 Reading Time: 4 minutes
Reading Time: 4 minutes

Status: Final Blueprint
Author: Shahab Al Yamin Chawdhury
Organization: Principal Architect & Consultant Group
Research Date: 2024-07-29
Location: Dhaka, Bangladesh
Version: 1.0
Part I: Strategic Foundations
This document outlines a blueprint for establishing a mature purple team function within an advanced Security Operations Center (SOC). The core concept is a strategic shift from traditional, adversarial security testing to a collaborative model focused on continuous improvement and measurable cyber resilience.
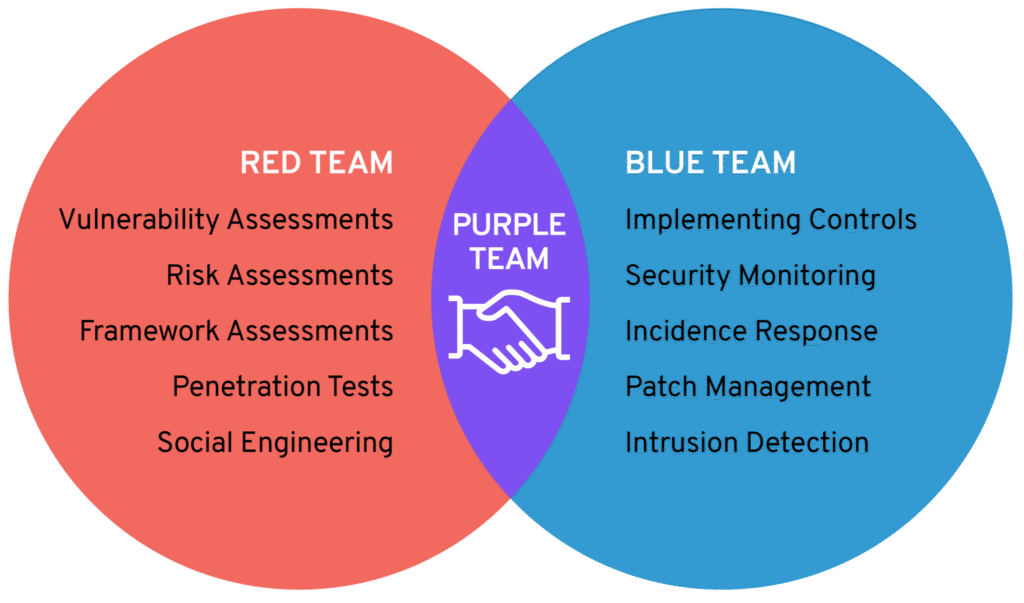
From Adversarial to Collaborative Security
The traditional security model separates offensive (Red Team) and defensive (Blue Team) functions. This creates operational silos and inefficient feedback loops. Purple teaming is not a separate team, but a collaborative function that integrates these two perspectives in real-time. The goal is not for one side to “win,” but for the entire organization to learn and enhance its collective security posture.
Table 1: Comparative Analysis of Security Teams
| Attribute | Red Team | Blue Team | Purple Team (Function) |
| Main Objective | Emulate adversaries to find vulnerabilities. | Protect, detect, and respond to threats. | Improve security posture via continuous, collaborative testing. |
| Primary Approach | Offensive, Adversarial | Defensive, Reactive & Proactive | Collaborative, Iterative |
| Feedback Loop | Delayed (post-engagement report) | Internal (continuous) | Real-time |
| Success Metric | Number of vulnerabilities found | Mean Time to Detect/Respond (MTTD/MTTR) | Quantifiable improvement in resilience |
Export to Sheets
The Business Imperative
Adopting a purple team model is a strategic business decision that delivers quantifiable value:
- Optimized ROI on Security Tools: Purple team exercises validate the actual efficacy of expensive security technologies (SIEM, EDR, etc.), ensuring they are configured correctly and delivering value.
- Measurable Resilience: It moves the security conversation from compliance checklists to data-driven metrics. By tracking improvements in MTTD and MTTR, the program demonstrates a direct reduction in the potential financial impact of a breach.
