 Reading Time: 5 minutes
Reading Time: 5 minutes

Status: Final Blueprint
Author: Shahab Al Yamin Chawdhury
Organization: Principal Architect & Consultant Group
Research Date: March 17, 2025
Location: Dhaka, Bangladesh
Version: 1.0
Executive Summary
This blueprint guides enterprise-scale implementation of the NIST Risk Management Framework (RMF). It provides a structured, risk-based methodology for managing information security and privacy risks, crucial in today’s threat landscape. The RMF emphasizes a continuous, six-step lifecycle: Categorize, Select, Implement, Assess, Authorize, and Monitor. This approach integrates security throughout the system development lifecycle, transforming it from a static review into an agile, continuous process. Successful RMF adoption enhances security posture, reduces cyber risks, ensures regulatory compliance, and fosters organizational resilience, turning security into a proactive business enabler.
1. Introduction: The Imperative for NIST RMF Adoption
The NIST RMF is a widely adopted, comprehensive framework for managing information security and privacy risks. Its continuous lifecycle approach embeds security into daily operations and strategic decision-making. Enterprises are driven to adopt RMF by evolving threats, stringent regulations (e.g., GDPR, HIPAA, PCI DSS), and the need to protect critical data, especially in cloud environments. This blueprint provides an actionable guide covering strategic, technical, operational, and organizational aspects for successful RMF adoption and sustainment.
2. Foundational Principles & Governance
The RMF is built on principles of enterprise-wide risk management, continuous monitoring, security integration throughout the lifecycle, and transparency. Effective governance requires establishing a risk executive function and roles like the Senior Agency Information Security Officer (SAISO), defining organizational risk appetite, and robust data governance. NIST RMF’s interoperability with other frameworks (e.g., ISO 27001, COBIT, CIS Controls) allows for synergistic compliance efforts, streamlining adherence to multiple regulatory mandates.
3. Strategic Planning & Program Design
A clear RMF program vision aligns with business goals, defining how RMF enhances security and reduces risk. A phased roadmap manages complexity, breaking implementation into stages with defined milestones and resource allocation. RMF maturity models (e.g., CMMI, NIST CSF) help assess current posture and guide continuous improvement. Agile and DevSecOps principles enable iterative development, rapid adaptation, and “security by design,” integrating security into the development pipeline.
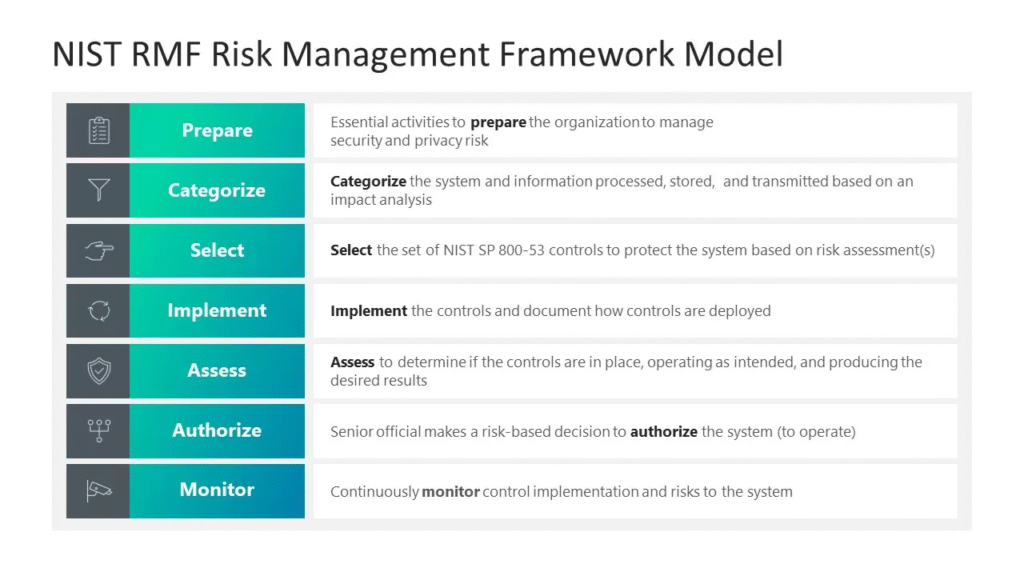
4. NIST RMF Lifecycle: Process, Functions & Activities
The RMF follows a six-step lifecycle:
- 1. Categorize: Classify information systems and data based on potential impact (low, moderate, high) to operations, assets, or individuals if compromised. This defines the required security level.
- 2. Select: Choose an initial set of security controls from NIST SP 800-53, tailoring them to the specific organizational and system context. This includes leveraging control inheritance.
- 3. Implement: Deploy selected security controls (e.g., access controls, encryption, network segmentation) and establish operational procedures. Comprehensive documentation, especially the System Security Plan (SSP), is crucial.
- 4. Assess: Rigorously evaluate control effectiveness through technical testing, vulnerability scanning, and interviews. Third-party auditors can provide independent verification.
- 5. Authorize: A designated senior official makes a risk-based decision to authorize the system for operation, issuing an Authorization to Operate (ATO) and formally accepting residual risks.
