What is a Technology Blueprint?
A technology blueprint serves as a comprehensive plan that details the technology infrastructure, including hardware, software, networks, and data management systems. It aligns technology initiatives with business objectives, ensuring that IT investments contribute to growth and scalability. Key components of a technology blueprint include:
- Technology Infrastructure Plan: Outlines the physical and virtual resources needed to support business operations, including decisions on cloud vs. on-premise solutions and hardware requirements.
- Software and Application Strategy: Determines the necessary software solutions for business operations, considering scalability and integration capabilities.
- Data Management and Security: Establishes protocols for data storage, backup, recovery, and cybersecurity measures to protect sensitive information.
- IT Governance and Policies: Develops policies for IT usage, including user access controls and incident response plans.
Benefits of a Technology Blueprint
- Strategic Alignment: Ensures that IT efforts align with the organization’s long-term vision and business objectives.
- Cost Management: Helps in budgeting and avoiding unnecessary IT expenditures by providing a clear roadmap for technology investments.
- Risk Mitigation: Identifies potential IT-related risks and outlines strategies to mitigate them, enhancing overall operational effectiveness.
- Streamlined Decision-Making: Facilitates collaboration among teams, allowing for more efficient project execution and better customer outcomes.
Creating a Technology Blueprint
To create an effective technology blueprint, consider the following steps:
- Conduct a SWOT Analysis: Identify strengths, weaknesses, opportunities, and threats to understand the current technology landscape and future needs.
- Define Goals and Objectives: Clearly outline what you want to achieve with your technology investments, ensuring they align with business goals.
- Engage Stakeholders: Involve key stakeholders in the planning process to gather insights and ensure buy-in for the technology strategy.
- Iterate and Adapt: Be prepared to adjust the blueprint as business needs evolve and new technologies emerge, ensuring it remains relevant and effective.
By developing a well-structured technology blueprint, organizations can navigate the complexities of technological integration and digital transformation, ultimately leading to improved efficiency and competitive advantage.
These interactive single page application is designed as a strategic dashboard for CIOs, CISO’s, CDOs, CTO’s and business leaders. Instead of a static document, it provides an interactive experience to explore the relevant framework, understand its value, and see a clear path for adoption. You’ll be able to filter through capabilities, visualize the adoption journey, and compare the framework against other standards, all within a clean, responsive interface.
Please be mindful, there is no one size fit all solution, every organization presents a unique situation, a unique work environment, a unique organogram, a unique technology stack, therefore, you should plan accordingly and engage a Principal Architect to do the heavy lifting for you, or you are free to do it yourself.
Strategic leaders must shift from static, compliance-driven security to an agile, AI-risk-intelligence posture that continuously evolves alongside adversarial capabilities.
Chat for Professional Consultancy Services

