 Reading Time: 3 minutes
Reading Time: 3 minutes

The Shift: From Siloed Posture Tools to Unified Exposure Management
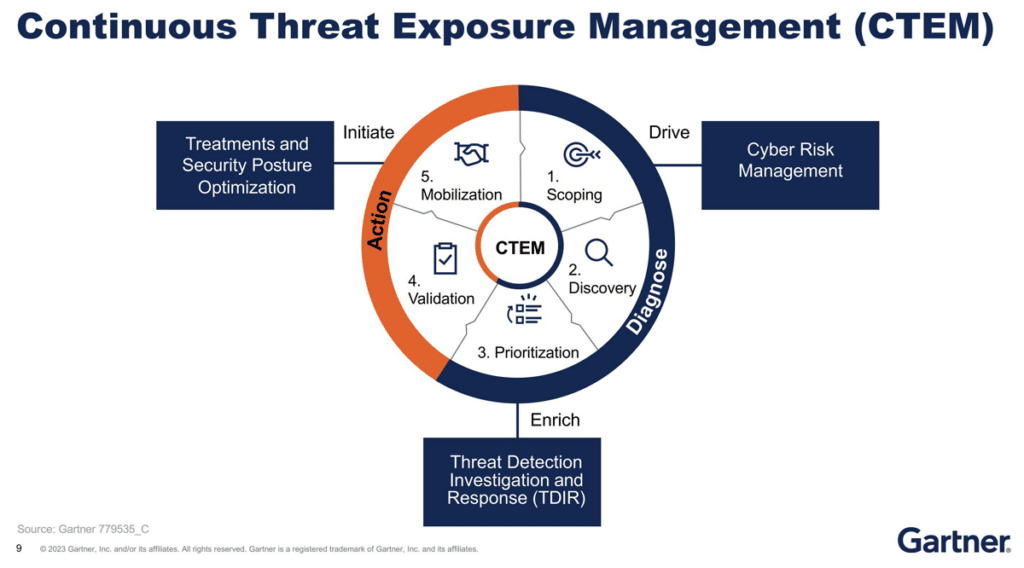
For years, security teams have relied on separate tools to manage cloud misconfigurations (CSPM), Kubernetes security (KSPM), and sensitive data exposure (DSPM). Meanwhile, Continuous Threat Exposure Management (CTEM) emerged as a programmatic approach to continuously identify, assess, and remediate exposures across the attack surface.
Now, these once‑distinct domains are converging into unified risk dashboards — platforms that consolidate posture, threat, and exposure data into a single operational and executive view. This shift is not just a tooling trend; it’s a structural change in how organizations measure and reduce cyber risk.
Why Convergence Is Happening
Three forces are driving this consolidation:
- Attack Surface Complexity
Hybrid and multi‑cloud environments, containerized workloads, SaaS sprawl, and distributed data stores have blurred the boundaries between infrastructure, workloads, and data. - Operational Inefficiency
Running separate CSPM, KSPM, and DSPM tools creates overlapping alerts, inconsistent scoring, and fragmented remediation workflows. - CTEM Alignment
Gartner’s CTEM framework emphasizes continuous, prioritized exposure reduction. Unified dashboards make it possible to operationalize CTEM across all asset classes.
The Core Components
CSPM — Cloud Security Posture Management
- Focus: Misconfigurations, compliance drift, and excessive permissions in cloud services (AWS, Azure, GCP).
- Key Metrics: CIS benchmark compliance, IAM privilege scores, public exposure counts.
KSPM — Kubernetes Security Posture Management
- Focus: Cluster configuration, RBAC controls, workload isolation, and runtime drift.
- Key Metrics: Pod security policy adherence, namespace isolation, image vulnerability counts.
DSPM — Data Security Posture Management
- Focus: Discovery, classification, and access control for sensitive data across cloud, SaaS, and on‑prem.
- Key Metrics: Sensitive data location maps, overexposed datasets, stale access permissions.
CTEM — Continuous Threat Exposure Management
- Focus: Continuous, prioritized exposure reduction across the entire attack surface.
- Key Metrics: Exposure severity index, remediation SLA adherence, attack path closure rates.
What a Unified Risk Dashboard Delivers
When these capabilities converge, the SOC and risk teams gain:
- Single Source of Truth — All posture and exposure data in one place, eliminating context switching.
- Cross‑Domain Correlation — Linking a misconfigured Kubernetes ingress to an exposed dataset in the same namespace, or tying cloud IAM drift to exploitable attack paths.
- Prioritized Remediation — AI‑driven scoring that factors in exploitability, business impact, and compliance requirements.
- Executive‑Ready Metrics — Translating technical exposure data into board‑level risk language and ROI models.
Example: From Siloed Alerts to Actionable Risk
Before convergence:
- CSPM flags an open S3 bucket.
- DSPM separately flags sensitive data in that bucket.
- KSPM has no visibility into the bucket but flags a vulnerable container image in the same workload chain.
- Analysts must manually stitch these findings together.
After convergence:
- Unified dashboard correlates all three findings into a single “High‑Impact Exposure” card.
- CTEM workflow assigns remediation tasks in priority order, with SLA tracking and automated verification.
Implementation Considerations
- Integration Strategy
- Choose platforms that natively integrate CSPM, KSPM, DSPM, and CTEM workflows, or use APIs to connect best‑of‑breed tools.
- Data Normalization
- Standardize severity scoring and asset identifiers to enable cross‑domain correlation.
- Automation & Orchestration
- Use SOAR or workflow automation to trigger remediation directly from the unified dashboard.
- Role‑Based Views
- Analysts need granular technical detail; executives need aggregated risk trends and business impact.
Benefits Beyond the SOC
- Compliance Efficiency — Unified evidence collection for audits across multiple frameworks (CIS, NIST, ISO, PCI DSS).
- Faster MTTD/MTTR — Reduced investigation time through correlated, context‑rich alerts.
- Strategic Risk Reduction — Ability to measure exposure reduction over time and tie it to business outcomes.
The Road Ahead
The convergence of CSPM, KSPM, DSPM, and CTEM into unified dashboards is not a passing trend — it’s the operational model for modern exposure management. As attack surfaces expand and AI‑driven threats accelerate, organizations will need real‑time, correlated, and prioritized visibility to stay ahead.
The winners will be those who collapse silos, normalize data, and operationalize CTEM across all asset classes — turning exposure management from a reactive chore into a proactive, measurable business enabler.
Chat for Professional Consultancy Services

FREE Consultation – 30 Minutes
