 as a strategic imperative for comprehensive cybersecurity resilience. Its outcome-driven, adaptable nature, coupled with a systematic implementation process and continuous measurement, enables organizations to effectively manage cyber risk, build a resilient digital foundation, and support strategic growth in an evolving threat landscape.
Chat for Professional Consultancy Services