FREE Consultation – 30 Minutes

Click on the relevant blueprints to know more:
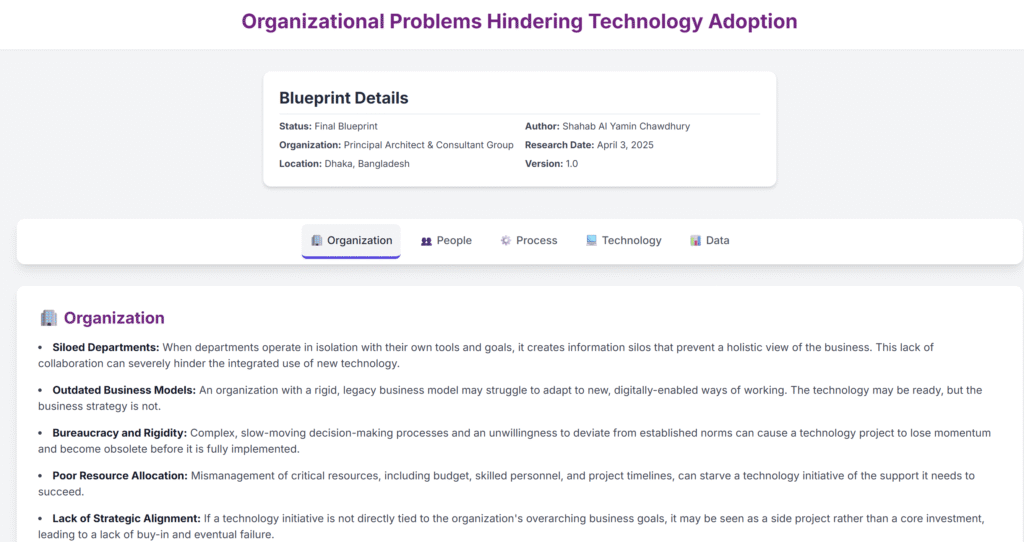
40. Organizational Problems Hindering Technology Adoption
________________________________________________________________________________________________________________________
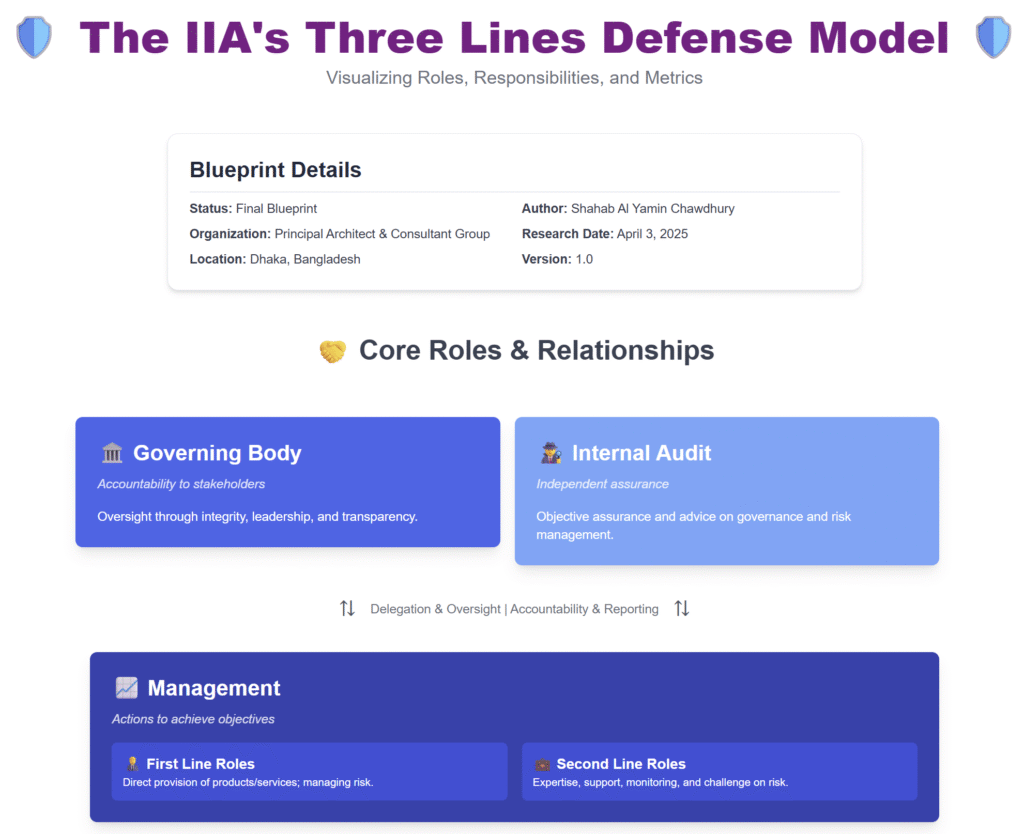
39. The IIA’s Three Lines Defense Model
________________________________________________________________________________________________________________________
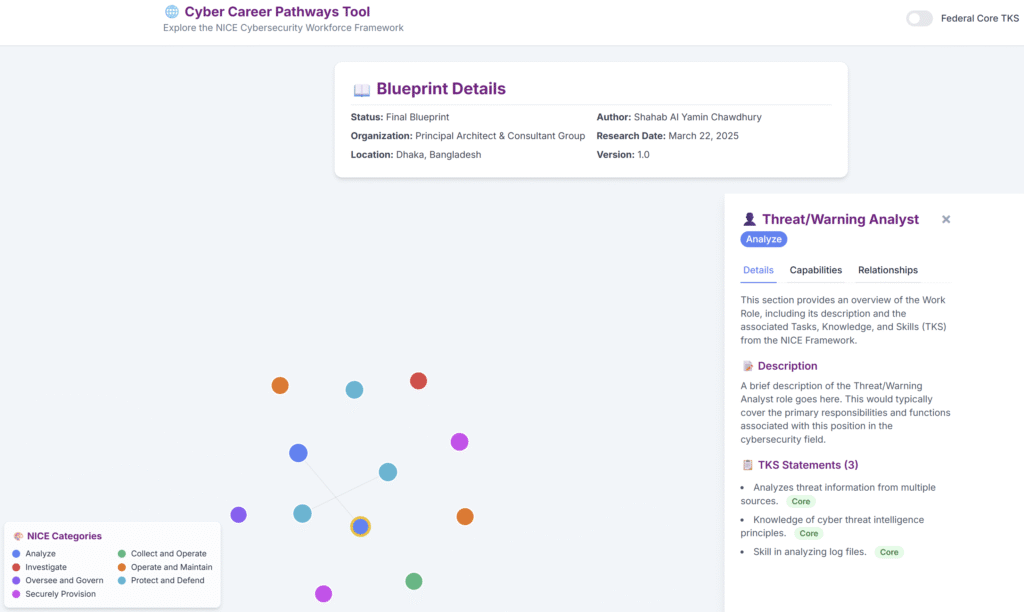
38. Cyber Career Pathways Tool
________________________________________________________________________________________________________________________