- 6. Monitor: Continuously monitor systems and controls for changes, new threats, and vulnerabilities. This enables proactive risk management, rapid response, and integrates change management.
5. Risk Management, Control Implementation & Compliance Assurance
Beyond system-specific categorization, enterprise risk analysis identifies and prioritizes risks across the organization, including supply chains and third-party vendors, integrating threat intelligence. Security controls, both technical (e.g., Zero Trust Architecture, automation) and operational (e.g., security awareness, incident handling), are designed and implemented to support effective detection and response. Robust processes for continuous compliance verification and audit readiness are paramount. Incident response and recovery plans are tightly integrated, with lessons learned feeding back into the RMF process for continuous improvement.
6. Technical Architecture, Platform & Feature Set Design
Enterprise architecture must integrate RMF principles, incorporating Zero Trust and cloud-specific controls. Selecting scalable, integrable, and user-friendly Governance, Risk, and Compliance (GRC) platforms, Security Information and Event Management (SIEM) systems, and vulnerability management tools is crucial. Key technical requirements include automated control mapping, continuous monitoring, workflow management, and comprehensive reporting. Seamless integration between RMF tools and existing security solutions, along with robust telemetry collection, creates a unified security ecosystem.
7. Operationalizing RMF: Monitoring, Support & Quality Assurance
Operationalizing RMF requires robust continuous monitoring and observability frameworks, leveraging AI/ML for anomaly detection and threat intelligence. Defining operational requirements for control maintenance, SSP updates, and continuous risk assessments ensures RMF remains effective. Rigorous Quality Assurance (QA) processes ensure accuracy and reliability of RMF activities and documentation. Clear support models and Service Level Agreements (SLAs) for security operations ensure timely resolution of RMF-related issues.
8. Organizational Readiness, Roles, Responsibilities & Skill Development
Clearly defining RMF roles (e.g., system owners, ISSOs, authorizing officials) and tasks is paramount. A comprehensive RACI (Responsible, Accountable, Consulted, Informed) matrix clarifies involvement for every RMF activity, fostering collaboration. Identifying required skills (technical, risk management, compliance) and developing comprehensive training programs for all personnel enhances cybersecurity literacy and fosters a security-aware culture. Structured organizational change management addresses resistance and ensures smooth transition to new RMF processes.
9. Performance Measurement, Maturity & Continuous Improvement
Defining measurable Key Performance Indicators (KPIs) (e.g., compliance rates, risk reduction, incident response times) is essential for tracking RMF program effectiveness. Enterprise-grade matrices aggregate KPIs for a holistic view, supporting drill-down analysis and dynamic visualization. Regular, tailored reporting communicates RMF performance to stakeholders. Formal processes for continuous improvement, including post-implementation reviews and feedback loops, ensure the RMF program remains adaptive and evolves with the changing risk landscape.
10. Financial Considerations: TCO, ROI & Investment Justification
A comprehensive Total Cost of Ownership (TCO) analysis accounts for all direct and indirect costs (software, hardware, personnel, training, consulting, operational overhead). Quantifying Return on Investment (ROI) involves articulating tangible benefits (reduced breach costs, avoided fines, operational efficiency) and intangible benefits (enhanced reputation, increased trust). Detailed budgeting and effective resource allocation ensure adequate funding and sustainability for the RMF program.
11. Challenges, Best Practices & Future Outlook
Common challenges include resource constraints, framework complexity, cultural resistance, lack of executive buy-in, and insufficient skills. Best practices include phased implementation, extensive automation, strong governance, integration with ERM/GRC, Agile RMF, DevSecOps, Zero Trust adoption, continuous monitoring, fostering a security culture, and leveraging control inheritance. The future of RMF will increasingly leverage AI/ML for enhanced threat detection and automation, with growing emphasis on supply chain security and integration with emerging technologies like blockchain and quantum-resistant cryptography.
12. Conclusion & Actionable Recommendations
NIST RMF implementation is a strategic enterprise transformation requiring robust governance, continuous security integration, and a focus on the human element. It moves organizations from reactive compliance to proactive, resilient security.
Phased Implementation Plan Summary:
- Foundation & Planning (3-6 Months): Establish governance, define vision, conduct risk analysis, initial system categorization, roadmap, and budget.
- Control Implementation (6-12 Months): Select/tailor controls, implement technical/operational controls, develop SSPs, integrate DevSecOps/Zero Trust, staff training.
- Assessment & Authorization (4-8 Months): Develop assessment plans, conduct assessments (internal/third-party), prepare SARs, formal ATO decisions.
- Continuous Monitoring & Optimization (Ongoing): Implement continuous monitoring, establish observability, automate security ops, track KPIs, conduct regular reviews, ongoing training.
Strategic Recommendations for Long-Term RMF Success:
- Foster a culture of continuous improvement.
- Invest in ongoing training and development.
- Regularly reassess RMF program alignment with business objectives.
- Embrace agility and adaptability to evolving threats.
- Leverage automation and AI for efficiency and enhanced capabilities.
- Strengthen third-party risk management.
Chat for Professional Consultancy Services
