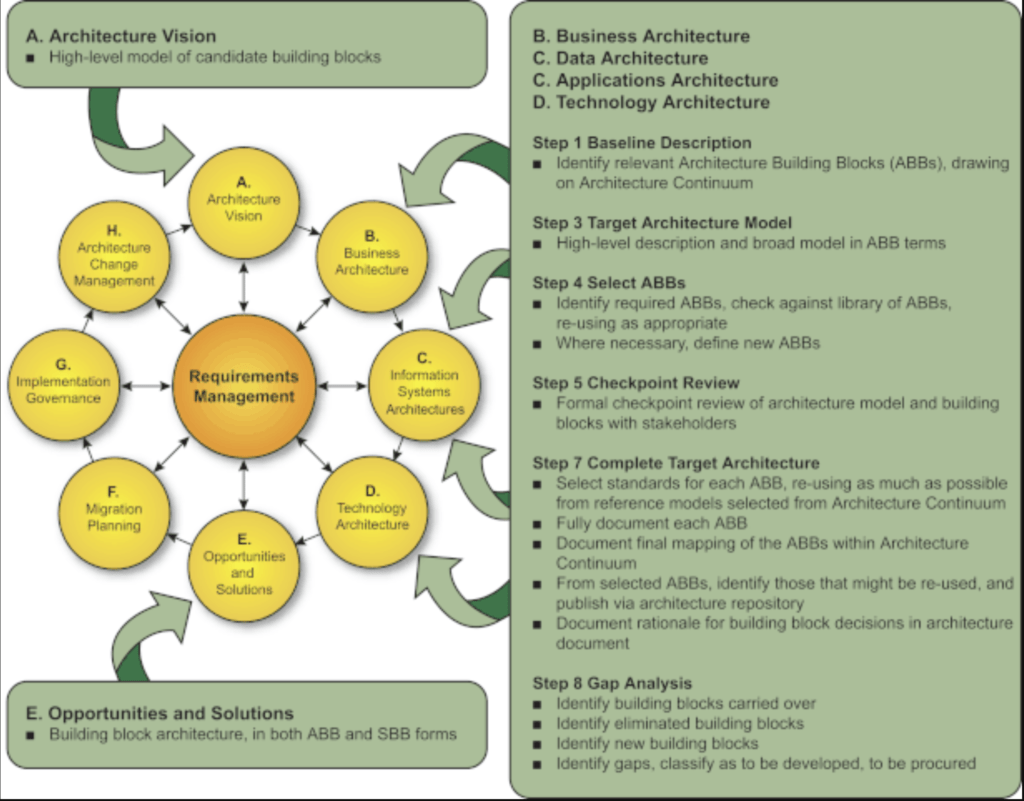
In the context of enterprise architecture, Architecture Building Blocks (ABBs) and Solution Building Blocks (SBBs) are key concepts used in the TOGAF Architecture Development Method (ADM) for designing and implementing systems.
Source: Building Blocks (opengroup.org)
ABBs are packages of functionality defined to meet the business needs across an organization. They are typically more abstract and are used during the early stages of the architecture development process.
SBBs, on the other hand, are more concrete and are used during the later stages of the architecture development process. They are product-specific forms of ABBs.
The mapping between ABBs and SBBs is crucial for ensuring that the implemented solution aligns with the architectural vision and meets the business needs. This mapping process also involves aligning with operational policies for data protection and compliance.
In terms of security, both ABBs and SBBs play important roles:
ABBs might define the overall security architecture and policies at a high level. SBBs would then implement these policies in a specific technology or product. For example, an SBB might implement secure data transmission using HTTPS. Note that the mapping from the SBBs to the IT topology and operational policies should include specifications of attributes shared across the environment, such as security. This ensures that the security requirements are consistently applied across all components of the system. The mapping of ABBs and SBBs is a critical step in the architecture development process, particularly in ensuring that security requirements are effectively addressed. It helps in achieving a balance between the high-level architectural vision and the practical implementation of the system.
Ensure security alignment between ABBs and SBBs?
Ensuring security alignment between Architecture Building Blocks (ABBs) and Solution Building Blocks (SBBs) is a critical aspect of the architecture development process. Here are some steps you can follow:
Define Security Requirements in ABBs: Start by defining the security requirements at a high level in your ABBs. This could include policies, standards, and guidelines that your organization needs to adhere to.
Implement Security in SBBs: The SBBs should then implement these security requirements. This could be in the form of specific technologies, products, or configurations.
Ensure Consistency: Make sure that the security attributes are consistently applied across all components of the system. This can be achieved by specifying attributes shared across the environment, such as security.
Review and Update: Regularly review and update your ABBs and SBBs to ensure they continue to meet your organization’s evolving security needs. This includes considering implementation and usage, and evolving to exploit technology and standards.
Publish Interfaces: Most building blocks have to interoperate with other building blocks. Wherever that is true, it is important that the interfaces to a building block are published and reasonably stable.
Loosely Coupled: A building block’s boundary and specification should be loosely coupled to its implementation; i.e., it should be possible to realize a building block in several different ways without impacting the boundary or specification of the building block.
Remember, the goal is to ensure that the implemented solution aligns with the architectural vision and meets the business needs, including security requirements. This process also involves aligning with operational policies for data protection and compliance, and also can be mapped to OSS (Operation Support System) & BSS (Billing & Settlement System).