________________________________________________________________________________________________________________________
36. Agile Approach for a Successful Transformation

_________________________________________________________________________________________________________________________
35. Control of Compliance Improvement

_________________________________________________________________________________________________________________________
34. Develop AIOps to Improve IT Operations

_________________________________________________________________________________________________________________________
33. IT Operations & Service Management Strategy

_________________________________________________________________________________________________________________________
32. IT Risk Management Program

_________________________________________________________________________________________________________________________
31. Business Goals and Capabilities for Your IT Strategy

_________________________________________________________________________________________________________________________

_________________________________________________________________________________________________________________________
29. Project Portfolio Management

_________________________________________________________________________________________________________________________
28. Autonomous Enterprise Data Strategy

_________________________________________________________________________________________________________________________

_________________________________________________________________________________________________________________________

_________________________________________________________________________________________________________________________
25. Establish a Data Governance Plan

_________________________________________________________________________________________________________________________
24. EA (Enterprise Architecture) with Connected Tool

_________________________________________________________________________________________________________________________
23. Business Aligned IT Strategy

_________________________________________________________________________________________________________________________
22. Service Desk Standardization

_________________________________________________________________________________________________________________________
21. IT Business Operating Model

_________________________________________________________________________________________________________________________
20. Cybersecurity Program Development

_________________________________________________________________________________________________________________________
19. Architectural Design Assistance Plan

_________________________________________________________________________________________________________________________

_________________________________________________________________________________________________________________________

_________________________________________________________________________________________________________________________

_________________________________________________________________________________________________________________________
15. Enhancing Data Resilience in the SaaS Era

_________________________________________________________________________________________________________________________
14. IT Problem Management Process

_________________________________________________________________________________________________________________________

_________________________________________________________________________________________________________________________
12. SIEM & SOAR Better Together

_________________________________________________________________________________________________________________________
11. The Evolving Landscape of XDR
_________________________________________________________________________________________________________________________
10. Effective Multicloud Security

_________________________________________________________________________________________________________________________
9. Securing the Workplace with Zero Trust

_________________________________________________________________________________________________________________________
8. Modernize Your Security with Zero Trust

_________________________________________________________________________________________________________________________
7. ERP System

