 Reading Time: 3 minutes
Reading Time: 3 minutes

Status: Final Blueprint
Author: Shahab Al Yamin Chawdhury
Organization: Principal Architect & Consultant Group
Research Date: June 3, 2025
Location: Dhaka, Bangladesh
Version: 1.0
This document provides a condensed overview of the DREAD Threat Modeling blueprint, an enterprise-grade framework for integrating proactive security into the development lifecycle.
Part 1: Principles and Framework
1.1 The DREAD+ Framework
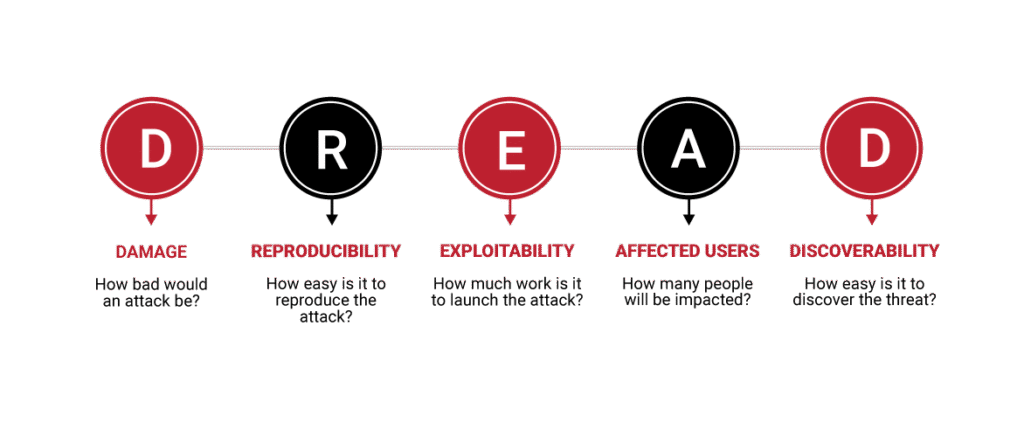
The core of the blueprint is a modernized DREAD+ framework, which addresses the historical subjectivity of the original DREAD model. It provides a standardized, semi-quantitative method for prioritizing threats.
The five pillars of DREAD+ are:
- Damage Potential: The magnitude of harm from a successful attack.
- Reproducibility: How easily an attack can be replicated.
- Exploitability: The skill and resources required to launch an attack.
- Affected Users: The scale and type of the user base impacted.
- Discoverability: How easily an attacker can find the vulnerability (defaults to maximum score to avoid “security through obscurity”).
Threats are scored from 10-50 and categorized into Critical, High, Medium, or Low risk levels, each with a required action.
1.2 Comparative Analysis
DREAD+ is a risk prioritization tool. It works best within a toolkit of other methodologies:
- STRIDE: Used for threat identification (what can go wrong?).
- PASTA: Used for deep, business-impact-focused analysis.
- OCTAVE: Used for organizational and operational risk management.
- CVSS: Used for scoring specific, known vulnerabilities (CVEs), not design flaws.
Workflow: Use STRIDE to identify threats, then DREAD+ to prioritize them for mitigation.
Part 2: Governance and Program Management
2.1 Threat Modeling Program Office (TMPO)
A central TMPO is established to ensure consistency, quality, and strategic alignment. Its mandate includes:
- Standardizing the DREAD+ methodology.
- Governing threat modeling tools and platforms.
- Developing and managing training, including a Security Champions program.
- Providing quality assurance and oversight.
- Measuring and reporting on program success using KPIs.
2.2 Roles, Responsibilities, and Lifecycle
- RACI Matrix: A detailed Responsibility Assignment Matrix (RACI) clarifies the roles of Product Owners, Architects, Developers, Security Champions, and the TMPO across the threat modeling process.
- Threat Model Lifecycle: Threat models are living documents managed through four stages:
- Creation: During the initial design phase.
- Validation: Formal review and baselining.
- Maintenance: Updated based on system changes or periodic reviews.
- Retirement: Archived when a system is decommissioned.
2.3 Measuring Success
The program’s value is demonstrated through a mix of activity and outcome-based KPIs, including:
- Coverage: Percentage of critical applications with up-to-date threat models.
- Effectiveness: Rate of design flaws found via threat modeling vs. later in the SDLC.
- Efficiency: Mean time to complete and remediate threats from a threat model.
- Business Impact: Year-over-year reduction in security incidents caused by design flaws.
A Threat Modeling Maturity Model (TMMM) is used to assess and guide continuous improvement across process, integration, scope, tooling, and culture.
Part 3: Operationalizing Threat Modeling
3.1 SDLC Integration
Threat modeling is embedded into each phase of the Secure Development Lifecycle (SDLC):
- Requirements: Define high-level security requirements.
- Design: Conduct the core threat modeling workshop (DFD, STRIDE, DREAD+).
- Implementation: Developers implement security controls defined in the model.
- Testing: QA uses the threat model to create abuse cases and validate mitigations.
- Maintenance: The threat model is updated as part of any change control process.
3.2 Agile and DevOps Integration
For modern workflows, a “little and often” approach is used:
- Agile Ceremonies: Lightweight threat modeling is integrated into backlog refinement, sprint planning, and retrospectives. Security requirements become acceptance criteria for user stories.
- Threat Modeling as Code (TMasC): The most mature state. The system architecture is defined in a version-controlled file (e.g., YAML). Automated scripts analyze this file in the CI/CD pipeline, identifying threats and potentially failing builds if new critical risks are introduced.
Part 4: Risk, Compliance, and Business Value
4.1 From Technical Threats to Business Risk
DREAD+ scores are used to triage which threats warrant a full quantitative risk analysis using a framework like Factor Analysis of Information Risk (FAIR). This translates technical ratings into financial terms (e.g., Annualized Loss Expectancy), making the risk understandable to business leaders.
4.2 Compliance and Control Mapping
Threat modeling activities and artifacts provide auditable evidence for compliance with regulations and standards like PCI DSS, HIPAA, GDPR, and the NIST Cybersecurity Framework. For example, Data Flow Diagrams (DFDs) help satisfy requirements for mapping data flows.
4.3 TCO and ROI
The program’s financial value is demonstrated by calculating its Total Cost of Ownership (TCO) and Return on Investment (ROI).
- TCO: Includes all personnel, tooling, and training costs.
- ROI: Calculated by measuring the reduction in financial risk (avoided losses) against the program’s TCO. This provides a clear, defensible justification for the program’s budget and strategic importance.
Chat for Professional Consultancy Services
