 Reading Time: 5 minutes
Reading Time: 5 minutes

Status: Final Blueprint
Author: Shahab Al Yamin Chawdhury
Organization: Principal Architect & Consultant Group
Research Date: August 7, 2024
Location: Dhaka, Bangladesh
Version: 1.0
Executive Summary
This playbook provides a comprehensive, structured framework for managing enterprise applications as strategic business enablers. It moves beyond treating applications as mere IT assets and reframes them as the digital manifestation of business capabilities. The blueprint is segmented into five core parts: establishing a strategic foundation, mastering the application portfolio, engineering a high-velocity delivery engine, ensuring operational excellence, and enabling the entire function through robust organizational and financial structures. By implementing the principles, frameworks, and processes outlined, an enterprise can transform its application management function from a reactive cost center into a proactive, value-driven partner that accelerates business ambition.
Part I: The Strategic Foundation
This section establishes the strategic alignment between the application portfolio and enterprise objectives.
- Chapter 1: Defining the Enterprise Application Charter: Treat applications as strategic business enablers, not just IT assets. Craft a clear vision, mission, and set of core principles (e.g., business value-driven, secure-by-design) to guide all decisions. Explicitly link application strategy to enterprise goals to ensure IT investments deliver maximum impact.
- Chapter 2: The Integrated Governance and Compliance Framework: Implement a single, integrated governance framework by leveraging the strengths of global standards. Use COBIT 2019 for overarching governance and control objectives, ITIL 4 for service management processes and value delivery, and TOGAF for enterprise architecture coherence. This structure ensures compliance with regulations like SOX and GDPR by design.
- Chapter 3: Enterprise Risk and Security Posture: Adopt a proactive risk management approach using the NIST Risk Management Framework (RMF), a seven-step process for identifying, assessing, and monitoring risks. Define the enterprise’s risk appetite to focus resources on the most critical assets and integrate security into the core governance structure, making it a shared responsibility (DevSecOps).
Part II: The Portfolio Command Center
This section focuses on gaining mastery over the entire application landscape through data-driven portfolio management.
- Chapter 4: Building the Application Inventory: Establish a single source of truth for all applications to combat redundant spending and security risks from “shadow IT”. Use a combination of top-down (financial records) and bottom-up (discovery tools, surveys) methods to compile a comprehensive inventory, enriching it with critical data attributes like business capability alignment, ownership, and cost.
- Chapter 5: Application Value and Cost Analysis: Calculate the Total Cost of Ownership (TCO) for each application to understand its full financial impact. Measure business value through a standardized framework assessing strategic alignment, operational efficiency, and user satisfaction. Visualize the portfolio on a Value-Cost Matrix to identify “Crown Jewels” and “Divestment Candidates.”
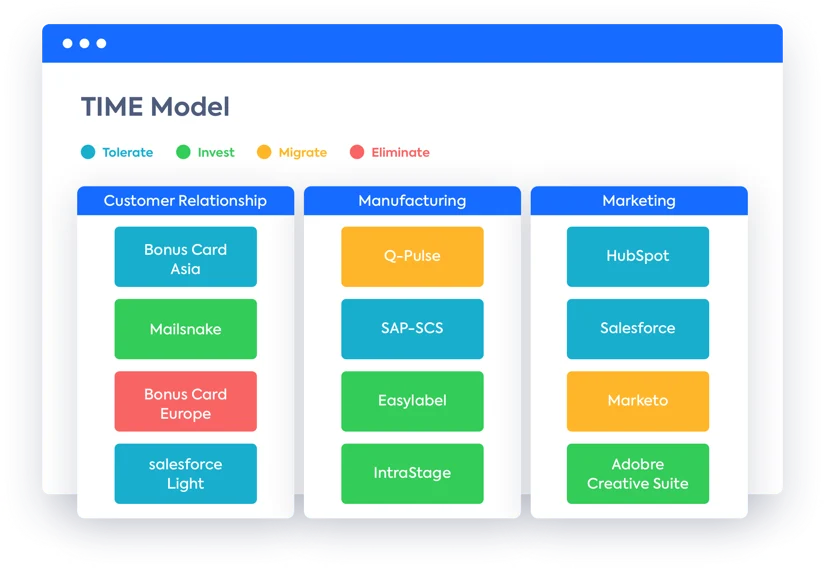
- Chapter 6: Application Rationalization and Modernization: Establish application rationalization as a continuous discipline, not a one-time project. Use the Gartner TIME model (Tolerate, Invest, Migrate, Eliminate) to categorize applications based on their technical fit and business value. For applications in the “Migrate” quadrant, apply the 7 Rs of Modernization (e.g., Rehost, Replatform, Refactor) to select the most appropriate strategy.