_________________________________________________________________________________________________________________________
____________________________________________________________
____________________________________________________________
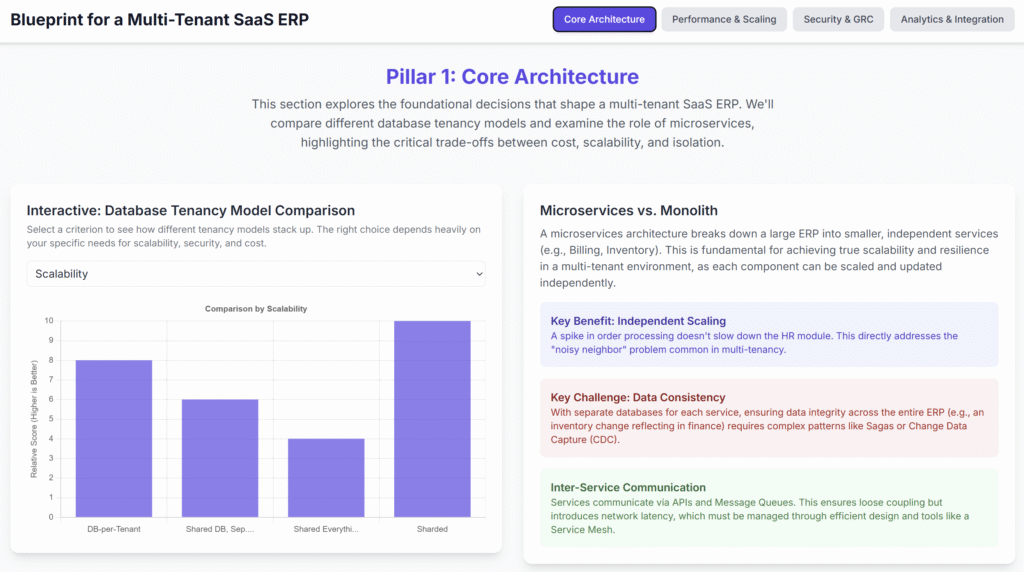
____________________________________________________________
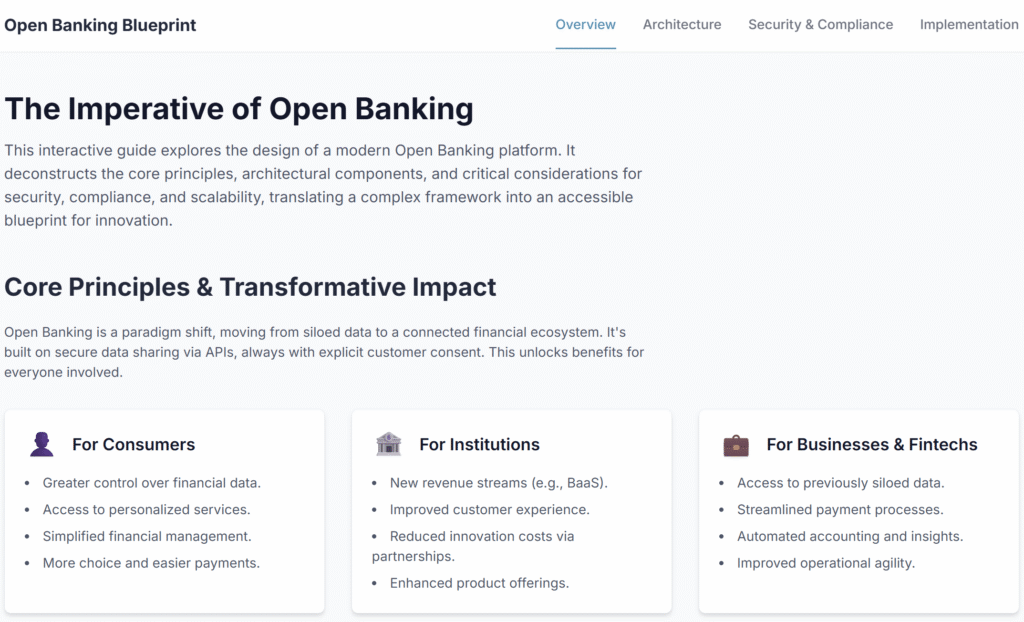
3. Designing an Open Banking Platform
____________________________________________________________
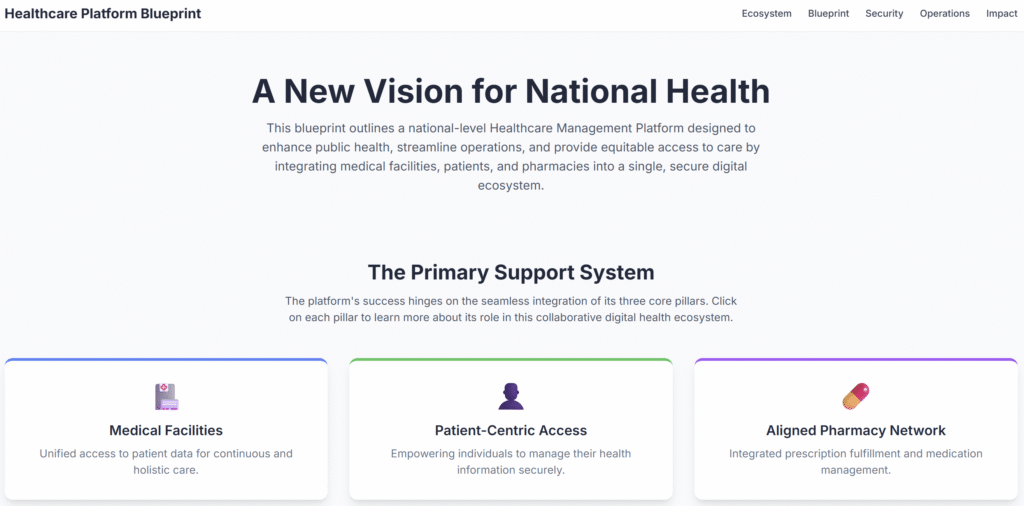
2. National Healthcare Management Platform
____________________________________________________________