 Reading Time: 3 minutes
Reading Time: 3 minutes

Status: Final Blueprint
Author: Shahab Al Yamin Chawdhury
Organization: Principal Architect & Consultant Group
Research Date: July 2, 2024
Location: Dhaka, Bangladesh
Version: 1.0
Executive Summary: Moving Beyond CVSS
Modern enterprises are overwhelmed by a “prioritization paradox,” where a flood of ‘Critical’ vulnerability alerts from systems like the Common Vulnerability Scoring System (CVSS) makes effective prioritization impossible. The reliance on CVSS’s static, technical severity scores creates a dangerous disconnect between remediation efforts and genuine business risk reduction.
This document outlines a blueprint for a Risk-Based Vulnerability Management (RBVM) program centered on the Unified Risk Score (URS). The URS is a transparent, customizable metric that provides a holistic view of risk by synthesizing three critical dimensions:
- Intrinsic Severity (CVSS): The inherent technical danger of the vulnerability.
- Threat Likelihood (EPSS): The real-world probability of exploitation, based on data-driven models and threat intelligence.
- Business Impact (ACR): The potential consequence of a compromise, based on the affected asset’s criticality to the business.
By adopting the URS, organizations can move from a reactive patching cycle to a proactive, data-driven risk management strategy. This allows for defensible prioritization, meaningful remediation timelines (SLAs), and the optimization of security resources on the threats that truly matter.
The Unified Risk Score (URS) Framework
The URS model is built on a “glass-box” architecture, combining open standards and internal business context into a single, actionable score.
The Three Pillars of Risk
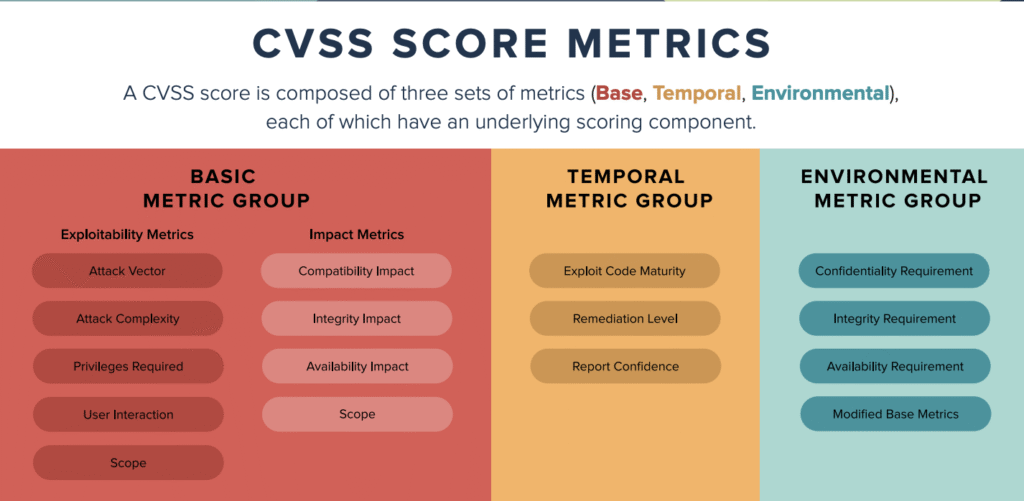
- Severity (CVSS): We use the CVSS score as the baseline for a vulnerability’s technical severity. It answers the question: “How bad could this be in a worst-case scenario?” However, this is only the starting point.
- Threat (EPSS & Threat Intelligence): We integrate the Exploit Prediction Scoring System (EPSS) to determine the real-world likelihood of a vulnerability being exploited. This score is enriched with high-fidelity intelligence, such as CISA’s Known Exploited Vulnerabilities (KEV) catalog, to answer the question: “Is anyone actually using this exploit?”
- Impact (Asset Criticality Rating – ACR): This is the most crucial component. Through a Business Impact Analysis (BIA) and a formal asset management process, we assign a criticality rating to each asset. This answers the question: “If this asset is compromised, how much will it hurt the business?”
The Core URS Formula
The URS is calculated using a transparent, weighted formula that can be tuned to an organization’s specific risk appetite. A typical implementation, producing a score from 0-1000, is:URS=((Norm_CVSS×Wsev)+(Norm_Threat×Wthreat)+(Norm_Impact×Wimpact))×1000
- Weights (W): The sum of weights must equal 1 (e.g., Severity=0.2, Threat=0.4, Impact=0.4).
- Normalization: All input scores (CVSS, EPSS, ACR) are normalized to a 0.0 to 1.0 scale before calculation.
This formula allows for clear, defensible prioritization. A “Critical” CVSS vulnerability with no active threat on a non-critical asset will receive a low URS, while a “Medium” CVSS vulnerability with a known exploit on a crown jewel asset will be correctly elevated to a high-priority risk.
From Score to Action
A risk score is only valuable if it drives action. The URS is the engine for a dynamic and efficient remediation process.
Risk Tiers & Remediation SLAs
The 0-1000 URS is mapped to intuitive risk tiers, each with a corresponding Service Level Agreement (SLA) for remediation. This creates a clear, auditable policy for action.
| Risk Tier | URS Range | Remediation SLA |
| Critical | 900 – 1000 | 15 Days |
| High | 700 – 899 | 30 Days |
| Medium | 400 – 699 | 60 Days |
| Low | 0 – 399 | 90 Days or Risk Acceptance |
This structure ensures that the most significant risks are addressed with the greatest urgency, backed by a data-driven justification that fosters buy-in from IT and business stakeholders.
The Command Center Dashboard
The entire framework is operationalized through an interactive, role-based dashboard that serves as the central command center for vulnerability management. It provides:
- CISO View: High-level strategic KPIs, including overall enterprise risk trends and SLA compliance.
- Manager View: Operational metrics like Mean Time to Remediate (MTTR) and vulnerability aging profiles.
- Analyst View: A tactical, prioritized queue of vulnerabilities ranked by URS, with direct drill-downs into the calculation, asset context, and threat intelligence for each finding.
Conclusion
By replacing the outdated reliance on CVSS alone with the multi-dimensional Unified Risk Score, organizations can cut through the noise of vulnerability alerts. This blueprint provides an actionable plan to build a more efficient, effective, and business-aligned vulnerability management program that demonstrably reduces risk and strengthens the enterprise’s overall security posture.