- Chapter 7: The Enterprise Application Roadmap: Translate portfolio analysis into a high-level, visual roadmap that communicates the strategic evolution of the application landscape over a 1-3 year horizon. This living document should be developed collaboratively with stakeholders and be tightly aligned with the enterprise’s budget and capacity planning cycles to ensure it is an executable reality.
Part III: The Delivery Engine
This section details the frameworks for building and deploying applications with both speed and quality.
- Chapter 8: The Modern Application Lifecycle (ALM): Integrate Agile, DevOps, and DevSecOps to create a high-velocity delivery engine. Implement best practices at each stage—Plan, Develop, Test, Deploy, Maintain—with a “shift-left” security approach that embeds security from the start. Establish clear governance for low-code/no-code environments to mitigate risks.
- Chapter 9: Architecture and Design Standards: Empower Application Architects to define and enforce standards, ensuring solutions are consistent with the enterprise architecture (TOGAF). Establish a library of reference architectures and design patterns to accelerate development. Implement an API-led strategy for Enterprise Application Integration (EAI) to avoid “spaghetti architecture”.
- Chapter 10: Quality Assurance and Reliability Engineering: Build a modern QA program that emphasizes continuous, automated testing integrated into the CI/CD pipeline. Introduce Site Reliability Engineering (SRE) principles, using data-driven Service Level Objectives (SLOs) and Error Budgets to balance feature development with reliability work.
- Chapter 11: The CI/CD and Deployment Pipeline: Architect a secure CI/CD toolchain that automates builds, testing, and deployments while protecting against attacks. Measure delivery performance using the four key DORA metrics: Deployment Frequency, Lead Time for Changes, Change Failure Rate, and Mean Time to Recovery.
Part IV: The Operations Nexus
This section covers the practices for ensuring applications are performant, reliable, and well-supported in production.
- Chapter 12: The Service Management and Support Model: Implement ITIL-aligned processes for Incident, Problem, and Change Management. Define a tiered support structure (L1, L2, L3) to handle issues efficiently and provide clear escalation paths. Manage expectations with formal Service Level Agreements (SLAs) and internal SLOs.
- Chapter 13: Advanced Monitoring, Observability, and AIOps: Evolve from traditional monitoring to observability to debug “unknown unknowns” in complex systems. Build this capability on the three pillars of telemetry: Metrics, Logs, and Traces. Leverage AIOps platforms to apply machine learning for proactive insights, anomaly detection, and automated remediation.
- Chapter 14: Performance, Scalability, and Resilience: Set clear performance objectives (SLOs) and integrate continuous performance testing into the CI/CD pipeline. Design applications for horizontal scaling and validate their limits with scalability testing. Build resilience by adopting Chaos Engineering—the practice of intentionally injecting controlled failures to proactively identify and fix weaknesses.
Part V: The Enablement Core
This section outlines the organizational, financial, and measurement structures that support the entire application management function.
- Chapter 15: Organizational Design and Roles: Structure the application management function using a hybrid or Center of Excellence (CoE) model to balance central governance with business-aligned agility. Define key roles and use a RACI matrix (Responsible, Accountable, Consulted, Informed) to clarify responsibilities for critical processes.
- Chapter 16: Stakeholder Management and Application Literacy: Implement a structured framework for stakeholder engagement to manage expectations and communicate value effectively. Foster enterprise-wide application literacy through training and super-user programs to maximize the ROI on technology investments.
- Chapter 17: Financial Management and FinOps: Align the application budget directly with the strategic roadmap and TCO analysis. Adopt FinOps principles for cloud applications to instill a culture of cost accountability and optimize cloud spend for business value. Use showback or chargeback models to manage the cost of shared services transparently.
- Chapter 18: The Performance Measurement Body of Knowledge: Establish a master catalog of KPIs and metrics to enable data-driven decision-making across all functions. Use a CMMI-based maturity model to assess and benchmark process maturity, guiding a journey from reactive firefighting to continuous optimization. Institute an annual renewal and reflection cycle to ensure the playbook remains a living, evolving guide for delivering enterprise value.