- Risk-Based Prioritization: Exercises are tailored to simulate threats most relevant to the organization’s critical assets (“crown jewels”), ensuring that defensive efforts are aligned with business priorities.
Part II: Architectural Blueprint
An effective purple team program is powered by a mature SOC architecture. This architecture is built on a foundation of people, processes, and a synergistic technology stack.
The “Technological Trinity” for Automation
The evolution from manual exercises to a continuous, automated purple team function is enabled by the integration of three core platforms:
- Threat Intelligence Platform (TIP): The strategic brain that aggregates threat data to direct the engagement. It provides intelligence on relevant adversary Tactics, Techniques, and Procedures (TTPs).
- Breach and Attack Simulation (BAS): The automated offensive engine. It continuously simulates thousands of real-world attack TTPs in a safe and controlled manner, providing a level of coverage impossible to achieve manually.
- Security Orchestration, Automation, and Response (SOAR): The automated defensive backbone. It integrates with the security stack to automate and orchestrate incident response workflows via playbooks.
This integration creates a closed-loop system: the TIP identifies a new threat, the BAS platform automatically simulates it, the SIEM/EDR detects it, the SOAR platform automates the response, and the BAS platform re-runs the simulation to validate the fix.
Part III: Operational Frameworks
Structured frameworks ensure that purple team exercises are consistent, repeatable, and produce measurable outcomes.
- Threat Intelligence-Led Penetration Testing (TLPT) Frameworks (e.g., TIBER-EU, CBEST): These are formal, prescriptive frameworks often mandated in highly regulated industries like finance. They use accredited external providers for threat intelligence and red teaming to conduct rigorous tests against an organization’s critical functions, ensuring a high degree of auditability.
- Adversary Emulation with MITRE ATT&CK: The MITRE ATT&CK framework provides a globally accessible, common language for describing adversary behaviors. This framework is used to create Adversary Emulation Plans (AEPs), which are step-by-step guides for simulating a specific threat actor (e.g., APT41, FIN7) by chaining together their known TTPs into a logical attack flow. This process makes threat intelligence tangible and actionable for testing.
Part IV: Metrics and Continuous Validation
A mature purple team program moves from discrete, episodic exercises to a continuous validation model that provides ongoing assurance of security control effectiveness.
Key Performance Indicators (KPIs)
A multi-dimensional metrics framework is essential to measure effectiveness and demonstrate value.
- Operational Metrics:
- Mean Time to Detect (MTTD): Average time from TTP execution to alert generation.
- Mean Time to Respond (MTTR): Average time from alert to threat containment.
- Efficacy Metrics:
- Detection Rate: Percentage of simulated TTPs that were successfully detected.
- Threat Resilience Score: The detection rate tracked over time against an expanding library of prioritized TTPs, providing a powerful narrative of improvement.
- Coverage Metrics:
- MITRE ATT&CK Coverage: Percentage of ATT&CK techniques for which a validated detection capability exists, often visualized as a heatmap.
These metrics are visualized in an interactive dashboard, providing clear, actionable insights for stakeholders ranging from SOC analysts to the C-suite.
Part V: Implementation Roadmap
The journey to a mature purple team program should follow a phased, crawl-walk-run methodology.
- Phase 1: Foundational (0-6 Months):
- Focus: Establish prerequisites.
- Actions: Solidify core SOC capabilities (SIEM, EDR, logging). Conduct initial manual, tabletop exercises to build a collaborative culture.
- Phase 2: Operationalizing (6-18 Months):
- Focus: Introduce automation and measurement.
- Actions: Implement a BAS platform. Develop and track a formal metrics program (MTTD, MTTR, Detection Rate).
- Phase 3: Continuous & Integrated (18-36 Months):
- Focus: Achieve a state of continuous validation.
- Actions: Integrate TIP and SOAR platforms with the BAS to create the fully automated feedback loop.
- Phase 4: Predictive & Autonomous (3+ Years):
- Focus: Position for the future.
- Actions: Explore AI-enhanced predictive threat modeling and digital twin environments for advanced, non-production testing.